'CryptoJoker' is the Latest Crypto-Type Ransomware Allowing Ransom Fee Negotiation
 As the New Year gets its start, new and emerging ransomware threats are making their presence known as a threat dubbed CryptoJoker Ransomware arrives on the scene bringing a new family of threats that encrypt files.
As the New Year gets its start, new and emerging ransomware threats are making their presence known as a threat dubbed CryptoJoker Ransomware arrives on the scene bringing a new family of threats that encrypt files.
The CryptoJoker Ransomware threat is known to have the fundamental activities that other well-known crypt-type threats have had, such as CryptoLocker and CrytoWall. The difference in CryptoJoker Ransomware lies within its ability to encrypt files using the .crjoker string added to the end of each encrypted file. Additionally, the malware is known to infect computers by arming PDF files via aggressive spam and spear phishing campaigns while it does not specify an exact amount for obtaining a decryption key to restoring the encrypted files.
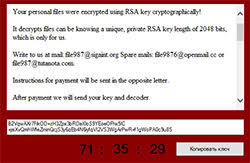
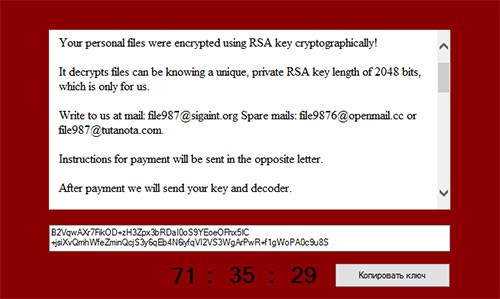
The similar aspects of CryptoJoker Ransomware to that of threats like CryptoLocker are not far from what we have witnessed in the countless cases of encryption taking place using the AES-256 encryption followed by an ingenious pop-up message giving computer users an option of paying a ransom fee. Those victimized by CryptoJoker Ransomware are encouraged to send an email to one of the three email addresses (file987@sigaint.org, file9876@openmail.cc, or file987@tutanota.com) listed on its popup message, as shown in Figure 1 below, to negotiate payment for decrypting their files. The negotiation aspects of CryptoJoker Ransomware are also a rather new technique that has not been fully exploited by previously identified ransomware threats.
Figure 1. CrytoJoker Ransomware Threat Message popup
By offering a method of negotiating the ransom fee, the cybercrooks behind CryptoJoker Ransomware can leverage their ability to collect payment. While the only method for decrypting and restoring files affected by CryptoJoker Ransomware is by obtaining a decryption key from its authors or restoring the files from a backup, computer users will be left no choice to pay the fine or go another route to wipe their system clean and reinstall Windows. Considering the latter option proves to be the less-traveled road for most computer users, offering a negotiated payment is naturally a more attractive proposition for computer users who may not be able to afford hefty ransom fees.
So far, due to the newness of CryptoJoker Ransomware, details on its detection rates are not known. However, we suspect CryptoJoker Ransomware will be just as popular, if not more prevalent, than CryptoLocker and CryptoWall Ransomware threats. What we do know, for now, is that CryptoJoker Ransomware targets about 30 file extensions. Moreover, CryptoJoker Ransomware will commonly delete shadow volume copies leaving victimized computer users with no changes of recovering the encrypted files unless they have a backup copy on another drive or bite the bullet and pay the ransom fee for a decryption key.
Our outlook for the New Year seems to already be panning out exactly how we predicted, and that's unfortunate for users of vulnerable computers. With the discovery of CryptoJoker Ransomware marking the beginning of 2016, we look for the year to be filled with an abundance of ransomware threats of the similar vernacular.
What computer users can do now to help protect themselves into this New Year, is to ensure all software is updated and to utilize an up-to-date copy of antivirus or antimalware software to proactively detect, prevent and remove emerging computer viruses and malware threats.