Russian Cybergang Turla Introduces Revamped ComRAT v4
 After what appears to have been a three-year hiatus, Russian cyber gang Turla is back with a vengeance. This time, the crooks are deploying an enhanced variant of the good old ComRAT malware whose earlier incarnations have plagued state organizations since 2008. The newly detected attacks made no exception as they have reportedly struck at least three government entities in Eastern Europe and Caucasia in January 2020. While the exact extent of the inflicted damage remains unknown, Turla has likely managed to get a grip on sensitive data and place them on cloud-based services such as 4Shared and OneDrive.
After what appears to have been a three-year hiatus, Russian cyber gang Turla is back with a vengeance. This time, the crooks are deploying an enhanced variant of the good old ComRAT malware whose earlier incarnations have plagued state organizations since 2008. The newly detected attacks made no exception as they have reportedly struck at least three government entities in Eastern Europe and Caucasia in January 2020. While the exact extent of the inflicted damage remains unknown, Turla has likely managed to get a grip on sensitive data and place them on cloud-based services such as 4Shared and OneDrive.
Launched in 2017, ComRAT v4 Is Now Spiced Up
The current fourth generation of the ComRAT dates back to 2017. However, the ComRAT v4 malware used in the Caucasian strikes in January 2020 sported a couple of features never seen in earlier ComRAT variants.
On the one hand, the new, spiced up ComRAT v4 retrieves the AV log data from each infected machine. That serves two purposes. First, it allows Turla’s hackers to see whether or not ComRAT v4 (2020) can pass through antivirus software unscathed. Second, those data can bring about changes in the malicious code to evade possible detections elsewhere.
On the other hand, the January 2020 ComRAT v4-related incidents were the first to feature a second Command-and-Control (C&C) server. In addition to the conventional remote HTTP server, Turla’s actors now hacked into the victim’s Gmail account to allow ComRAT to read emails, download the malicious attachment(s) contained therein, and execute whatever instructions the latter may provide. Having control over the victim’s Gmail allows the crooks to send (and carry out) additional ComRAT commands at their discretion. The flowchart below, which was developed by ESET, provides a detailed overview of the process.
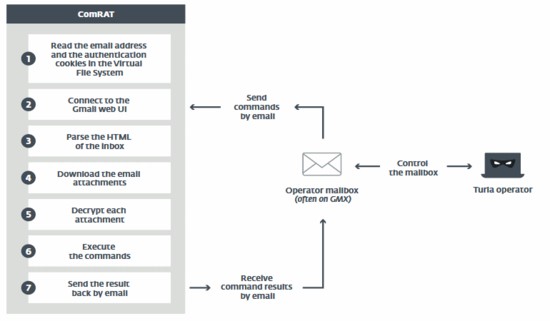
Image source: ZDNet
Chronological Round-up
Formerly come to life as Agent.BTZ, ComRAT is a shining example of what Remote Access Trojans do when they infiltrate a targeted computer network. Presumably compiled in 2007, ComRAT v1 gained notoriety for hacking the Pentagon – the heart of the U.S. Department of Defense – in 2008. The perpetrators - a suspected gang of Russian hackers – reportedly used an external USB stick to plant ComRAT v1 (and the worm it carried along) across the entire network, potentially exposing classified operational data relating to the government’s endeavors in the Far East. The breach was so critical it called for sweeping reforms in U.S. cybersecurity.
The success of the Pentagon attack spawned three more ComRAT versions. ComRAT v2, ComRAT v3 came out in 2008, 2012, respectively. Although v2 and v3 did not differ much from v1, it was v4 that underwent a complete overhaul in 2017. Yet, the main goal pursued by the actors behind ComRAT – harvesting sensitive documents – remains the same to this day, despite the newly added features outlined above.