COVID-19 Cybercriminal Scammers are Recycling Phishing Kits
 Phishing attacks looking to take advantage of fears around the COVID-19 pandemic are becoming more prevalent across the board. Cybercriminals are apparently trying to cut down on the work by using older phishing kits to do most of the effort for them. Older phishing kits are being deployed when they were previously retired. They're being used due to the massive number of people now working from home.
Phishing attacks looking to take advantage of fears around the COVID-19 pandemic are becoming more prevalent across the board. Cybercriminals are apparently trying to cut down on the work by using older phishing kits to do most of the effort for them. Older phishing kits are being deployed when they were previously retired. They're being used due to the massive number of people now working from home.
This Week In Malware Ep 11: Hackers Thrive on Covid-19 Themed Ransomware & Malware Attacks
Millions of people across the world are telecommuting or being stuck at home and on the internet, since the mandatory lockdown policies are becoming widespread. Phishing attacks and threat actors are using this opportunity to use a range of attacks, from SMS text messages to emails and more. They're directing these attacks with attempts to look like COVID-19 news, updates from the government or health products and services.
Scams and phishing schemes are gaining traction
With the latest attacks the victims are being fooled with link redirects to malicious websites or spoofs of legitimate websites like eBay, Orange France or Microsoft. The attackers are also focused on imitating official sources on the pandemic like the World Health Organization or local medics.
The scammers often pretend they're an insurance company, a bank or a medical expert to build trust with the victims, creating an opportunity to strike in the process. Once a level of trust has been established, the criminals attempt to convince the victims to open malicious attachments, follow malicious links or to share personal information. That allows the attackers to gain access to banking information, critical services and applications.
Although most of the URLs are newly created, since there are dozens of new Coronavirus-related domains deployed daily, the phishing kits that work in the background are being reused to cut down on development.
In February, 19 new domains were using one phishing kit, a reused tool. During March, 43 of the new domains were using recycled phishing kits. In the first two days of April, 26 new domains were using recycled kits. The repurposing and recycling of the phishing kits makes the job of those defending against them slightly easier.
COVID-19 theme growing more prevalent in cybercrimes
The Coronavirus pandemic has emerged as the primary theme in cybercrime this year. As the infection spreads in the physical world, so does a digital version of it in the electronic one.
In a single week alone, the Nokia Threat Intelligence Lab analyzed new campaigns using a Trojan targeting Windows, mimicking a map with confirmed COVID-19 cases. Other examples found were CovidLock, an Android ransomware that pretended to give users ways to spot nearby COVID-19 patients. Nokia also noticed a safety-mask SMS scam, using an app that pretended to help users find masks, when in reality reaping contacts and SMS messages from infected devices.
One of the credentials phishing campaigns was spotted aimed at US healthcare and higher education targets, as well as information security companies. The message behind it claimed it was from their payroll departments. The emails were titled 'General Payroll !' and pushing a fake message saying the Trump administration is considering sending most Americans a check to stimulate the economy.
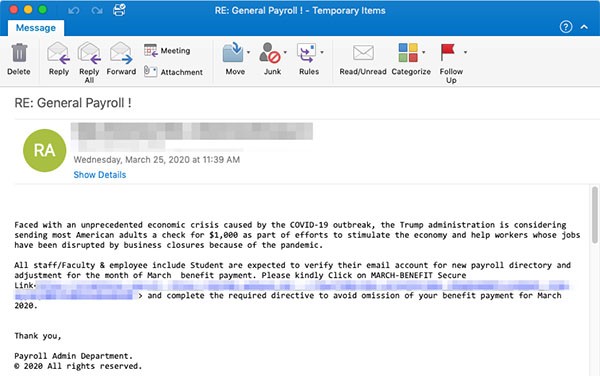
Example of COVID-19 Phishing email - Source: Threatpost.com
Researchers noticed the telltale signs of the scam: clear grammar and spelling errors and a basic web page design that was branded by a free website maker. The messages ask users to click a malicious link called 'MARCH-BENEFIT secure link' that sends them to a phishing page. The page asks for usernames, email addresses and passwords connected to their employee benefits.