Researchers Dig Into Mole Ransomware Attack That Hit UK Universities
 On June 14, Ulster University and University College London reported that they have both been hit by what was described as a 'widespread ransomware attack.' The two institutions quickly put together response teams which set off to contain and remove the malware. Although the term 'zero day' was used rather lightly, the people tasked with fending off the attack did a good job overall. The first thing they did was to take the drives hosting shared information for students and teachers offline. Sadly, by that time, some of the data had already been encrypted.
On June 14, Ulster University and University College London reported that they have both been hit by what was described as a 'widespread ransomware attack.' The two institutions quickly put together response teams which set off to contain and remove the malware. Although the term 'zero day' was used rather lightly, the people tasked with fending off the attack did a good job overall. The first thing they did was to take the drives hosting shared information for students and teachers offline. Sadly, by that time, some of the data had already been encrypted.
There was good news, though. Both universities had fresh backups that weren't affected by the ransomware. Over the next few days, the response teams restored the information, made sure that the malware is well and truly gone, and on June 19, everything went back to normal.
At first, nobody knew the name of the ransomware that had hit the educational institutions, but the universities seemed pretty convinced that it had arrived via a phishing email. Later, however, University College London said that a drive-by download from a compromised website was a more likely infection vector. Indeed, it was.
A Proofpoint security researcher known as Kafeine was among the people who wanted to know more about the attack. He learned that the ransomware had communicated with a Command and Control (C&C) server hosted at 137.74.163[.]43 – an IP used by Mole, an offshoot of the CryptoMix ransomware family. He found a few samples on VirusTotal which carried file names that coincided with the payloads known to be dropped by the Astrum (a.k.a. Stegano) exploit kit. Later, the researcher learned that the universities' systems had also communicated with avia-book[dot]com shortly before the ransomware deployed. The avia-book[dot]com domain is associated with the AdGholas malvertising campaign which has been running rampant over the last few months. Kafeine had enough evidence to piece together the whole attack chain.
The method of attack looks like this:
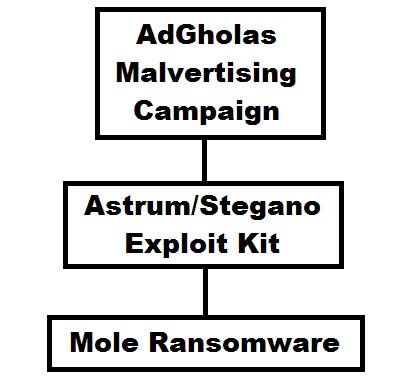
The fact that AdGholas was working with Astrum wasn't really surprising. Waves upon waves of malvertising coming from this particular crew have been observed extensively by Proofpoint and Trend Micro researchers over the last few months, and the ads always led to landing pages that belonged to Astrum. The surprising bit was the payload.
Ever since teaming up, the Astrum-AdGholas tandem has been in the business of distributing banking malware, with Ursnif and Ramnit being the most widely spread Trojans. It's the first time experts see the gangs blasting ransomware around. When we say "blasting," we mean it.
The universities were the high-profile targets that made the headlines, but according to Kafeine, a number of other users in the UK and US were hit by the same attack chain and the same Mole ransomware. In reality, it's bad news because as we mentioned in our previous article, Mole's encryption algorithm is strong, and the crooks have made it clear that they want 0.5 bitcoins (just under $1,400 at the current rate) for the decryption key.
The Mole ransomware incident might be a one-off for the people operating AdGholas and Astrum, and they could soon be back to pushing banking Trojans. Whatever they decide to distribute, however, they are going to spread it through a highly sophisticated, proven network of malicious advertisements and exploits which is why users should probably think about an ad-blocker and patching their software regularly.