Petya/NotPetya Ransomware CyberAttack: It Wasn't About the Money
 It's been a busy few days for the cyber security community and victims of a worldwide cyberattack. As you probably know, on Tuesday, a massive malware outbreak locked computers in hundreds of organizations across the globe and disrupted their operations. Here's an example of the difficulties enterprises were faced with. TNT Express, a Dutch courier service, was among the affected organizations, and in addition to slowing down the delivery of some items, the attack also resulted in the temporary trading halt of the shares of FedEx, its principal company.
It's been a busy few days for the cyber security community and victims of a worldwide cyberattack. As you probably know, on Tuesday, a massive malware outbreak locked computers in hundreds of organizations across the globe and disrupted their operations. Here's an example of the difficulties enterprises were faced with. TNT Express, a Dutch courier service, was among the affected organizations, and in addition to slowing down the delivery of some items, the attack also resulted in the temporary trading halt of the shares of FedEx, its principal company.
Security researchers were called in to see what was going on and find out how to fight against the threat. It quickly became clear that the malware was based on the Petya ransomware which gained infamy last year for overwriting the Master Boot Records (MBRs) and Master File Tables (MFTs) of infected computers in addition to encrypting files. Petya is a classic ransomware operation. After locking the information, its operators demand money for restoring things back to normal.
Cybercriminal's Greed Gets In The Way
Petya is a way of satisfying the criminals' greed, and initially, experts thought that the crooks running NotPetya, the malware that was responsible for Tuesday's attack, are driven by the same motive. Further investigation reveals, however, that this might not be the case.
Let's take a look at some of the differences between Petya and NotPetya. After rummaging around under the hood, the security experts concluded that the current file-encrypting mechanism is not the same as the one Petya used in the past. The more obvious differences were visible from the ransom note, as shown in Figure 1 below. NotPetya's operators decided to do away with what has now become the Hollywood cliché of a skull and crossbones ASCII image, and they borrowed some of the text from the WannaCry ransomware. The payment system was different as well.
Figure 1. The differences between Petya's and NotPetya's ransom notes
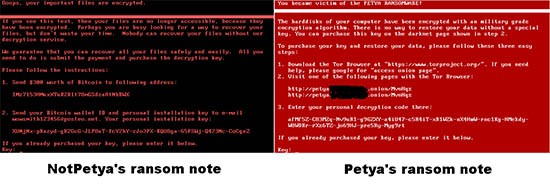
Petya's ransom notes from 2016 gave victims a personal ID and instructed them to go to a rather well-designed website hosted on Tor where they would enter the said ID. Then, the users needed to process the bitcoin payment and wait for the decryption key from the said website.
NotPetya also gave victims their own ID, but instead of redirecting them to Tor, the malware author urged them to send it to wowsmith123456@posteo.net. Presumably, he was going to reply with further instructions. Unfortunately, a few hours after the reports about the infection came in, Posteo closed the email account and announced that they are unwilling to tolerate cybercriminals using their services. Right now, the victims don't have a way of contacting NotPetya's operator which means that their only hope of restoring the files is gone. And it's all thanks to the author's silly mistake of moving the communication channel to email. Or is it?
The personal ID in the ransom note plays a crucial role in retrieving the data hit by the old Petya. Through it, the crooks are able to get more information on which victim is contacting them exactly, and, upon successful payment, they can provide the right decryption key.
There Is More To The Petya Cyberattack Epidemic Than Originally Thought
Yesterday, researchers from Kaspersky tried to find out how NotPetya's author uses the victim's personal ID to help with the retrieval of the information. The ID, it turns out, is generated by a function called CryptGenRandom. Did you spot the "Random" in the name?
That's right, NotPetya's personal ID is a completely random string of symbols which contains no information that could be of any use for retrieving the lost files. This means that even if the crook's email account were live, he still wouldn't be able to help victims restore their systems back to normal.
Matthieu Suiche, a security specialist and founder of Comae Technologies, was also looking at the differences between Petya and NotPetya yesterday. More specifically, he was examining the way the two malware families attack the Master Boot Record of the infected host, and he realized that if the correct key is provided, the MBRs of computers hit by Petya can be restored. With NotPetya, however, this is not possible according to his research, and he reckons that this is deliberate.
In fact, both Suiche and Kaspersky think that in reality, NotPetya is not ransomware at all, but rather, a wiper the sole purpose of which is to cause as much damage as possible. The ransomware disguise, Suiche says, is nothing more than "a lure for the media." This theory is also supported by the fact that there's about $10 thousand in the author's Bitcoin wallet and yet nobody is even trying to take the money. Money, as we mentioned already, is the ultimate goal of all ransomware operators.
Suiche and Kaspersky's opinion is bound to open the question of attribution, and we're pretty sure that people will soon start saying that NotPetya came from a mysterious Russian APT crew with an interesting name. Whether they'll have enough evidence to support this claim is another matter, and for the victims, it's unlikely to make any sort of difference.
There might be something affected organizations will be interested in, though. Yesterday, JANUS, the author of the original Petya ransomware, announced that he's looking into NotPetya and is trying to find out if the files encrypted by the new malware could be decryptable by his own private keys. A couple of hours later, he requested an encrypted file so that he could perform the tests. Although there can be no guarantees, help might be coming from the unlikeliest of places. That's how strange the world of malware could be sometimes.