How Hackers Use Cryptojacking Malware to Take Over Computers to Mine Cryptocurrency
 We all know the term "carjacking" and the unfortunate circumstances that such an act entails. With the evolution of the Internet and formation of a technologically-driven society, we're in a perpetual battle to protect our personal data and our commonly-used devices. In the quest for hackers to leverage any vulnerable system and ultimately make money, they have formed an alliance to attack computers in a way to turn them into zombies and mine cryptocurrency.
We all know the term "carjacking" and the unfortunate circumstances that such an act entails. With the evolution of the Internet and formation of a technologically-driven society, we're in a perpetual battle to protect our personal data and our commonly-used devices. In the quest for hackers to leverage any vulnerable system and ultimately make money, they have formed an alliance to attack computers in a way to turn them into zombies and mine cryptocurrency.
With the cryptocurrency craze at an all-time high, we're not all surprised that hackers are taking over computers to mine cryptocurrency, a process aptly dubbed cryptojacking, which will earn hackers unthinkable amounts of cryptocurrency funds (virtual money) in the long run.
This Week In Malware Ep 13: Glupteba Cryptojacking Malware Becomes Unstoppable
Table of Contents
What is Cryptojacking?
Cryptojacking, as the name suggests, is a process of 'hijacking' or overtaking certain functions of a computer and using it to mine cryptocurrency. As simple as it sounds, there is a vast amount of complexity to the matter.
Hackers are steadily creating new types of threats, most of which are Python-based malware bundled up in a single malicious executable file. These new threats, some that go by the name of WannMine, PyRoMine, or Monero Miner, are designed to take over specific functions of an attacked computer and use the system's resources to mine cryptocurrency.
The process of mining cryptocurrency, such as Bitcoin, Ethereum, and Monero, to name a few, usually involves a dedicated computer unit, typically a computer directed from a graphics card setup, which utilizes a great deal of energy and CPU (Central Processing Unit) power. In the case of victimized PCs infected with cryptojacking malware, the system may be nearly useless for carrying out basic functions as the threat will use most, if not all, of the CPU resources to mine cryptocurrency. Mining cryptocurrency is a process that requires high-level computations to be performed repeatedly granting the miner portions of Bitcoins, Monero, or Ethereum funds. Such funds in the cryptocurrency world may be "cashed in" for other types of money, which is the ultimate attraction for hackers who look to 'Cryptojack' your computer.
How Cryptojacking Works
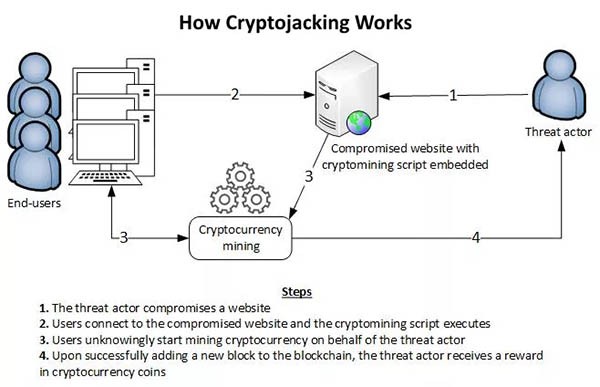
The image (Figure 1) below on 'How Cryptojacking Works' is a simple illustration by the European Union Agency for Network and Information Security giving us a visual representation on how a cryptojacking scenario takes place. First, a computer user accesses a website that has been compromised with cryptomining script. From there, the embedded script code on the malicious or compromised site may load or install the cryptojacking malware, which will in return start actively mining for cryptocurrency over the Internet on behalf of the threat actor, or hacker. The process of mining cryptocurrency will add a new blockchain with each successful action through solving computations as a part of cryptocurrency mining. As such, the reward is cryptocurrency coins that the threat actor or hacker can then cash-in whenever they desire.
Figure 1. Diagram flow-chart of how cryptojacking works. Source: European Union Agency for Network and Information Security (ENISA)
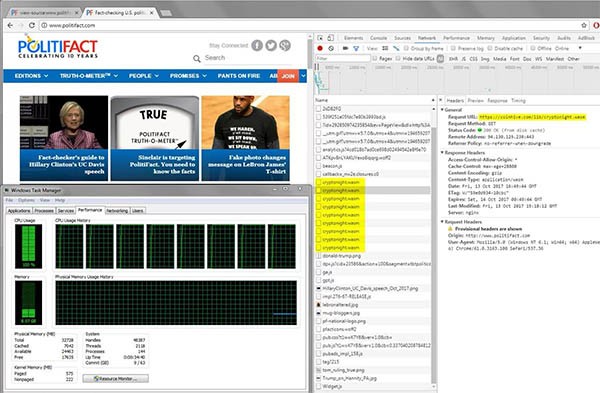
Just last year, during the months of October and November, cryptojacking scripts affecting mobile devices increased by 287%, according to analysis by the mobile security firm Wandera. The most troubling part of cryptojacking is the idea of it spreading through websites, ones that have been hacked and injected with malicious script code that ultimately affects a computer visiting a specific site, such as show in Figure 2 below of the Politifact site's CDN (Content Delivery Network) source code demonstrates. Sites known to have spread such malicious code are numbered in the thousands, including countless porn sites and CDN services that help render many popular sites. The following notable sites, some of which are still actively infected, are known to have cryptojacking source code embedded that may have originated from a hacked CDN service at one time:
- analytics.blue
- cbs.com
- coinhive.com
- cdn.static-cnt.bid
- cdn.jquery-uim.download
- cnt.statistic.date
- crucial.com
- cryptoloot.pro
- everlast.com
- globovision.com
- hallaert.online
- movistar.com
- minr.pw
- politifact.com
- showtime.com
- ufc.tv
- webmine.pro
Figure 2. Website Politifact shown with coinhive cryptojacking source code after compromise of it's CDN service. Source: Badpackets.net
Note: While many of the popular websites listed above were found to have embedded cryptojacking code at some time, some of the sites may have addressed the issue or the Content Delivery Network has taken action to stop the nefarious uses of Coinhive and injected malicious scripts. However, most of the companies who have sites leveraged by crypojacking have yet to issue any statements or make claims to being free from cryptojacking code. We urge users to utilize caution when visiting any of the sites listed above.
Video: “Cryptojacking: How your PC can be hacked to mine cryptocurrencies”
How to Detect Cryptojacking Malware
The detection of cryptojacking can be a difficult process unlike knowing that your system is infected with ransomware that outwardly displays a ransom note across your screen alerting you of the issue and its demands. Cryptojacking, in all its newness, is not something that you want to leave in the hands of a conventional anti-malware tool. However, there are clear indications that are a give-way of cryptojacking, such as your computer running slow, the CPU cooling fans speeding up and staying at high speed for a long period, your computer becomes unresponsive, or you notice a spike in network traffic accessing the Internet. Monitoring your system is your best practice in detecting cryptojacking, in addition to knowing your computer's normal behavior to contrast a case where a cryptojacking threat is utilizing a significant amount of CPU resources.
How to Prevent Cryptojacking Malware
In a simple answer to those who wonder if there is a solution to cryptojacking, the answer remains a resounding no. However, there are steps to take to be proactive about avoiding being a cryptojacking victim. Running an updated anti-malware or anti-virus application is your first line of defense along with avoiding malicious sites or ones that may have been hacked. Moreover, evading malicious downloads from questionable sources and limit opening any spam email messages that have attachments is also a method of staying out of the target or cryptojacking hackers.
The process for cryptojacking threats to spread appears to be mostly limited to hacked websites that harbor malicious JavaScript code. The simple process for stopping a cryptojacking attack that initiates from a malicious website is to simply kill the browser tab that is running the script. Though, the tricky part is preventing an attack from the same malicious URL or a similar one running a malicious script. Computer users may update a web filter to block the known malicious URL or utilize anti-crypto mining tools, which may be difficult to find at the moment due to the newness of cryptojacking attacks.
Additional actions computer users can take to limit or reduce the chances of being a victim of cryptojacking is to update and purge all browser extensions. Seldom some browser extensions may be the culprit of a cryptojacking attack, which is more reason to go through the list of installed extensions and remove any unnecessary extensions or ones that are questionable. Lastly, it's best that computer users adapt and be in the know of cryptojacking attacks to better understand how hackers compromise their systems, in addition to always keeping your software updated and running a copy of trusted anti-virus/anti-malware software.
How Do You Know if You’re a Victim of Cryptojacking?
Because the process of cryptojacking involves a specialized form of malware using a large amount CPU resources, most will immediately know if such an attack when their system runs extremely slow. However, there may be cases of cryptojacking threats not having such a drastic impact on a computer that has a powerful and fast CPU. An example would be a newer PC that has a quad-core processer or better, which for all intents and purposes, is not immune to such an attack.
The main goal for hackers who wield cryptojacking threats is to overtake a vulnerable system that is powerful enough to mine cryptocurrency, which usually doesn't yield a lot of cryptocurrency funds. Though, there are other forms of cryptojackers apart from the traditional form of executable files, which can be parasitic malware or threats that rely on malicious JavaScript code that's hidden on websites. At times, computer users may be infected with parasitic malware and not know it until their system finally slows down in response or returns an error due to lagging CPU or GPU (Graphics Processing Unit) cycles.
Because cryptojacking hackers aren't targeting any of your banking accounts or resources outside of your physical computer's computational abilities, cryptojacking isn't as severe as some may think. Though, one would conclude that cryptojacking is very dangerous when it comes to your computer's health and utilizing a significant amount of energy and Internet traffic.
The consequences of being a victim of cryptojacking can propagate into the following:
- An abnormally high electric bill.
- A higher-than-normal Internet service bill due to high traffic use.
- Drastically reduced computer performance.
- Consistently high computer cooling fan-speeds.
- System overheating or overheating errors.
- System errors due to lagging processing cycles or inability to run additional applications.
- Higher-than-normal Internet traffic through monitoring.
- System crashes or blue screens of death.
Considering your victimized PC will be the culprit such unfortunate cases, in the end, it's best to keep tabs on the health of your computer and ensure it has a clean bill of health, just as you would with your body.