Hackbit Ransomware Campaign Uses GuLoader Against European Targets
 Security researchers from Proofpoint have recently found a Hackbit ransomware campaign targeting mid-level employees across Germany, Austria, and Switzerland with emails containing malicious Excel attachments.
Security researchers from Proofpoint have recently found a Hackbit ransomware campaign targeting mid-level employees across Germany, Austria, and Switzerland with emails containing malicious Excel attachments.
The emails are sent from accounts registered with GMX Mail, a Germany-based free email provider mainly serving a European client base. The spear-phishing email campaign's volume was relatively low, and it targeted the legal, pharmaceutical, financial, retail, business service, and healthcare sectors. The campaign's focus was customer-facing employees with readily available contact information such as attorneys, advisors, managing directors, insurance advisors, project managers, and directors.
"The largest volume of messages we observed were sent to the information technology, manufacturing, insurance, and technology verticals," a Proofpoint report read.
The spear-phishing emails were crafted to look like tax refund documents and invoices from local companies. One of the German examples used logo and branding of 1&1, a well-known German telecom company. Some of the emails used subject lines such as "Ihre Rechnung (Translated: Your Bill)" and "Fwd: Steuerrückzahlung" (Translated: Tax Repayment)."
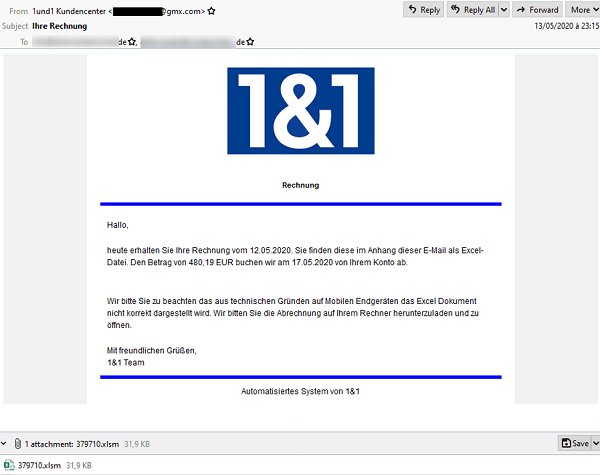
Example of an "Ihre Rechnung (Transladed: Your Bill)" email. Source: Proofpoint
Google Translate translated this example of a German lure as:
Today you will receive your invoice dated 12.05.2020. You will find it in the attachment to this e-mail as an Excel file. We will debit the amount of EUR480.19 from your account on May 17th, 2020.
Please note that due to technical reasons the Excel document is not displayed correctly on mobile devices. We ask you to download the invoice on your computer and open it.
Best regards,
The email contains an Excel attachment named 379710.xlsm, containing malicious macros. Since neither the malware nor the macros can work on a mobile device, the email instructs the recipient to open the attachment from a computer. Once the attachment is opened, the user is told in both German and English to enable Excel macros.
If the victim makes the mistake of enabling macros on the Excel spreadsheet, it will download and execute GuLoader, a relatively new, but widespread dropper that is used to deliver second-stage malware. The GuLoader dropper is configured to download and run a sample of Hakbit, the most recent variant of the Thanos ransomware-as-a-service (RaaS).
The Hackbit ransomware uses AES-256 encryption to lock the victim's files away and demands a ransom. The threat actors are asking for 250 Euros in bitcoin for the decryption of the data. Despite the relatively low ransom amount, researchers noted that as of June 16, 2020, there were no transactions that indicated ransom payments to the bitcoin wallet listed in the ransom note.