SeaChange video platform allegedly hit by REvil Sodinokibi Ransomware
SeaChange, a video delivery software company, was recently targeted by the operators behind the Sodinokibi ransomware. The attackers posted images of data they allegedly stole from the affected company during their operations.
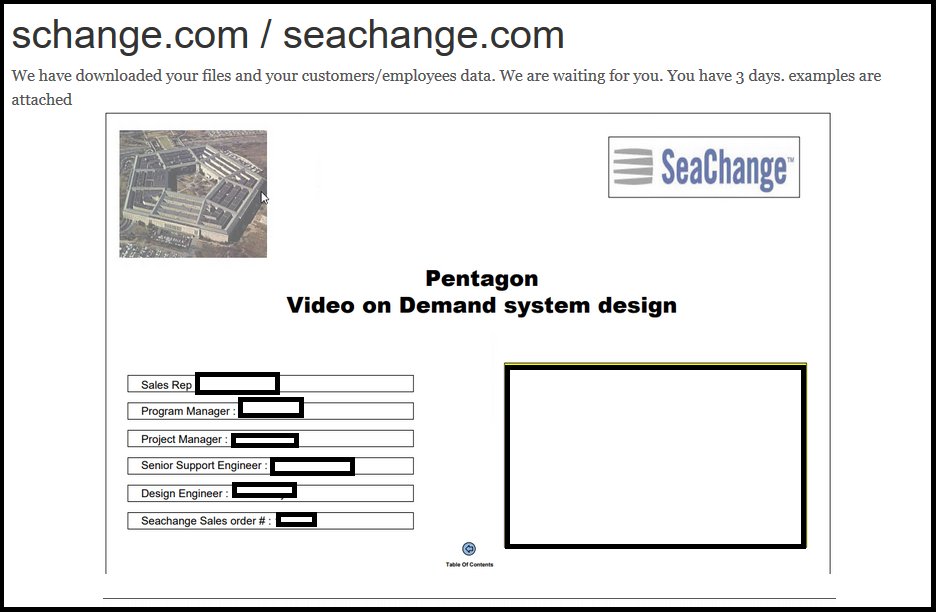
SeaChange bogus notification message
SeaChange is a company based in Waltham, Massachusetts, with offices in Brazil and Poland, working with video-on-demand and streaming. Their wide range of customers includes COX, DirecTV, DISH, Verizon, and the BBC. The company has been active on the market for 25 years, making it a lucrative target for threat actors and ransomware. Since last year, hackers have been launching websites where they publish data leaks stolen from victims, making the publications when they refuse to pay ransom demands. This tactic has been used successfully by criminals to show the victims they mean business and to extort targets.
This Week in Malware Ep7: Revil Ransomware Attacks High-Profile-Client Law Firm
Sodinokibi posted SeaChange data images
REvil, the group behind the Sodinokibi ransomware, made an update on their data leak website. The SeaChange victim page shows images of documents they claim they have stolen from the company during an attack.
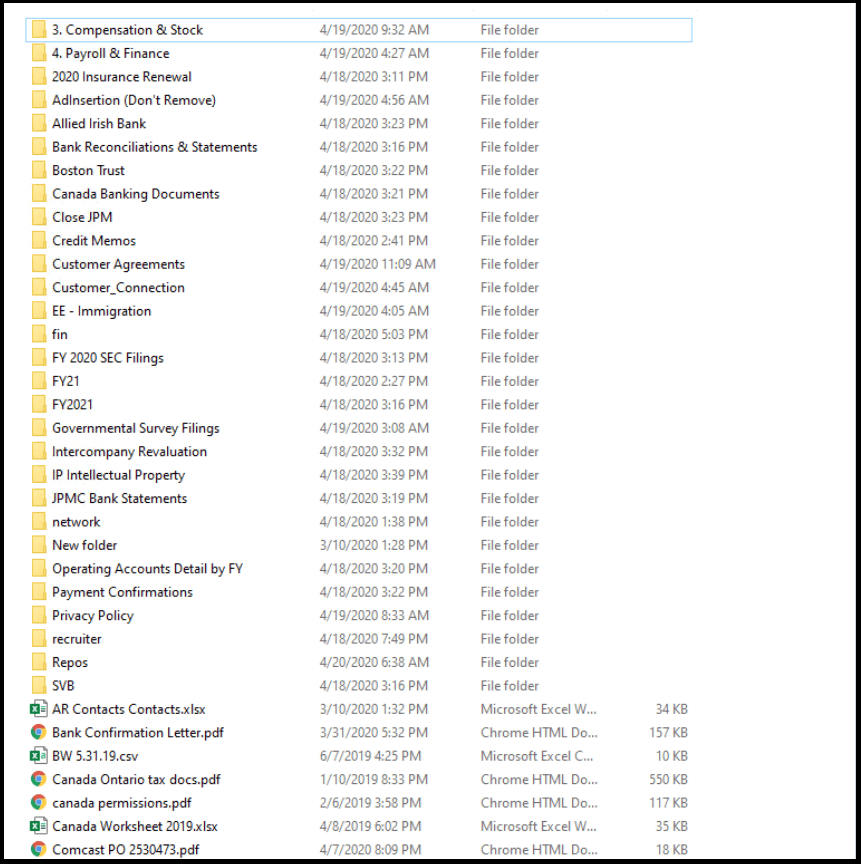
Screenshot of folders listed on server that threat actors have access
The images showed screenshots of folders on a server where the threat actors allegedly have access. Details show a driver's license, insurance certificates, bank statements, and a cover letter for a video-on-demand service proposal for the Pentagon.
There were more documents, including payroll and finance information, customer agreements, payment confirmations, and more.
Sodinokibi operators threatened the company, saying they have 3 days to contact them.
Both the company and the ransomware operators didn't share details with researchers on the ransom data stolen by the attackers.
July 2021 Update Alert – REvil Ransomware Hackers Initiate New Attacks
REvil ransomware has jump-started a new cyber campaign by compromising Kaseya’s remote desktop software to spread. Using Kaseya’s software, REvil has hit over 200 US businesses including AT&T, Sprint, and Verizon, and over 40 customers worldwide. The attack was discovered on Friday, July 2nd, right before the July 4th holidays, making it less likely for companies to respond with countermeasures.
The timing couldn’t have been worse as the cyber campaign occurred during the July 4th weekend, won’t most employees, particularly the ones involved in IT, are not at work. Kaseya is trying to protect its customers' data. According to Kaseya CEO Armen Movsisian, the company is "working around the clock" on implementing solutions while working with law enforcement.
According to the report, the new campaign, known as a supply-chain attack, uses Kaseya's remote software to connect to computers and attempt to install REvil ransomware on them. At this point, it is unclear whether Kaseya's software was intended to be used by attackers for ransomware installation. Reports state that at least over 200 US companies have been affected by the hack.