XP Security 2013
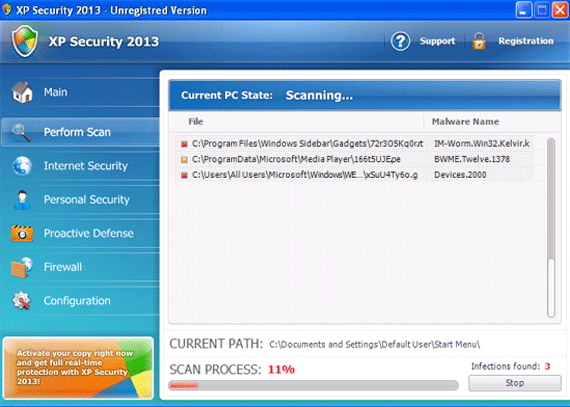
XP Security 2013 Image
XP Security 2013 is a dangerous anti-virus program that propagates with the help of Trojans. XP Security 2013 tries to imitate a trustworthy and powerful security program by pretending to scan the compromised PC and detect malware infections on the computer system, which, in truth, are absolutely false. XP Security 2013 attempts to convince victims to purchase its so-called full version to remove those supposed PC infections. XP Security 2013 was created by cybercriminals with the only aim to deceive unsuspecting computer users and swindle them out of their money.
XP Security 2013 belongs to a huge family or rogue security programs, the FakeRean family that has among its members Antivirus 2008, Windows Antivirus 2008, Vista Antivirus 2008, Antivirus Pro 2009, AntiSpy Safeguard, ThinkPoint, Spyware Protection 2010, Internet Antivirus 2011, Palladium Pro, XP Anti-Virus 2011, CleanThis, PC Clean Pro, XP Home Security 2012, Windows Clear Problems, XP Security 2012, Antivirus PRO 2015.
XP Security 2013 has no capability of detecting and removing any type of malware threats. Once installed, XP Security 2013 immediately starts displaying fake pop-up warning messages to intimidate you into thinking that your PC is compromised. In reality, your computer has been corrupted by malware, but the real security threat is XP Security 2013 itself, which has to be removed as soon as possible with a genuine security program. ESG's security analysts highly recommend you not to believe anything associated with XP Security 2013 and purchase this malware application.
File System Details
| # | File Name |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|
| 1. | %LocalAppData%\[RANDOM CHARACTERS].exe | |
| 2. | %LocalAppData%\[RANDOM CHARACTERS] | |
| 3. | %Temp%\[RANDOM CHARACTERS] | |
| 4. | %AppData%\Roaming\Microsoft\Windows\Templates\[RANDOM CHARACTERS] | |
| 5. | %CommonAppData%\[RANDOM CHARACTERS] |

