Hackers Breach 60 Ad Servers, Loading Them With Malicious Ads
 Advertising security company Confiant recently published a report that details the exploits of a hacking group that has been actively taking over ad servers and inserting malicious ads in their ad inventory.
Advertising security company Confiant recently published a report that details the exploits of a hacking group that has been actively taking over ad servers and inserting malicious ads in their ad inventory.
The hacking campaign was discovered last month, but after some retrospective analysis, security experts concluded that it has been ongoing for at least nine months. Confiant has dubbed the hacking group that they first unknowingly came across in August 2019, Tag Barnacle.
The main target of the Tag Barnacle group is advertising networks that run outdated versions of the Revive open-source ad server. Once the attackers breach the server, they silently alter existing ads and inject them with malicious code that hijacks sessions and redirects visitors to websites peddling malware that is usually masquerading as legitimate Adobe Flash Player updates.
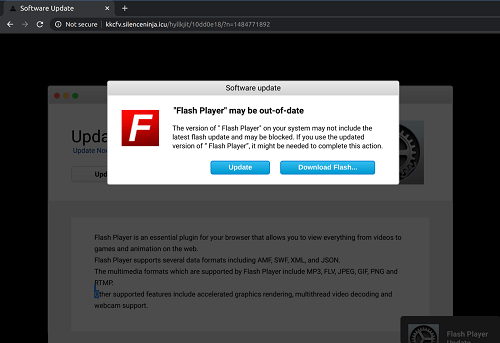
Fake Flash Player update. Source: Confiant
Security experts say that the malware samples that these fake updates are used to push range from the Shalyer Trojan on macOS systems to InstallCore on Windows, and are used to further corrupt the infected computer with all sorts of info-stealers, unwanted browser extensions, and ransomware.
Table of Contents
The Reach
Confiant says that Tag Barnacle has compromised around 60 Revive ad servers, which malicious activity detected on more than 360 websites. Tag Barnacle's reach, however, could be much bigger, as the Revive software is also used by smaller real-time bidding (RTB) ad serving providers.
"If we take a look at the volumes behind just one of the compromised RTB ad servers - we see spikes of up to 1.25MM affected ad impressions in a single day," said Confiant Senior Security Engineer, Eliya Stein.
Not Your Everyday Malvertiser
Directly hacking ad servers on this scale hasn't been the norm for quite a while, as malvertisers usually opt for a different strategy. Not every malvertiser has the skillset needed to hack ad serving infrastructure, but everyone nowadays can buy ad space on legitimate websites fairly cheaply.
Buying ad space works for both ad networks that are willing to turn a blind eye to malvertising campaigns being run on their servers, and for malvertisers who are not willing to take the risk of actually hacking an advertising network. The Tag Barnacle group, however, is one of the exceptions to this trend.
"We have seen other malvertisers do this, but it's less widespread in general for several reasons," Stein elaborated in an email sent to ZDNet. "First of all, I believe there's a sense among the attackers that there's a legal gray area when it comes to malvertising, but once you compromise an ad server, there is no question that you've broken the law in a big way."
Malvertising Campaign Still Ongoing
Stein also stated that Confiant has been notifying advertising companies that have been breached by the Tag Barnacle group over the last few weeks. Still, not everyone has acted on the security experts' warning.
While some of the ad servers were briefly impacted, others continue to run Tag Barnacle's malvertising campaigns. It's now in the hands of the owners of those ad servers to patch their systems.
Meanwhile, end-users can protect their systems from malvertisers such as the Tag Barnacle group by installing legitimate antivirus software.