Decryptor Released For GetCrypt Ransomware
 GetCrypt Ransomware is a recently detected malware threat that encrypts the data on the compromised machine and demands a ransom for its decryption. The malware was first caught by the cybersecurity research team neo_sec. GetCrypt is being spread through malvertising campaigns that redirect users to sites hosting the RIG exploit kit. Landing on one of the poisoned sites will cause the exploit kit to do what its name suggests - exploit vulnerabilities on the user's computer in order to drop the ransomware on it.
GetCrypt Ransomware is a recently detected malware threat that encrypts the data on the compromised machine and demands a ransom for its decryption. The malware was first caught by the cybersecurity research team neo_sec. GetCrypt is being spread through malvertising campaigns that redirect users to sites hosting the RIG exploit kit. Landing on one of the poisoned sites will cause the exploit kit to do what its name suggests - exploit vulnerabilities on the user's computer in order to drop the ransomware on it.
If your files have already been rendered unusable by GetCrypt, do not despair as there might still be hope to recover them without paying anything to the criminals - a decryptor for GetCrypt is available. Still, to decrypt the affected files it is necessary for each victim of the ransomware to have access to one of the original unencrypted files. The decryptor software uses such a pair of an encrypted and unencrypted version of the same file to brute force the decryption key and unscramble the user's files.
GetCrypt Avoids CIS Countries
Upon execution, the first step of GetCrypt is to check the Windows language of the infiltrated machine and if it is set to either Ukranian, Belarusian, Russian, or Kazakh, the ransomware simply shuts itself down. In all other cases, GetCrypt employs CPUID to create a string of 4 characters that is going to be used as an extension for the encrypted data. While the vast majority of ransomware threats target certain file types for encryption, GetCrypt is instead designed to run a scan and encrypt all files not located in a specific list of directories with the Salsa20 and RSA-4096 encryption algorithms. The full list of directories to avoid consists of ":\ProgramData, :\Users\All Users, :\$Recycle.Bin, :\Program Files, :\Local Settings, :\Boot, :\Windows, :\System Volume Information, :\Recovery, AppData." All shadow volume copies of the encrypted files will be deleted through the "vssadmin.exe delete shadows /all /quiet command."
GetCrypt Attempts To Access Network Shares By Brute Force
While it is not that unusual for ransomware threats to spread to network shares connected to the already infected machine, GetCrypt's behavior deviates from the norm. It leverages the "WNetEnumResourceW" function to enumerate a list of available network shares. If the ransomware fails to connect to one of them, it will attempt to brute force the required credentials by using an embedded list of usernames and passwords.
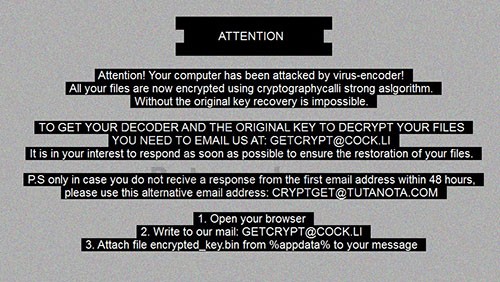
The rest of the encryption process is pretty standard. A text file named "# decrypt my files #.txt" containing a ransom note will be dropped on the desktop screen as well as in each folder with encrypted files. The text of the note is:
Attention! Your computer has been attacked by virus-encoder!
All your files are now encrypted using cryptographycalli strong aslgorithm.
Without the original key recovery is impossible.
TO GET YOUR DECODER AND THE ORIGINAL KEY TO DECRYPT YOUR FILES YOU NEED TO EMAIL US AT: GETCRYPT@COCK.LI
It is in your interest to respond as soon as possible to ensure the restoration of your files.
P.S only in case you do not recive a response from the first email address within 48 hours
Also, the background image of the user's desktop will be replaced with a new one: