Locky Ransomware Distribution Network Attacked to Strip Threat of Encryption Abilities
 Ransomware threats like Locky have been a major disruption for countless computer users who have had their system's files encrypted by the aggressive malware. In light of the destructive nature of Locky Ransomware and its file encryption abilities, an unknown entity has hacked the distribution network, or botnet, used to spread the Locky Ransomware threat. They have attacked the network in a way that essentially decontaminates the Locky Ransomware threat stripping its ability to encrypt files where it will only display a warning notification.
Ransomware threats like Locky have been a major disruption for countless computer users who have had their system's files encrypted by the aggressive malware. In light of the destructive nature of Locky Ransomware and its file encryption abilities, an unknown entity has hacked the distribution network, or botnet, used to spread the Locky Ransomware threat. They have attacked the network in a way that essentially decontaminates the Locky Ransomware threat stripping its ability to encrypt files where it will only display a warning notification.
Distribution networks are often referred as being a botnet, which is a group of compromised computers that have been infected with malware that receives instructions to carry out from a command and control server. In the light of how ransomware threats like Locky primarily spread, they usually have a botnet send out spam emails to countless computer users that all include a malicious attachment file that will ultimately load the ransomware threat if opened.
First discovered and reported by the security firm F-Secure, is a satiation where the Locky Ransomware threat was found to lack its encryption payload leaving it bear with the function of only displaying a warning notification. The warning message left on the stripped version of Locky is one that attempts to warn computer users that they should not open unknown email attachments. Furthermore, the benign threat fails to perform any actions that Locky Ransomware is known for, which includes its action of encrypting files and holding an infected system for a ransom fee.
The Locky Ransomware threat that was stripped of its original functions is peddled in the same manner where it is included as a spam email attachment within a ZIP archive containing a JavaScript file. Users that open up the ZIP file and then double-click on the JavaScript file will launch the benign Locky Ransomware threat, which will display the warning message.
We believe that the message that the benign Locky Ransomware threat is attempting to communicate is one to forewarn computer users of the dangers they face when opening up email attachments from unknown sources.
Looking into how a recent ransomware threat was stripped of its functionality the folks at F-Secure are sure of the distribution network for Locky was hacked. As it turns out, the practice of hacking malware botnets and replacing their payloads with other content is becoming a common action. Moreover, the practice of replacing the payload of a malicious threat with pro-user content appears to be the commonplace practice of hackers looking to overshadow the success of other malware creators.
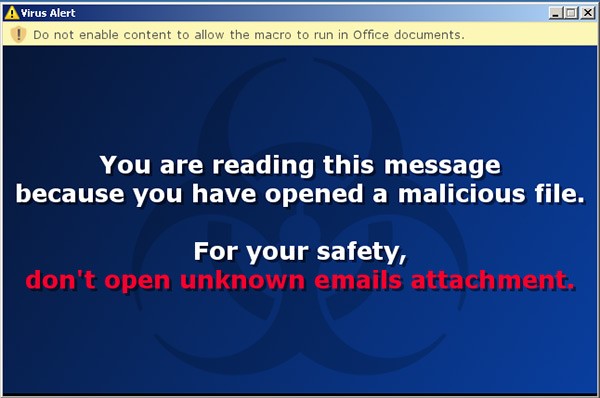
Those who encounter the benign version of Locky Ransomware will take notice to its alert message, which is shown in figure 1 below and reads: You are reading this message because you have opened a malicious file," the popup reads. "For your safety, don't open unknown emails attachment."
Figure 1. Benign version of Locky Ransomware notification pop-up – source: F-Secure
While the recent stripping of functions from Locky Ransomware is not the first time a malware threat was replaced with different functions by alleged hackers, it demonstrates a growing technique that prevails for some in the task for reverse engineering malware threats. Additionally, computer security experts and researchers may find such a technique to be beneficial in the long run as aggressive malware threats are essentially sterilized to become ineffective.