Are You Sure You’re NOT Infected with Malware?
Don’t Fall Victim to Malware or Ransomware Attacks!
Detect and remove malware, viruses, ransomware & other threats for FREE! Get Protected with SpyHunter.
Download SpyHunter (FREE Trial!)*Malicious software, or malware, is software specifically designed to operate on a system without the knowledge of the user or their consent. Malware comes in many shapes and forms, but it is mostly aimed at either collecting information or hurting the system they inhabit. Although the commonly used term “computer virus” is used in many cases, malware is a catch-all term for a varying range of software. Malware may cover a range of threats such as spyware, worms, Trojans, rootkits, adware, scareware, rootkits, used for dishonest practices, and more. Malware may encrypt sensitive data, steal information, hijack functions, and monitor the activities of users without their permission. These may affect not only computers, but servers, clients, routers, networks, and even individual devices. Today malware is used by both black hat hackers and governments to steal personal, business, financial information or to sabotage computer systems and industry. Malware is also sometimes used against government or corporate websites to disrupt their operations or to make a statement, as was the case with numerous hacks attributed to hackers from the hacktivist group Anonymous.
The rise of malware attacks and operations worldwide has also increased the damage by such actions, as can be seen in the figure below:
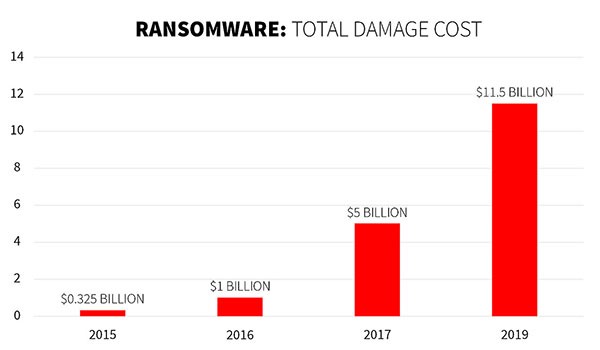
Ransomware Damages Costs Chart – Source: CyberSecurity Ventures
The term malware itself was used for the first time by Yisrael Radai, a security researcher and computer scientist back in 1990. Malware existed long before that, however. In 1971 BBN Technologies engineer Robert Thomas created the Creeper virus as an experiment, made to interact with DEC PDP-10 mainframe computers running the TENEX operating system and to spread on the ARPANET. Although the program itself didn’t alter any functions, delete, or steal any data, it was moved from one mainframe to another without the permission of the users, all the while displaying a teletype message reading “I’m the creeper: Catch me if you can.”
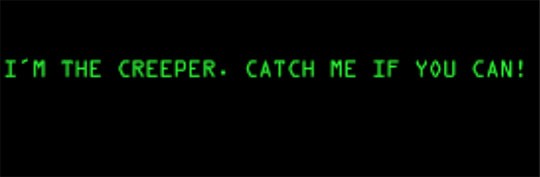
Creeper Malware
The Creeper virus was then altered by computer scientist Ray Tomlinson, adding the ability to self-replicate and essentially creating the first worm in known history. Tomlinson then created Reaper, a program that acted as the first antivirus software, designed to move across ARPANET and to delete the self-replicating Creeper worm. Later on, the concept of malware took off in the technology industry, with examples of such threats appearing on IBM and Apple personal computers in the 1980s, before becoming more popular and widespread after the introduction of the World Wide Web as part of the commercial face of the internet in the 1990s.
Malware authors use various ways of physical and virtual interaction used to spread malware and to infect networks and individual devices. Malicious programs may, for example, spread through the use of drive-by downloads infecting USB drives, which in turn end up affecting other machines. On the other side of malware propagation, examples can be seen through the use of phishing attacks, disguised as legitimate messages that contain malicious attachments or links. Some malware types attack with the concentrated effort of a command-and-control server that allows the threat actors to communicate and extract information from infected systems, even remotely compromising and wiping devices and servers. Malware threats have been steadily on the rise over the course of time, growing in sophistication and spread.
New and emerging strains of malware often include new techniques allowing them advanced evasion and obfuscation capabilities, working to fool not only the users but antimalware products as well. Some of the methods count on tactics, such as using web proxies to hide their IP addresses and malicious actions. The more advanced threats, such as polymorphic malware, may change their underlying code to have a better chance against signature-based detection. Others may use anti-sandbox techniques to avoid being detected while inside a sandbox environment, where samples of malware are easier to trap and analyze. Fileless malware, on the other hand, is capable of residing in the system’s RAM to avoid detection.
Common signs of malware infection may include the following symptoms:
Different types of malware have different characteristics that distinguish them from one another, for example:
Worms can self-replicate usually without human interaction or any instructions from the authors that made them. The primary function of a worm is to propagate to other computers while remaining active on affected systems. The Morris Worm was considered to be the first computer worm back on November 2, 1988. Modern examples of worms can be seen with Stuxnet, a threat capable of infecting supervisory control and data acquisition (SCADA) systems in the nuclear industry.
Spyware is made with the specific task of collecting data on infected devices and any users utilizing them without their knowledge. Spyware is an umbrella term used for applications and tools used to collect data, though not necessarily one kind of threat. This information is often sent to remote servers, where the information can be used or sold to third parties. Spyware may come in the form of worms, trojans, tracking cookies or system monitors, among other things. The word spyware was used for the first time around October 1995 in Usenet in a post aiming at Microsoft’s business model at the time.
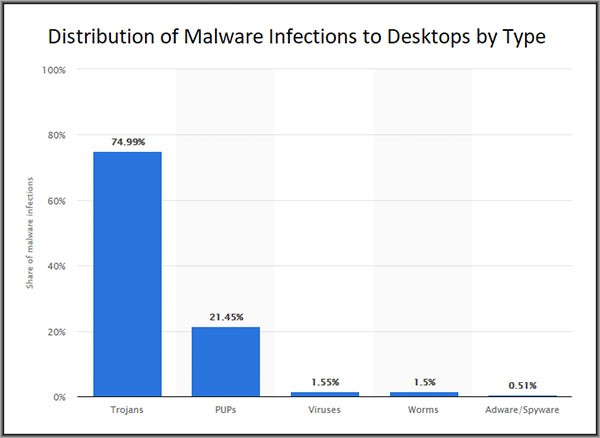
The global volume of spyware threats is dwarfed by other types of malware – Source: Safetydetectives.com
Trojans are designed to appear as a legitimate program closely emulating what functions it is supposed to imitate. Once activated during installation, though, Trojans may execute other functions of a more malicious nature. They may sometimes be disguised in the form of what looks to be legitimate software. Trojans are often employed by hackers and cybercriminals looking to gain access to a system. They are sometimes deployed with the use of social engineering tactics, fooling the users into executing the application themselves. The first case of a trojan operating in a network dates back to 1975 with ANIMAL, written by John Walker for UNIVAC 1108. More modern examples of trojans can be seen with the Zeus trojan, capable of stealing personal information, banking details, and more.
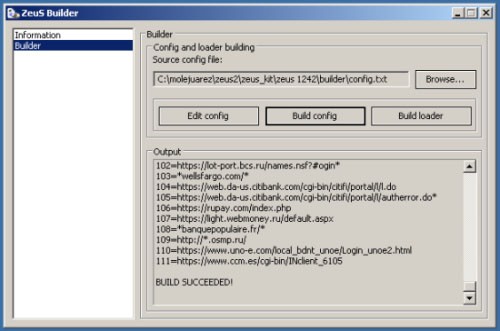
The ZeusBuilder toolkit was released soon after a Zeus source code leak in 2011 – Source: Live Hacking
Rootkits are used to obtain admin-level access to the victim’s system. Once this software is installed, it gives the threat actors root access with the capability of controlling almost any process. Rootkits are designed to keep their existence hidden from the user and from security software. The first rootkit that made the news in a big way was part of a copy protection attempt by Sony on CDs sold by the company. The rootkit was installed by the company, opening more vulnerabilities in the process when users listened to the CDs on their systems.
Ransomware is made to infect a user’s system and to encrypt useful and sensitive data. Criminals use this during ransom demands to extract ransom payments from the victim in exchange for a decryption key for the system data, but often they don’t provide one. Ransomware is often deployed with the threat of publishing the user’s personal data or continuously blocking access to it with a strong encryption algorithm unless a ransom is paid off. With the more advanced ransomware threats, data recovery becomes nearly impossible without a decryption key. A decryption tool may be released after a period of reverse engineering of the ransomware by security researchers. The first ransomware trojan appeared in 1989, called AIDS. More modern examples can be seen with Cryptolocker and WannaCry.
Backdoors or also Remote Access Trojans (RAT) are capable of quietly creating backdoors into infected systems that allow threat actors to access infected machines remotely. Backdoors are a concept that dates back to the dawn of ARPANET in 1967. They were discussed and theorized at the time, later to be implemented in systems either for testing purposes or by cybercriminals. Some modern threats are capable of installing backdoors, opening up security vulnerabilities to exploit. Examples such as Backdoor.Win32.BlackHole and other similar threats give administrative access to attackers and full control of infected machines.
Keyloggers are used to record nearly everything the users do on an infected computer by keeping track of keystrokes but also open web pages, programs, emails, and more. This is done covertly, so the person using the computer in question doesn’t pick up on being monitored. Data can then be retrieved by the person operating the logging program. Legal keyloggers exist, often sold to employers and used to oversee the use of computers in the workplace, but keyloggers are also often used to steal personal information, passwords, banking details, and more. One of the earliest keylogger software was written by Perry Kivolowitz in 1983 for Unix and posted on Usenet. Today there are many legal and illegal varieties, such as KeyBase Keylogger, Keylogger.Fs0ciety and more.
Adware is used to track the user’s download and browser history with the intent of providing banner ads and to attempt to lure the user into purchasing products through targeted ads. Although not necessarily a threat, some infected ads may be used to spread other threats in less reputable or compromised websites. Adware started becoming more prominent around 1995, with its use becoming more common as time went by. In some cases, adware is used with poisoned ads to carry out unwanted tasks, such as recording web page history, search activity, tracking the user’s location, and more.
Last updated: 2026-02-07