Windows Virtual Firewall
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Ranking: | 9,803 |
| Threat Level: | 20 % (Normal) |
| Infected Computers: | 7,907 |
| First Seen: | July 16, 2012 |
| Last Seen: | August 26, 2023 |
| OS(es) Affected: | Windows |
Windows Virtual Firewall Image
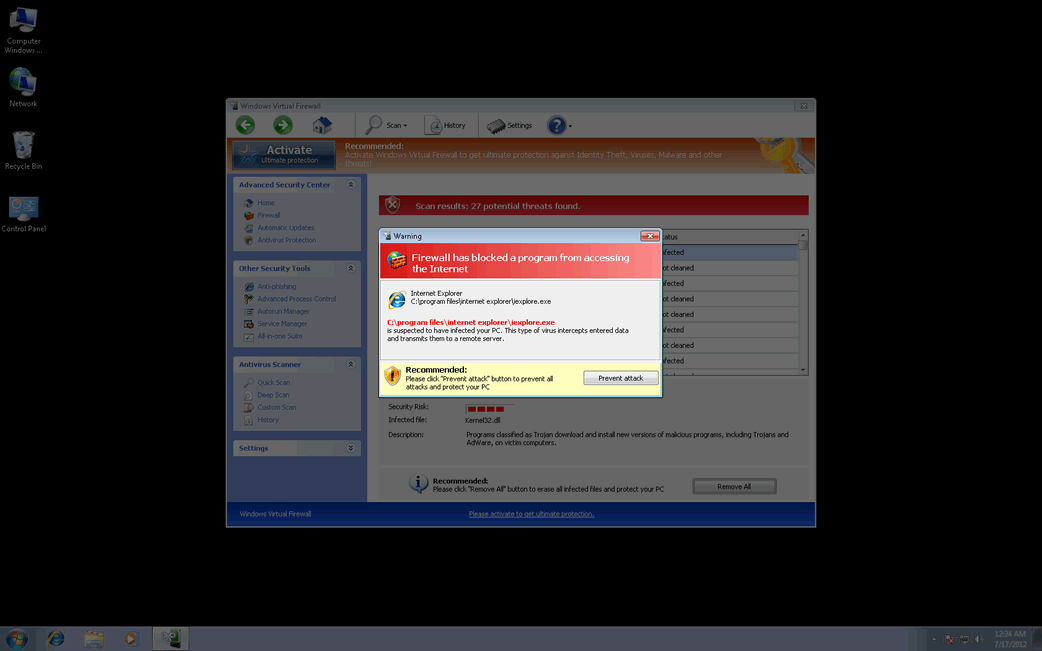
ESG security researchers warn against the supposed computer security application Windows Virtual Firewall. Despite its name, Windows Virtual Firewall has no association with Microsoft or with your computer system's firewall. Rather, Windows Virtual Firewall is part of a very common online scam designed to convince inexperienced computer users to purchase bogus security upgrades for fake security programs. This scam has been active for many years and, in the case of Windows Virtual Firewall's family of malware it has been active since 2009. This family, known to PC security researchers as FakeVimes, has numerous fake security programs and, since 2012, has also included a dangerous rootkit component in the form of a Sirefef variant. Removing Windows Virtual Firewall and other malware in the FakeVimes family requires the use of an established anti-malware program that was designed to fight the rootkit technology. Examples of clones of Windows Virtual Firewall include Windows Web Combat, Windows Stability Guard and Windows Virtual Angel.
Table of Contents
Understanding How Windows Virtual Firewall Enters Its Victims’ Computers
Most of the time, a social engineering strategy is used to deliver Windows Virtual Firewall and other FakeVimes rogue security programs. Some common approaches used to install Windows Virtual Firewall and its clones are listed below:
- Criminals may set up corrupted advertisements for security software. Often found on websites commonly considered unsafe (such as those associated with illegal file sharing and pornographic material,) these advertisements will use a two-pronged approach to attack the victim's computer system. In the background they may use Flash or JavaScript exploits in order to install a downloader Trojan or Windows Virtual Firewall itself. They will also engage in social engineering by claiming that the victim's computer system is severely infected and recommending the use of Windows Virtual Firewall to fix this supposed infection.
- Windows Virtual Firewall and other fake security programs can also be distributed in malicious email attachments. These will usually be disguised as benign image or text files while actually being compressed archives containing an executable file or malicious files designed to use known exploits to force the victim's computer to accept a malware infection.
- One third way in which Windows Virtual Firewall is commonly delivered is through fake video codecs. These are often found on pornographic or illegal-file sharing websites with supposed streaming video. Trying to watch these videos will often result in error messages prompting the victim to download a supposed video codec. However, this 'codec' is actually either Windows Virtual Firewall or a downloader Trojan designed to install this malicious program on the victim's computer system.
Windows Virtual Firewall Video
Tip: Turn your sound ON and watch the video in Full Screen mode.
File System Details
| # | File Name |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|
| 1. | %AppData%\Protector-[RANDOM CHARACTERS].exe |
Registry Details
URLs
Windows Virtual Firewall may call the following URLs:
| virtuallylend.com |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.