JS.Crypto (Ransom32) is First JavaScript-Based Ransomware with Ability to Infect Multiple Operating Systems
 We know all-to-well how relentless cybercrooks and hackers are when it comes to them concocting the latest and most aggressive forms of malware. Each and every day a plethora of new malware threats are created, some are harmless annoyances while others are destructive monsters that devour files on an infected computer.
We know all-to-well how relentless cybercrooks and hackers are when it comes to them concocting the latest and most aggressive forms of malware. Each and every day a plethora of new malware threats are created, some are harmless annoyances while others are destructive monsters that devour files on an infected computer.
In the latest efforts of cybercrooks and hackers, they have conjured up a nasty ransomware threat that is the first of its kind, one that utilizes JavaScript frame work, which enables it to infect Windows, Mac and Linux systems. The threat dubbed as JS.Crypto Ransomware or Ransom32, is currently being sold on the dark web as a ransomware-as-a-service. The deal offered by those that spread the new ransomware threat is offered in exchange for a 25% cut of the ransom profits, which are collected in virtually the same manner as recent crypto-type ransomware threats.
We knew and predicted that the New Year would usher in several new and aggressive malware threats sporting advanced infection methods that we have never seen before. However, we didn't suspect such threats to be emerging within a few days of 2016.
JS.Crypto Ransomware is a first of its kind threat. First identified by victimized computer users reporting on popular security forums, JS.Crypto, or Ransom32, was found to only target Windows computers. After security researchers started to dive deeper into the functions of JS.Crypto Ransomware, it was then concluded that the threat utilizes NW.js framework, which allows an application to be written once but usable across multiple operating systems or platforms. Essentially, JS.Crypto Ransomware may not only infect machines running Windows but ones running Mac OS X and Linux.
So far, JS.Crypto Ransomware has only been seen in a form to attack Windows computers in an executable .exe file format. While regular JavaScript has certain limitations within web browsers, the JS.Crypto Ransomware using JavaScript, mainly the cross-platform variation NW.js (Node Webkit), it may be packaged for other operating systems and allow much more control and interaction.
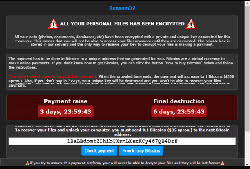
The fundamentals and victimized user interface of JS.Crypto Ransomware is not much different from other recent crypto-type ransomware threats. The threat will encrypt files and offer a method to the computer user for decryption for a ransom fee. One of the differences lies within the JS.Crypto Ransomware threat being offered as a ransomware-as-service, which allows negotiation for the Tox ransomware developer and the percentage cut they get for each paying victim. What this means is that the JS.Crypto Ransomware authors will want a cut of the ransom payments.
Currently, the JS.Crypto Ransomware (Ransom32) threat is spread through clever spam email message attachments. Many of the cybercrooks running the campaigns that initiate the spread of JS.Crypto Ransomware are using a hidden server on the Tor network where they may be able to obtain a customized JS.Crypto Ransomware threat tailored to one's specific attack methods.
Some of the apparent issues that lie within JS.Crypto Ransomware, which may lead to its slow spread rates, is its massive file size being 32 MB. At such a large size, many potential victims may dismiss downloading the attachment. Most ransomware threats are sized around only 1 MB, which is small enough not to draw any suspicions by potential victims. So far, this major flounder has kept JS.Crypto Ransomware in check and has not propagated as fast as other ransomware threats we have seen in the recent past. However, the potential for JS.Crypto Ransomware to be customized and upgraded is there, which may eventually lead to widespread infections.