What Does DDoS Stand For?
What Does DDoS Stand For? Image
A Distributed Denial-of-Service (DDoS) attack is a malicious attempt to disrupt the traffic of targeted servers, network, or service by overwhelming the targets or surrounding infrastructure with a flood of Internet packets. DDoS attacks are capable of utilizing multiple compromised computer systems as sources of the attack's traffic. Machines exploited in the process may include computers and IoT devices networked to the victim. On a high level, the DDoS attack acts by jamming up internet traffic, preventing it from arriving at its desired destination by flooding the target with junk data.
Table of Contents
How does a DDoS attack work?
A DDoS attack needs an attacker gaining access to a network of devices to carry out the attack. IoT devices, computers, and other machines get infected with malware, making each one of them into a bot. The attackers then gain control over the botnet, using it to further their goals. Once the botnet is established, the attackers can direct devices through updated instructions to each of the bots by remote. When the botnet targets the IP address of a victim, each of the bots responds by sending requests to the target, clogging up the network or server to overflow capacity, resulting in abnormal traffic levels. Differentiating between attack traffic and regular traffic can be difficult due to the nature of the infected devices.
What Methods are Used in a DDoS attack?
Different DDoS attack vectors may go after various components of computer networks. To better understand the inner workings of DDoS attacks, one needs to know how systems are connected. A network connection depends on different layers, with each layer having a different purpose. The OSI model in the following figure shows a concept for the framework used in computer networks, comprised of 7 separate layers:
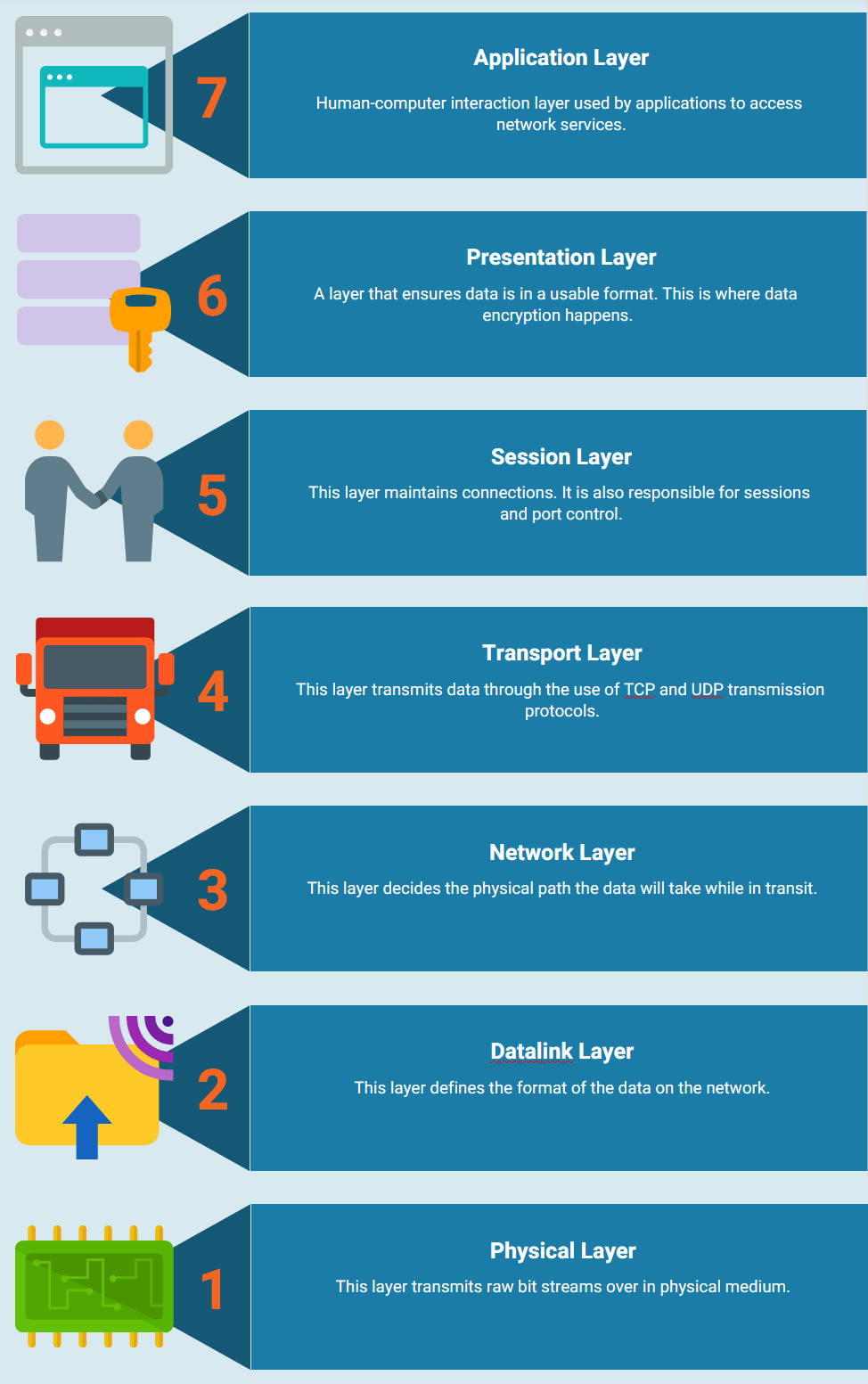
Although almost all DDoS attacks use overwhelming tactics on a device or network, these attacks can be subdivided into three categories. Attackers may take one route or multiple routes with different attack vectors, or cycle them to keep the defenders off-balance for as long as possible.
Application Layer Attack
The point of this type of attack is to exhaust the resources of the chosen target. The attacks target the layer where web pages are generated on a server and delivered in response to HTTP requests. A single request is easy to execute on the client-side, but it may be taxing on the system for the target server to respond to multiple requests as the server needs to load files and run database queries to show the web page. Application layer attacks are difficult to counter, as the traffic may be hard to track down as malicious. Examples of an Application Layer Attack can be seen with the following:
HTTP Flood
An HTTP flood is an attack similar to refreshing a browser page again and again on a massive number of machines simultaneously. A large number of HTTP requests overwhelm the server, stalling it and resulting in a denial-of-service situation. This type of attack can range from a simple implementation of one URL with the same range of attacking IPs to more complicated versions with a large number of attacker IP addresses, using random URLs, referrers and user agents.
Protocol Attacks
A protocol attack aims to cause a service disruption by consuming all available state table capacity for web application servers or the immediate resources like load balancers and firewalls. Protocol attacks focus on weaknesses found in layers 3 and 4 of the protocol stack to render the targeted system inaccessible. Examples of protocol attacks can be seen with SYN floods.
SYN flood attacks exploit the TCP handshake by sending off many TCIP initial connection request packets using spoofed IP addresses. The targeted machine responds to the connection requests and then waits for the final step of the handshake. When that never happens, it exhausts the targeted system's resources as a result.
Volumetric Attacks
Volumetric attacks attempt to create congestion in traffic by consuming the available bandwidth between the larger internet and the target. Large data packets are sent to the target using amplification or other means, such as requests from an existing botnet. Examples of that can be seen with DNS amplification.
DNS amplification
DNS amplification attacks are used to request to open DNS servers using a spoofed UP address. The attacker requests in such a way that the DNS server responds with a large amount of data, sending an amplification of the initial query of the attacker.
What Can Be Done to Mitigate a DDoS Attack?
The significant worries regarding the mitigation of a DDoS attack lie in differentiating between regular and malicious traffic. On the internet, DDoS traffic may come in many shapes. The traffic varies in design, such as single source attacks to adaptive attacks taking on multiple vectors to succeed. The latter uses these methods to overwhelm targets in different ways, distracting the mitigation efforts of any single trajectory. Attacks that target multiple layers can stack, such as DNS amplification combined with HTTP floods. The more complex the attack pattern, the harder it will be to separate regular traffic from malicious traffic. Mitigation may involve a layered approach toward the threat as the best way to deal with it. The following methods may be used in the process:
Black Hole Routing
One of the solutions is to create a blackhole route and to funnel traffic into the route. When the blackhole filter is implemented without restriction criteria, both malicious and legitimate traffic will be routed to a null route, dropped from the network. If an internet property is experiencing a DDoS attack, the internet service provider (ISP) may send the traffic into a blackhole to deal with the situation.
Rate Limiting
Limiting the requests a server accepts over a time frame is another way to deal with a DDoS attack. The rate-limiting approach is useful in slowing down web scrapers from getting away with valuable data and counteracting brute force login attempts, but it alone won't have the necessary effect to deal with sophisticated DDoS attacks.
Web Application Firewall
A Web Application Firewall (WAF) is a tool used to assist in stopping a layer 7 DDoS attack. Putting a WAF between the internet and the origin server allows the WAF to act as a reverse proxy, guarding the targeted server against some types of malicious traffic. Filtering requests allow layer 7 attacks to be slowed down or stopped. One of the advantages of having WAF is to implement custom rules as an attack unfolds.
Anycast Network Diffusion
This mitigation method uses an Anycast network to disperse the traffic across a network of distributed servers, essentially absorbing the impact of the attack. The Anycast network used to mitigate may have varying results, depending on the size of the attack and the efficiency of the network.