DoppelPaymer Ransomware
DoppelPaymer Ransomware Image
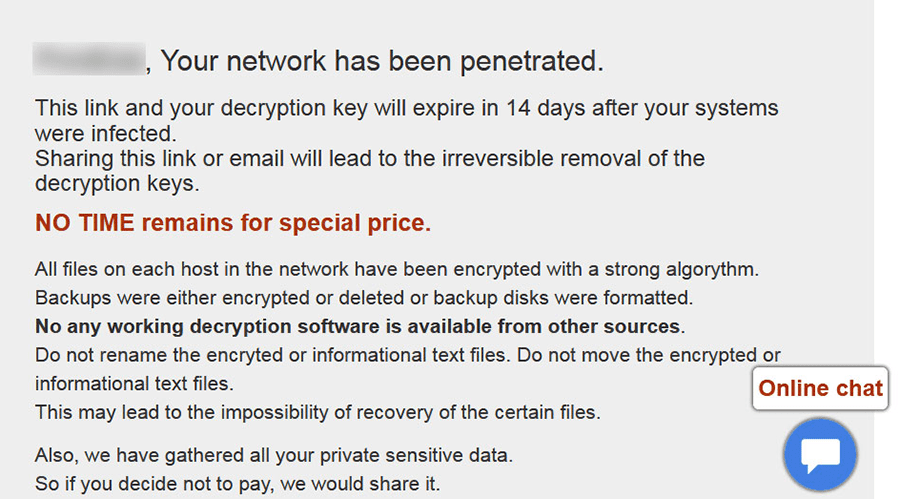
DoppelPaymer Ransomware is a file-locking trojan that blocks your media and leaves ransom notes redirecting you to a payment portal for the unlocker. Although it's an update of the highly-similar BitPaymer Ransomware, it uses a separate encryption method and requires a different decryptor for restoring any files. Let your anti-malware products remove DoppelPaymer Ransomware as soon as they detect it and store secure backups for undoing the side effects of its attacks.
This Week in Malware Ep6: DopplePaymer Ransomware #thisweekinmalware
Just a Doppelganger Getting Paid
At least one criminal from the same group of hackers that brought the world Gameover Zeus and the Dridex banking trojan is turning old tools into new money, in theory. A new variant of BitPaymer Ransomware, from the 'Business Club' threat actor, is circulating with attacks targeting both private sector companies and government networks. This update, DoppelPaymer Ransomware, is sufficiently different that one could call it a fork, although both its ransoming infrastructure and code are too similar to those of BitPaymer Ransomware for being coincidental.
DoppelPaymer Ransomware is more than just a fire-and-forget project, and has at least eight iterations out in the wild, each with more improvements to their features than the previous one. The trojan uses AES encryption – with padding – along with RSA-2048, for encrypting and blocking digital media from opening. Our malware experts also caution that DoppelPaymer Ransomware can lock files more quickly than its predecessor, thanks to a multi-threaded encryption routine.
DoppelPaymer Ransomware's ransom demands for the unlocker are as flexible as its version numbers. Although it always asks for Bitcoins, the amount ranges from as low as two up to an incredibly-improbable one hundred – over a million USD. Accordingly, our malware experts see most attacks matching targets with significant financial backing, such as the servers for US city governments and South American national ministries.
Sticking a Fork in a Trojan's Forked Development
Without decryption code leaks, bugs, or other, unanticipated assistance, our malware experts rate it as not probable that a free decryptor will be compatible with DoppelPaymer Ransomware. When taking into accounts its development pace, any solutions, once created, are likely of being made defunct in a matter of days or weeks. Users always should have backups secured properly on external devices for a long-term, and dependable, counter to file-locker trojans.
Government server compromises can occur through brute-forcing logins, tricking employees into opening malicious files over e-mail, or abusing software vulnerabilities. In turn, using complex passwords, learning the visual patterns of phishing scams, and updating software routinely will leave your server at lessened risk. Our malware experts, also, recommend not enabling macros in potentially dangerous documents or spreadsheets, which are very well-used infection vectors.
The majority of file-locking trojans have limited protection against conventional anti-malware products or their threat detection methodologies. Updated anti-malware services should delete DoppelPaymer Ransomware as a threat as soon as it intrudes on your computer.
DoppelPaymer Ransomware is a clone that's striking out on its own, but comes with the same, old, 'for money' mentality. If users don't want to be the cashout point for its campaigns, they should tend to their digital media.

