Astaroth attacks are Becoming More Sophisticated, Microsoft Warns
 Following a slow in activities, the info stealer Astaroth is back, according to Microsoft. Astaroth came back in early February, wielding improved capability in its attack chain. The malware employs fileless techniques as well as various methods of trying to run undetected. The new and improved attach chain maintains the complexity of previous versions, with multiple components and improved evasion capability.
Following a slow in activities, the info stealer Astaroth is back, according to Microsoft. Astaroth came back in early February, wielding improved capability in its attack chain. The malware employs fileless techniques as well as various methods of trying to run undetected. The new and improved attach chain maintains the complexity of previous versions, with multiple components and improved evasion capability.
Astaroth works by only using system tools already in existence on machines it infects, attempting to avoid detection without downloading additional modules. That resulted in a marked increase in Windows Management Instrumentation Command-line (WMIC) activities that led to Microsoft's investigation.
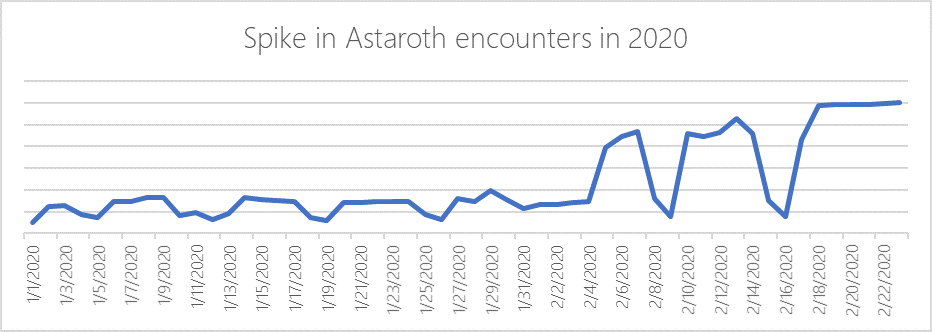
Microsoft Defender ATP data showing Astaroth activity is on the rise again. Source: Microsoft
Astaroth is now avoiding the use of WMIC entirely to bypass the detections. The attackers behind it have moved on to new techniques to make their creation even stealthier by using ADS (Alternate Data Streams) to hide its malicious payloads. It was also improved by using the legitimate process ExtExport.exe to do the same.
Table of Contents
Taking the new Astaroth apart
The attackers were ensuring the updates to their malware weren't making it easier to detect. With the significant changes in using Alternate Data Streams (ADS), Astaroth now abuses systems at several stages. ADS allows users to attach data to existing files, with the stream data and size not visible in File Explorer. Attacks of this kind are hiding their malicious code in plain sight. In this specific case, they were hiding the binary data inside the ADS of desktop.ini, all without changing the file size. Doing it allowed them to create a staging ground for the downloads, which are read and decrypted as they arrive. That complex attack chain allows the eventual loading of Astaroth straight into memory. When the malware is running, it decrypts plugins that allow it to steal sensitive data.
ADS (Alternate Data Stream) abuse
For each download, the content ends up copied to the ADS. The original content deletes itself as part of the process. These actions repeat for every downloaded payload. Another action Astaroth takes that abuses ADS happens when it runs a script to check for security products. A malicious script checks for that kind of software, and it ends up copied as ADS in an empty text file.
ExtExport.exe abuse
The malware uses a living-off-the-land binary (LOLBin) not previously seen to load its first stage malware code. Using ExtExport.exe allows attackers to use this legitimate utility to load any DLL that passes to the attacker-controlled path to the tool. The tool is made to look for DLLs bearing the following names: mozcrt19.dll, mozsqlite3.dll, or sqlite3.dll. The attackers have to rename the malicious payload to one of the said names, which forces ExtExport.exe to load it.
Userinit.exe abuse
The newly loaded DLL is a proxy, one that reads binary ADS streams (desktop.ini:masihaddajjalxa.~, desktop.ini:masihaddajjalxb.~, and desktop.ini:masihaddajjalxc.~) and combines them into a DLL file. This newly formed DLL is the second stage of the malware code. The DLL file also acts as a proxy, reading and decrypting another ADS stream: (desktop.ini:masihaddajjalgx.gif) into another DLL. That DLL is then injected into userinit.exe.
The newly loaded DLL inside userinit.exe also acts as a proxy that reads and decrypts another ADS stream (desktop.ini:masihaddajjalg.gif) into a DLL. This last DLL is Astaroth itself, loaded inside userinit.exe. That allows Astaroth to avoid appearing anywhere as a file, loading itself directly into memory.