CryLocker Ransomware Mysteriously Tracking Victims via Imgur, Google Maps and Pastee Services
A New Ransomware Family Uses Legitimate Services to Achieve its Goal
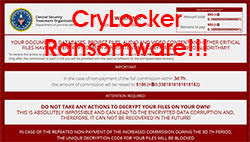 There's a new family of ransomware out there, and its name is CryLocker. CryLocker was discovered at the beginning of the month by computer security researchers who call themselves the MalwareHunterTeam. Since then, numerous other experts have dissected the code, and they've come to the conclusion that in some aspects, CryLocker is pretty conventional when it comes to its core functions.
There's a new family of ransomware out there, and its name is CryLocker. CryLocker was discovered at the beginning of the month by computer security researchers who call themselves the MalwareHunterTeam. Since then, numerous other experts have dissected the code, and they've come to the conclusion that in some aspects, CryLocker is pretty conventional when it comes to its core functions.
The ransomware was initially named after the Central Security Treatment Organization – the fake institution it claimed to represent. The CryLocker name was adopted on September 5th when a new version came out. However, frequent name changes and the use of non-existent law enforcement agencies to scare people into paying the ransom are not uncommon in the world of malware.
The infection vector for CryLocker is fairly traditional as well. At first, CryLocker infiltrated systems via the Rig exploit kit, but the most recent versions use Sundown. Surprisingly , there are no records of this particular ransomware being distributed through spam emails.
Like all other threats of this type, once it initializes, the malware will encrypt most of your files (no less than 667 extensions are targeted), and it will later demand a ransom of 1.1 Bitcoins or about $666 at the current rate to restore access to the data. The files get a .cry extension, and the shadow copies are deleted, which means that retrieving the information with the help of System Restore is not possible. For the time being at least, there's no decryption tool available for free, either.
So far, there's nothing too unconventional about CryLocker. After digging deeper, however, the researchers found some interesting features.
As soon as it enters your system, CryLocker will start gathering detailed information about your computer . Things like the Windows version and the username will be collected and sent to over 4,000 IPs (one of which presumably belongs to the Command & Control server). The ransomware will also place the information in a fake PNG file, and it will try to upload it to Imgur. If Imgur rejects it, the file will be sent to Pastee, which is one of the many legitimate services used by CryLocker.
While it's scouring for information, CryLocker will also try to collect details about the PC's wireless access point, and it will connect to Google Maps' Geolocation API. Researchers are still not sure why it would do that, but they assume that with these details, the perpetrators will manage to show victims that they know the physical location of the infected system, thus increasing the scare factor. All communication with the outside world is done via the UDP protocol instead of the more commonly used TCP.
Certain users might get infected with CryLocker and still end up having their files left intact. The ransomware will look through the keyboard settings of the infected computer. If the system is setup to work in Russian, Belarusian, Kazakh, Ukrainian, or Uzbek, the ransomware will not proceed with the encryption and will automatically remove itself.
While CryLocker remains to be somewhat of a mystery, it is a clear look into the future evolution of ransomware giving us a glimpse of its potential through the utilization of third party sources. Such actions could eventually be used to infiltrate vulnerable computers more effectively.