CrypMIC Ransomware Attempting to Cash-In on CryptXXX's Success
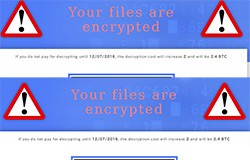 The ransomware sector is more active than ever, and that's more than obvious considering there are new threats unleashed daily. The reason for this is simple – ransomware has proved to be very lucrative for malware authors and hard to combat for victimized computer users. One of the biggest threats in recent months is the CryptXXX family of ransomware. Its malvertising campaigns have proved to be such a big success that it has been targeted by a copycat. The CrypMIC ransomware is trying to cash in on the success of CryptXXX and is doing a pretty good job imitating it thus far.
The ransomware sector is more active than ever, and that's more than obvious considering there are new threats unleashed daily. The reason for this is simple – ransomware has proved to be very lucrative for malware authors and hard to combat for victimized computer users. One of the biggest threats in recent months is the CryptXXX family of ransomware. Its malvertising campaigns have proved to be such a big success that it has been targeted by a copycat. The CrypMIC ransomware is trying to cash in on the success of CryptXXX and is doing a pretty good job imitating it thus far.
The similarities start with the distribution method. Both the CrypMIC and the CryptXXX ransomware utilize the Neutrino exploit kit, which takes advantages of Java and Flash Player vulnerabilities. The similarities continue with the ransom notes, which are almost identical. Here is the full text of the CrypMIC ransom note:
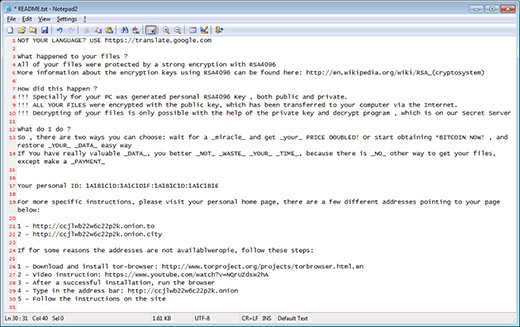
NOT YOUR LANGUAGE? USE https://translate.google.com
What happened to your files ?
All of your files were protected by a strong encryption with RSA4096
More information about the encryption keys using RSA4096 can be found here: http://en.wikipedia.org/wiki/RSA_(cryptosystem)
How did this happen ?
!!! Specially for your PC was generated personal RSA4096 Key , both public and private.
!!! ALL YOUR FILES were encrypted with the public key, which has been transferred to your computer via the Internet.
!!! Decrypting of your files is only possible with the help of the private key and decrypt program , which is on our Secret Server
What do I do ?
So , there are two ways you can choose: wait for a _miracle_ and get _your_ PRICE DOUBLED! Or start obtaining *BITCOIN NOW! , and restore _YOUR_ _DATA_ easy way If You have really valuable _DATA_, you better _NOT_ _WASTE_ _YOUR_ _TIME_, because there is _NO_ other way to get your files, except make a payment
Your personal ID: -
For more specific instructions, please visit your personal home page, there are a few different addresses pointing to your page below: -Screenshot of the CrypMIC ransom note:
The HTML ransom notes and the demanded ransom amount are also identical. Moreover, both CrypMIC and CryptXXX use a custom Command & Control communications protocol and generate IDs for its victims employing the same structure. The reason for all these similarities is simple - CrypMIC is trying to imitate one of the most powerful ransomware families to discourage you from looking for a solution and push you into playing the ransom. As it is with most ransomware, however, paying the ransom doesn't guarantee that you will get your files back. CrypMIC ransomware also has another feature of CryptXXX. Both ransomware programs have data collecting capabilities, so your encrypted files may not be the only thing that is in danger.
The most obvious feature that sets CrypMIC apart from CryptXXX is that CrypMIC doesn't change the file extension, making it harder to find which files are encrypted. Then, there is the encryption method. CrypMIC uses an AES-256 encryption algorithm, while CryptXXX employs an RC4 and RSA combination. Also, we see that CrypMIC's campaigns have recently changed the exploit kit that they utilize.
Reports show that, after the Neutrino exploit kit campaign was taken down by GoDaddy and Cisco Talos, CrypMIC started using the RIG exploit kit, the most active one currently. With such occurrences, experts can conclude that the CrypMIC threat is far from gone.