Sage Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Ranking: | 16,955 |
| Threat Level: | 100 % (High) |
| Infected Computers: | 1,121 |
| First Seen: | December 5, 2016 |
| Last Seen: | September 9, 2023 |
| OS(es) Affected: | Windows |
The Sage Ransomware is a typical ransomware Trojan that is used to encrypt the victims' files and then demand ransom in exchange for the decryption key. PC security analysts suspect that the Sage Ransomware is related to the TeslaCrypt family of ransomware after studying the Sage Ransomware's code. If the Sage Ransomware has been installed on your computer, PC security researchers advise computer users to avoid paying the ransom, since this seldom results in the recovery of the affected files.
Table of Contents
Sage PC Users will be Protected Against the Sage Ransomware
The Sage Ransomware encrypts the victim's data by using a strong encryption algorithm. After encrypting the victim's files, the Sage Ransomware shows a ransom note to the victim in the form of a pop-up message. The text of the Sage Ransomware's ransom note reads as follows:
'ATTENTION!
the Sage encrypted all your files!
—————————–
All your files, images, videos, and databases were encrypted and made inacessible by software known as the Sage.
You have no chance to restore the files without our help.
But if you follow our instructions files can be restored easily.
Instructions on how to get your files back are stored on every disk,
in your documents and on your desktop.
Look for files !Recovery_2g0zr9.txt and !Recovery_2g0zr9.html
If you can't find this files, use the program 'Tor Browser'(you can find it in Google)
to access the (onion)Web site http://qbxeaekvg7o3lxnn.onion to get your instructions'
The Sage Ransomware asks for $560 USD in BitCoin, doubling the amount if the ransom has not been paid within a week. Paying the Sage Ransomware ransom may not result in access to the decryption key.
The Phases of a Sage Ransomware Infection
The Sage Ransomware attack is basic, but effective. the Sage Ransomware has some basic methods to avoid detection by security software, and uses the AES 256 and RSA 1024 encryption to make the victim's files inaccessible. During its attack, the Sage Ransomware scans the victim's computer in search for certain file types to encrypt. The Sage Ransomware will encrypt the following file types:
.3GP, .7Z, .APK, .AVI, .BMP, .CDR, .CER, .CHM, CONF, .CSS, .CSV, .DAT, .DB, .DBF, .DJVU, .DBX, .DOCM, ,DOC, .EPUB, .DOCX .FB2, .FLV, .GIF, .GZ, .ISO .IBOOKS,.JPEG, .JPG, .KEY, .MDB .MD2, .MDF, .MHT, .MOBI .MHTM, .MKV, .MOV, .MP3, .MP4, .MPG .MPEG, .PICT, .PDF, .PPS, .PKG, .PNG, .PPT .PPTX, .PPSX, .PSD, .RAR, .RTF, .SCR, .SWF, .SAV, .TIFF, .TIF, .TBL, .TORRENT, .TXT, .VSD,.WMV, .XLS, .XLSX, .XPS, .XML, .CKP, .ZIP, .JAVA, .PY, .ASM, .C, .CPP, .CS, .JS, .PHP, .DACPAC, .RBW, .RB, .MRG, .DCX, .DB3, .SQL, .SQLITE3, .SQLITE, .SQLITEDB, .PSD, .PSP, .PDB, .DXF, .DWG, .DRW, .CASB, .CCP, .CAL, .CMX, .CR2.
The Sage Ransomware also will encrypt a variety of rare file types associated with programs such as Adobe Photoshop or other specialized applications. The Sage Ransomware delivers its ransom note as a text file and an HTML file, both dropped on the victim's Desktop. The Sage Ransomware will also change the victim's Desktop image into its ransom note.
Recovering from a Sage Ransomware Attack
The best defense against threats like the Sage Ransomware is to have backups of all important files. This allows a quick recovery by restoring the affected files from the backup. Recovering from a Sage Ransomware can be a significant expense, especially for individual computer users rather than small businesses or medium-sized businesses, which are also targeted in these attacks. Paying the Sage Ransomware ransom allows these people to continue creating these attacks. Instead, PC security researchers strongly advise computer users to have strong backup methods. Having backups of files makes attacks like the Sage Ransomware completely ineffective. In fact, if having backups of all files becomes a standard practice eventually, it is likely that attacks that follow the Sage Ransomware's methods will become completely obsolete since the con artists no longer have any leverage to demand payment of a ransom.
SpyHunter Detects & Remove Sage Ransomware
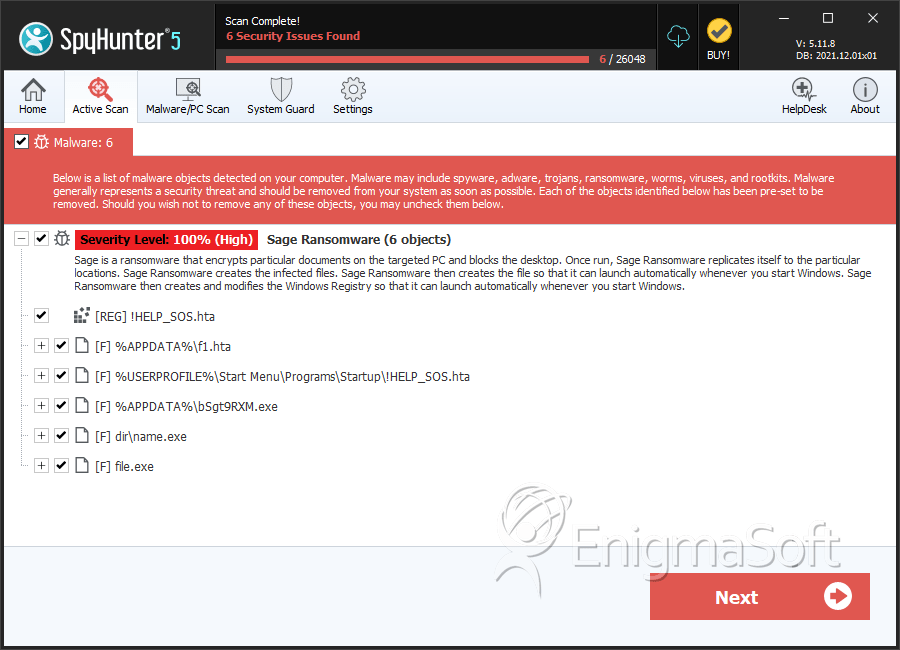
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | f1.hta | da3fc4dc0cab7127d2228eea660def92 | 91 |
| 2. | f1.hta | 69ffb32f0a73e94492e1de2759ec4e47 | 58 |
| 3. | f1.hta | 0e962b17327cf256a7a9aac36bcc2e73 | 42 |
| 4. | f1.hta | 3d2a8e8b0c01ee4c0bafc49feb66dcf8 | 39 |
| 5. | f1.hta | 3d06a605002f0804b7ee4b28b5b0add1 | 38 |
| 6. | f1.hta | cef78bb8b23c09271a714810bee83ead | 37 |
| 7. | f1.hta | 9ac24a74c5fb285bda11a36f2572f358 | 30 |
| 8. | f1.hta | f043948461a12b1013c69cb0f9202db9 | 25 |
| 9. | f1.hta | 996df93357dd6b84ff3f4bb776799008 | 22 |
| 10. | f1.hta | ba63852da88e3217747e246c13f0b350 | 22 |
| 11. | f1.hta | 5b665ea43bb8bd2752c2a676aec9095d | 22 |
| 12. | f1.hta | 2df49f17d4b5faadebd80e0ba8abd64c | 14 |
| 13. | f1.hta | 75e0befbf9f654183f8fd28b568df045 | 13 |
| 14. | f1.hta | 56c72facc278384e05dc2f7aa0eab860 | 13 |
| 15. | f1.hta | 793dbbc4261f681a5d204e8e196d11bc | 12 |
| 16. | f1.hta | 4856de358dd83e9562b0864c7d1ed40c | 12 |
| 17. | f1.hta | 5760263e095cd4fec28a0d8a5b3a8e2a | 12 |
| 18. | !HELP_SOS.hta | b98ea223d2147b74a151614b756a84fd | 11 |
| 19. | f1.hta | e00e17e5c7525ed68e1b660239a81e3f | 10 |
| 20. | f1.hta | e68e9dfeb02037693858df00008d0af0 | 10 |
| 21. | f1.hta | 5947e68e4358be02cd264a68bc8e22c3 | 10 |
| 22. | !HELP_SOS.hta | f6339a90d5a71c514a1d1aeeeb44829c | 10 |
| 23. | f1.hta | 22dda250b1f467bdc19d4075c9da1327 | 10 |
| 24. | !HELP_SOS.hta | 557ae920ab0898fba2a5b05ea3167ab5 | 4 |
| 25. | !HELP_SOS.hta | 7dfb4582aec404f6ec68614a476cb178 | 4 |
| 26. | !HELP_SOS.hta | a8c342224490fb8a30616ded6d030622 | 1 |
| 27. | !HELP_SOS.hta | b339f1cdfd77aeb604727798e33af202 | 1 |
| 28. | file.exe | c167732d2390deb95b081c97caf23cc2 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.