Slocker Android Ransomware Emerges as a WannaCry Lookalike
 TrendMicro researchers have recently spotted a new variant of Slocker, the first Android ransomware which struck first in the summer of 2016 before resurfacing with more than 400 modifications in May 2017. The new Slocker incarnation, which reportedly came up in early-June 2017, is the first to utilize a graphical user interface which bears a striking resemblance to that of the infamous WannaCry ransomware. A desperate attempt at capitalizing on the name of the latter, which failed to make a significant impact in the end.
TrendMicro researchers have recently spotted a new variant of Slocker, the first Android ransomware which struck first in the summer of 2016 before resurfacing with more than 400 modifications in May 2017. The new Slocker incarnation, which reportedly came up in early-June 2017, is the first to utilize a graphical user interface which bears a striking resemblance to that of the infamous WannaCry ransomware. A desperate attempt at capitalizing on the name of the latter, which failed to make a significant impact in the end.
Table of Contents
Infection Vector
Advertised primarily via Chinese QQ and BB forums, Slocker showed up on third-party app stores under various guises as a multimedia player, a game cheating tool, or any other feature-heavy app interesting enough to draw users' attention. Those who downloaded a video player or a game cheating tool seemingly got what they were looking for – an icon showing a video player or a cheating tool. As it would turn out later, neither the icon, neither the name was legitimate. As soon as users clicked on the icon of the downloaded app, it changed immediately, along with the name of the app and the wallpaper of the Android device.
Once launched, Slocker executed its payload in the background.
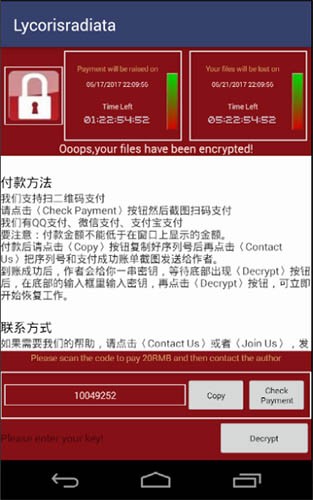
Slocker's Lock Screen and icons before and after launch - Source: TrendMicro
The Encryption Process
Unlike its earlier versions which only targeted user data only stored in the internal memory of the infected device, the new Slocker attacks external storage, as well. What is more, Slocker only encrypts documents, pictures, and videos sized between 10KB and 50MB, while Android system files remain intact.
Before any encryption takes place, however, Slocker generates a random number, puts it deep inside the mobile OS and subsequently uses this number (and its MD5 in particular) to build the final AES encryption. All encrypted files get a new extension consisting of a QQ number combined with the random number. When the whole encryption process is complete, Slocker opens a new window providing three different payment methods – Alipay, WeChat or QQ – all leading to one and the same QR code requiring payment through the QQ mobile payment service. Although TrendMicro's report on Slocker does not contain any exact figures, it does reveal a three-day promotional offer giving victims the opportunity to get away with a reduced ransom amount. Should they refuse to accept the offer, the required payment amount goes up for the next four days. In case no payment takes place within those seven days, infected users faced total data loss.
Slocker’s Ultimate Failure
As dangerous as it may have seemed at the beginning, Slocker has failed to do any severe damage due to its:
- weak encryption algorithm
- Sparse distribution heavily dependent on Chinese QQ and BB forum groups
When it first showed up on June 2, 2017, this WannaCry lookalike applied an AES encryption based on the MD5 of the aforementioned random number. However, it only took security researchers one day to break it. They released a fully-functioning decryptor for this particular Slocker variant on June 3 after finding out it had a linear correlation with the random number:
Decryption Key = Random Number + Constant
Slocker Random Number and Decryption Key image - Source: TrendMicro

The June 2 Slocker variant had a random number of 10049252, a constant of 520, and its decryption key was 10049772. Even though the subsequent Slocker variants which sprang into existence over the next few hours more or less tweaked their decryption patterns, they could still be broken relatively easy, security engineers say.
On the other hand, placing Slocker on a couple of Chinese forums helped to restrict the geographic exposure of the malware and narrowed down the search for the perpetrator(s). On June 7, the Chinese police apprehended the actor behind the extortion mobile crypto-virus. However, they have yet to track down the crooks responsible for the remaining Slocker variants. Given that new mobile viruses are becoming increasingly common and sophisticated, it can only be a matter of time before we see enhanced forms of malware much harder to crack.