Are You Sure You’re NOT Infected with Malware?
Don’t Fall Victim to Malware or Ransomware Attacks!
Detect and remove malware, viruses, ransomware & other threats for FREE! Get Protected with SpyHunter.
Download SpyHunter (FREE Trial!)*First of all, we are not referencing the mystery meat jellied in a can, but rather unwanted electronic mail and messaging polluting the Internet. Spam is the electronic version of junk mail sent through the postal service and is one of many malicious strategies employed over the Internet by cybercriminals or unscrupulous advertisers.
Spam is distributed in bulk, so sent to the masses. Distributors of spam are known as spammers and their primary goal is to reach as many end-users as possible in hopes of carrying out one or more payloads. Payloads could be scams that sell fake programs or tools, phish for vital data, secretly download malware, or even as basic as unsolicited advertisements. The cost to distribute spam is minimal and is roughly a manner of obtaining email addresses or lists, whether through purchase or deceptively, i.e. theft. The bigger cost is borne by the owners of the broadband, which is maliciously violated, or recipients, who fall victim to scams. According to many trusted computer security sources, including SpamLaw.com, Spam 45% of all Email is Spam.
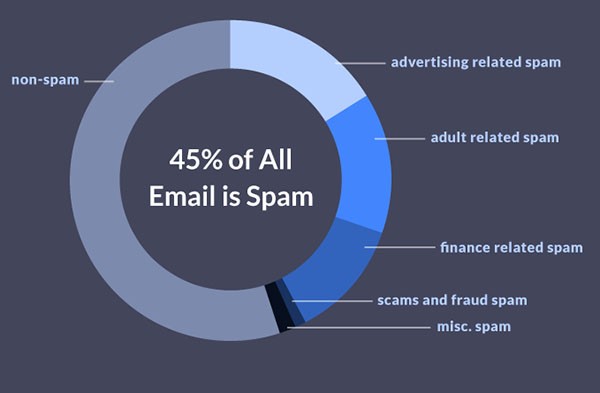
45% of all Email is Spam – Source: SpamLaw.com
While email spam ranks high on the list of well-used spam strategies, other online media may be infiltrated or violated. Let’s take a closer look at some of these delivery trucks:
Email Spam – Email spam is a reminiscence of junk mail delivered through the postal service. However, not every email spam communication is full of unwanted advertisements. Cybercriminals invest a lot of stolen money studying human behavior and learning better ways to cheat PC users out of money, gather vital data or drop malware onto vulnerable systems. Email spam can be cleverly shaped and can spoof legitimate businesses or persons, i.e. family or friends. Email spam may contain an infectious link or attachment and when clicked, can secretly download malicious programs or redirect victims to fictitious web pages and forms to deceptively gather vital data.
Instant Messaging – Spam delivered via messaging clients, such as Skype, Yahoo! Messenger, Google Talk, Windows Live, etc. Instant messaging channels are attractive because most clients are not blocked by firewalls.
Social Networking – Security experts have seen a spike in social networking spam campaigns, since these sites, i.e. Twitter or Facebook, are not only popular and widely used, but offer a lax and friendly environment. Spammers hack account owners to dupe trusting associates, i.e. friends or followers and may post an infectious link, attachment, or video that when click unleashes a nasty infection or malicious program.
Spamdexing is when cybercriminals alter HTML pages and use black hat SEO (search engine optimization) tricks to manipulate the ranking of their malicious websites, having them placed high on search engine lists.
In the past, spammers posted infectious links on sites such as YouTube, however, such practice of allowing links has been discontinued. Now spammers spoof sites like YouTube and mislead the victim by giving it a juicy or sensationalized name and description, i.e. Death of Lady Gaga or Live Suicide, etc. When the link is clicked, the payload is unleashed, i.e. malware dropped, rerouted to a malicious website or survey generating revenue for a cybercriminal, etc.
Spam may be delivered via zombie networks or using another malware form, i.e. a Trojan. Payloads might be a fake form used to collect vital data, or dropped malware that installs a backdoor giving a hacker remote access and control of the infected system. Often dropped malware is absent an interface, keeping the victim in the dark. Today’s malware is stealth and is able to disarm weaker antivirus programs and security measures in place as well as reconfigure the system as follows:
Cybercriminals may partake in email address harvesting to nourish their spam campaigns. Email address harvesting collects and sells email addresses compiled in databases. While most scams resulting from spam rely on user help, i.e. click, unfortunately, many PC users do not take the time to fully read agreements or verify the source of emails, links, or attachments. Therefore, take heed and implement safety procedures that protect your vital data and keep hackers out of your computer.
Last updated: 2026-02-08