HackTool:Win32/Patcher.D
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 1,701 |
| Threat Level: | 50 % (Medium) |
| Infected Computers: | 64,737 |
| First Seen: | November 22, 2012 |
| Last Seen: | February 5, 2026 |
| OS(es) Affected: | Windows |
Table of Contents
Aliases
15 security vendors flagged this file as malicious.
| Antivirus Vendor | Detection |
|---|---|
| AVG | Generic30.AMTI |
| AhnLab-V3 | Trojan/Win32.FakeAV |
| Kaspersky | Trojan.Win32.FakeAV.oshe |
| Avast | Win32:FakeAV-EEG [Trj] |
| AntiVir | SPR/Cain.7992528 |
| Kaspersky | not-a-virus:PSWTool.Win32.Cain.284 |
| F-Prot | W32/Backdoor2.HMWL |
| K7AntiVirus | Backdoor |
| McAfee | PWCrack-Cain |
| AVG | HackTool.MCQ |
| AntiVir | SPR/UltraSurf.A.1 |
| Kaspersky | not-a-virus:NetTool.Win32.UltraSurf.gu |
| K7AntiVirus | RemoteTool |
| AVG | Generic30.AMBN |
| Fortinet | W32/Pincav.CLLG!tr |
SpyHunter Detects & Remove HackTool:Win32/Patcher.D
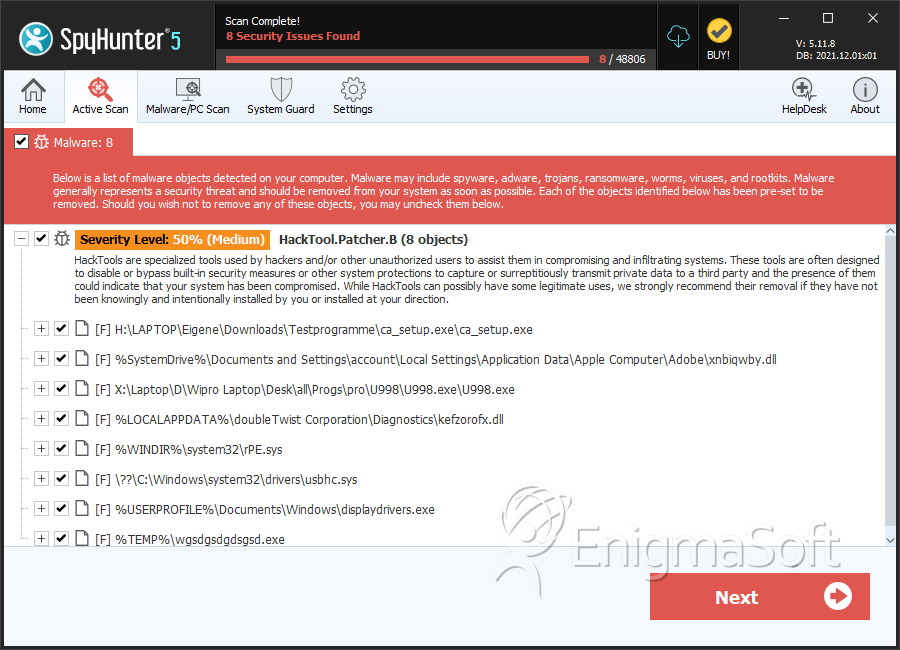
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | ca_setup.exe | 6fd3c21ef5e301a91e44d2666d9dc90c | 258 |
| 2. | xnbiqwby.dll | 8408f944b27201aef5b3785167241884 | 93 |
| 3. | U998.exe | 7a69ea0b15862846e124cd70cef1a448 | 86 |
| 4. | kefzorofx.dll | 4721e7530bbb70b252f672bc6ee407e3 | 58 |
| 5. | rPE.sys | 9ba69c21950479ce0f958dd3240db5d6 | 24 |
| 6. | usbhc.sys | 666372e9bf260bcaa96b85066078275e | 14 |
| 7. | displaydrivers.exe | baf9fd30cfe7cca9a9ea435e743419e8 | 9 |
| 8. | wgsdgsdgdsgsd.exe | 8eb7a135045db08d9c77b374bc32cdb0 | 6 |
| 9. | skymonk_24243443_77.exe | 949dc2cdaa70289c1394a872f17374b0 | 5 |
| 10. | 2009016142.Adobe_Flash_win.exe | b1a76dbfbebfa5641fc1827b05c4fd70 | 5 |
| 11. | antim32.exe | 5db46e27037310a20ba153d6702f6bd1 | 4 |
| 12. | RMActivate_ssp.exe | 1e17d3fecee94cb2fe0b1bfe70cc9eb2 | 3 |
| 13. | stifolo.dll | a25b468edf73c46545d3d29bd365999a | 3 |
| 14. | winldr.exe | 4212a41ab67ba55c7a6a79ff030119ae | 2 |
| 15. | tTEvbsKqrbOXLI.exe | 9ac0c8b795b6bdc11be79a48f062ccf5 | 2 |
| 16. | 4207.exe | 831ab49c4eaaee0833bff6b112d3bfdf | 1 |
| 17. | UIAutomationCore.exe | 79342474962eda125aad8fcd92820c87 | 1 |
| 18. | thawbrkr.exe | cf1f7d9c2c40cb7dee4486b5d10bd723 | 1 |
| 19. | exoljsv.exe | eb1e2f7ece9938a9bd8dd59dcfae3d6a | 1 |
| 20. | Nbt.exe | 9b48cc94a29da18cea15684a91f5dc9a | 1 |
Analysis Report
General information
| Family Name: | HackTool.Patcher.B |
|---|---|
| Signature status: | No Signature |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
ce64b03650dae0172c2fdd2958e1afa0
SHA1:
c778997992ff3c45a70780705abd9d55d42ae158
SHA256:
1ABBC8DE4C0A0C08EE1CF972B3F4CA4CAB7BCCC1C3553EF0FC90F1A76B7D3FE6
File Size:
57.34 KB, 57344 bytes
|
|
MD5:
2f941f7dad3392e23814b1712f463981
SHA1:
199ed5bf30068f5ac90e62c20d68d060cdfde603
SHA256:
8856F9771A581778A4BF222462D75F917661B39F8C6BE935D937E7D74F937123
File Size:
240.64 KB, 240640 bytes
|
|
MD5:
d66289bb0455d047804fbe6b686895dc
SHA1:
84194bc166e3869a95c1d09d4090c36b4626f83f
SHA256:
056B5FE084478CD78DDBE8936F888E5DACDB2B38CF3ED6B19389591BAA363EDD
File Size:
1.06 MB, 1061376 bytes
|
|
MD5:
cb2c0bc1902ff3294af444a068632a0d
SHA1:
f167cbd31c467a0b5b5bc95693ae9c3eba2700cb
SHA256:
63CB7F1AF064FF1DB54E73781D6D21CF3E33B31E9B8AA704FC560BE4FB03CA0E
File Size:
457.22 KB, 457216 bytes
|
|
MD5:
6ea58085bf5901e36cee44e953e7bb2a
SHA1:
bad3a7a1144dfb1a16db84c98172273acf78206c
SHA256:
A27328A3EADD0AD50C6226A9B62700AAC668EBE3D40485327836422BFC70D62A
File Size:
227.33 KB, 227328 bytes
|
Show More
|
MD5:
5539b8e219195d5c4a46e2bdabba2ac5
SHA1:
7bec13ed90eaea46f0aeedf3082f0fea0c03e897
SHA256:
C2446CE42B2FE83575BB7F3905D0B6ECB6BC38E16C8A6014DDF5C8AA0C8DA3C6
File Size:
11.26 KB, 11264 bytes
|
|
MD5:
563fc2e92a4d282467c9910e3ea21449
SHA1:
3fe1d8181680060d550facd328e7f660c91a517d
SHA256:
8D9AC7BD8D83F2A179CBE9B8AAE427761ECA749D0059BA5DF72F5E582A077628
File Size:
122.88 KB, 122880 bytes
|
|
MD5:
98727de361904fa0962d2aca68494441
SHA1:
ea0eb777b8aef78b1d6e26d1fe7d75d43483caf3
SHA256:
AD217264CB9696F6A613847651C0E09B870656495EE348E72C76C19C2169AE61
File Size:
62.98 KB, 62976 bytes
|
|
MD5:
4ed4347aa55836ef094f0f2cec216bb1
SHA1:
df65d42bb0113216812c8dec5e3da07c54d6dcb7
SHA256:
EE6670AA25B73FCCF26661A98FE0CF360874A48B996D57D19FC786D2D48986B9
File Size:
119.81 KB, 119808 bytes
|
|
MD5:
5c61b70f64f72611afeab26b8e22b518
SHA1:
872cef6e7c7f99c32d9ba82eee572cb66127f1df
SHA256:
0D73CE0D7BA8C8BF0A0B2FFB99E5AB7A8A38FC91EB2744E2614D19DD362DEB9F
File Size:
11.26 KB, 11264 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have exports table
- File doesn't have relocations information
- File doesn't have security information
- File has been packed
- File has exports table
- File has TLS information
- File is 32-bit executable
- File is either console or GUI application
Show More
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
- File is Native application (NOT .NET application)
- File is not packed
- IMAGE_FILE_DLL is not set inside PE header (Executable)
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Icons
File Icons
This section displays icon resources found within family samples. Malware often replicates icons commonly associated with legitimate software to mislead users into believing the malware is safe.File Traits
- .UPX
- 2+ executable sections
- dll
- HighEntropy
- MPRESS
- MPRESS Win32
- Native MPRESS x86
- No Version Info
- packed
- PEC2
Show More
- PECompact v2.20
- SusSec
- upx
- WriteProcessMemory
- x86
Block Information
Block Information
During analysis, EnigmaSoft breaks file samples into logical blocks for classification and comparison with other samples. Blocks can be used to generate malware detection rules and to group file samples into families based on shared source code, functionality and other distinguishing attributes and characteristics. This section lists a summary of this block data, as well as its classification by EnigmaSoft. A visual representation of the block data is also displayed, where available.| Total Blocks: | 27 |
|---|---|
| Potentially Malicious Blocks: | 24 |
| Whitelisted Blocks: | 3 |
| Unknown Blocks: | 0 |
Visual Map
? - Unknown Block
x - Potentially Malicious Block
Similar Families
Similar Families
This section lists other families that share similarities with this family, based on EnigmaSoft’s analysis. Many malware families are created from the same malware toolkits and use the same packing and encryption techniques but uniquely extend functionality. Similar families may also share source code, attributes, icons, subcomponents, compromised and/or invalid digital signatures, and network characteristics. Researchers leverage these similarities to rapidly and effectively triage file samples and extend malware detection rules.- Patcher.A
- Patcher.B
- Patcher.C
Files Modified
Files Modified
This section lists files that were created, modified, moved and/or deleted by samples in this family. File system activity can provide valuable insight into how malware functions on the operating system.| File | Attributes |
|---|---|
| c:\users\user\appdata\local\temp | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\bassmod.dll | Generic Write,Read Attributes |
| c:\windows\syswow64\bassmod.dll | Generic Write,Read Attributes |
| c:\windows\syswow64\muzika.xm | Generic Write,Read Attributes |
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| Anti Debug |
|
| User Data Access |
|
| Syscall Use |
Show More
|
| Process Manipulation Evasion |
|
| Process Shell Execute |
|
Shell Command Execution
Shell Command Execution
This section lists Windows shell commands that are run by the samples in this family. Windows Shell commands are often leveraged by malware for nefarious purposes and can be used to elevate security privileges, download and launch other malware, exploit vulnerabilities, collect and exfiltrate data, and hide malicious activity.
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\ea0eb777b8aef78b1d6e26d1fe7d75d43483caf3_0000062976.,LiQMAxHB
|