Security Shield 2012
Security Shield 2012 Image
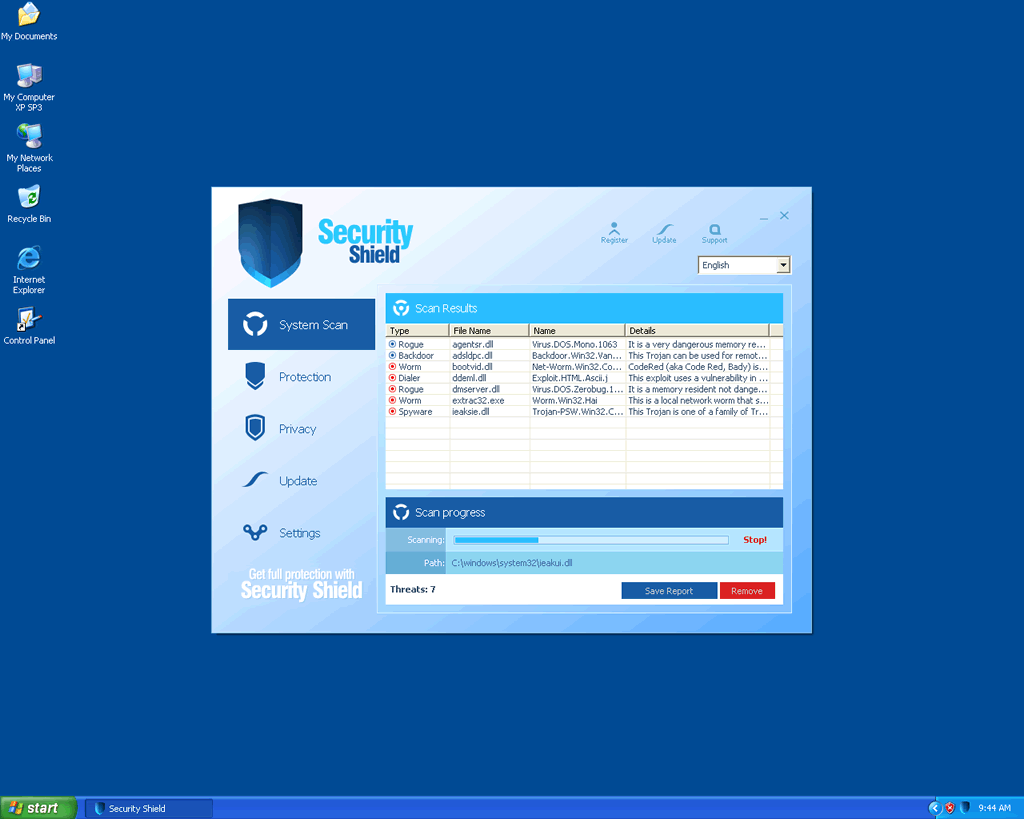
Security Shield 2012, also appearing as Security Shield or Security Shield Pro, is just one of dozens of fake security applications belonging to the WinWebSec family of rogue security applications. One of the characteristics that differentiate the WinWeb Security family of rogue security software from other fake security programs is that fact that Security Shield 2012 and its clones have the ability to block certain security programs as well as preventing the victim from accessing their web browser, displaying a fake firewall notification instead. ESG PC security researchers recommend starting up in Safe Mode and using a dedicated anti-malware application to delete Security Shield 2012 from the infected computer system.
There are many clones of Security Shield 2012, including System Security, Antivirus Security, Total Security 2009, Security Tool, Trojan.RogueAV.a.gen, System Adware Scanner 2010, FakeAlert-KW.e, Advanced Security Tool 2010, System Tool 2011, Security Shield, MS Removal Tool, Total Security, System Security 2011, Essential Cleaner, Security Shield Pro 2011, Personal Shield Pro, Security Shield 2011, Security Sphere 2012, Advanced PC Shield 2012, Futurro Antivirus.
There are several versions of each of these fake security programs, some ending with the year of their release (for example, Security Shield 2010 or Security Shield 2011) or by adding 'Pro' to the end of the bogus security program's name (for example, Security Shield Pro). Regardless of their name or year, these are all the same application with slight changes to the graphic user interface.
Table of Contents
Security Shield 2012 Will Not Provide Protection for Your Computer System
Security Shield 2012 has no way of removing malware from your computer, especially since Security Shield 2012 is a kind of malware infection. This program is designed entirely to convince its victims to purchase a 'full version' of a useless fake security application. Since Security Shield 2012 has the ability to disable your security software, it may be necessary to boot your computer from an external drive or in Safe Mode in order to gain access to your security software.
In some cases, renaming your security program with a name corresponding to an unblocked file process (such as explorer.exe) can bypass Security Shield 2012 and allow your security software to activate. In many cases, ESG security researchers have found that the fake registration code 64C665BE-4DE7-423B-A6B6-BC0172B25DF2 can stop many of Security Shield 2012's most intrusive symptoms, giving you access to your web browser and security software in order to remove Security Shield 2012. It is important to understand that this will not stop a Security Shield 2012 infection, but merely stop Security Shield 2012 from affecting your computer long enough for you to use a legitimate security tool to remove Security Shield 2012 from your operating system.
File System Details
| # | File Name |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|
| 1. | %AppData%\SecurityShield 2012 | |
| 2. | %StartMenu\%Programs\SecurityShield 2012\SecurityShield 2012.lnk | |
| 3. | %StartMenu\%Programs\SecurityShield 2012 | |
| 4. | %AppData%\Microsoft\Internet Explorer\Quick Launch\SecurityShield 2012.lnk | |
| 5. | %StartMenu\%Programs\SecurityShield 2012\How to Activate SecurityShield 2012.lnk | |
| 6. | %StartMenu%\ProgramsSecurityShield 2012\Help SecurityShield 2012.lnk | |
| 7. | %UserProfile%\Start Menu\Programs\SecurityShield 2012.lnk | |
| 8. | %AppData%\SecurityShield 2012\IcoActivate.ico | |
| 9. | %StartMenu\%Programs\SecurityShield 2012\Activate SecurityShield 2012.lnk |

