'.locky File Extension' Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 375 |
| First Seen: | February 16, 2016 |
| Last Seen: | October 24, 2025 |
| OS(es) Affected: | Windows |
Ransomware Infections have become increasingly common in the last few years. Only in the first two months of 2016, computer users have come across hundreds of new ransomware infections and variants of previous ransomware threats. One of the most prevalent threats in this period is TeslaCrypt 3.0, a new version of a ransomware Trojan first released in early 2015. The '.locky File Extension' Ransomware is one of the many variants of this threat. This new version of TeslaCrypt closes a loophole that allowed computer users to help computer users recover their files previously. Variants of this threat have been released, each changing the victims' files' extensions to a different string. In the case of the '.locky File Extension' Ransomware Trojan, this is a TeslaCrypt 3.0 variant that changes encrypted files' extensions to LOCKY.
How the '.locky File Extension' Ransomware may Infect a Computer
The '.locky File Extension' Ransomware infection process is not difficult to understand. In fact, most encryption ransomware tends to follow the same approach when infecting a computer. First, the '.locky File Extension' Ransomware will be delivered using common threat delivery methods, in most cases a corrupted email attachment contained in a phishing email message. When the victim opens the harmful email attachment, the '.locky File Extension' Ransomware is installed on the victim's computer. The '.locky File Extension' Ransomware will perform a scan of the victim's computer, looking for files to encrypt using its AES encryption algorithm. The .locky File Extension' Ransomware Trojan will infect files with the following extensions:
.7z; .rar; .m4a; .wma; .avi; .wmv; .csv; .d3dbsp; .sc2save; .sie; .sum; .ibank; .t13; .t12; .qdf; .gdb; .tax; .pkpass; .bc6; .bc7; .bkp; .qic; .bkf; .sidn; .sidd; .mddata; .itl; .itdb; .icxs; .hvpl; .hplg; .hkdb; .mdbackup; .syncdb; .gho; .cas; .svg; .map; .wmo; .itm; .sb; .fos; .mcgame; .vdf; .ztmp; .sis; .sid; .ncf; .menu; .layout; .dmp; .blob; .esm; .001; .vtf; .dazip; .fpk; .mlx; .kf; .iwd; .vpk; .tor; .psk; .rim; .w3x; .fsh; .ntl; .arch00; .lvl; .snx; .cfr; .ff; .vpp_pc; .lrf; .m2; .mcmeta; .vfs0; .mpqge; .kdb; .db0; .DayZProfile; .rofl; .hkx; .bar; .upk; .das; .iwi; .litemod; .asset; .forge; .ltx; .bsa; .apk; .re4; .sav; .lbf; .slm; .bik; .epk; .rgss3a; .pak; .big; .unity3d; .wotreplay; .xxx; .desc; .py; .m3u; .flv; .js; .css; .rb; .png; .jpeg; .txt; .p7c; .p7b; .p12; .pfx; .pem; .crt; .cer; .der; .x3f; .srw; .pef; .ptx; .r3d; .rw2; .rwl; .raw; .raf; .orf; .nrw; .mrwref; .mef; .erf; .kdc; .dcr; .cr2; .crw; .bay; .sr2; .srf; .arw; .3fr; .dng; .jpeg; .jpg; .cdr; .indd; .ai; .eps; .pdf; .pdd; .psd; .dbfv; .mdf; .wb2; .rtf; .wpd; .dxg; .xf; .dwg; .pst; .accdb; .mdb; .pptm; .pptx; .ppt; .xlk; .xlsb; .xlsm; .xlsx; .xls; .wps; .docm; .docx; .doc; .odb; .odc; .odm; .odp; .ods; .odt
After the '.locky File Extension' Ransomware has infected the victim's files, the '.locky File Extension' Ransomware will change the affected files' extensions to LOCKY to indicate which files have been encrypted. The '.locky File Extension' Ransomware will also delete Shadow Volume copies of encrypted files as well as System Restore points, making it impossible for computer users to use alternate methods to recover their files. Sadly, it is currently not possible to decrypt the files encrypted by the '.locky File Extension' Ransomware without the encryption key, which is stored on the Command and Control server rather than in the '.locky File Extension' Ransomware infection itself.
The '.locky File Extension' Ransomware alerts the victim of the infection using text or image files dropped on the victim's computer. These messages will demand payment of a ransom worthing several hundred dollars through BitCoin or other anonymous methods. The following is an example of a ransom message commonly associated with the '.locky File Extension' Ransomware:
Your personal files are encrypted!
Your files have been safely encrypted on this PC: photos, videos, documents, etc. Click "Show Encrypted Files" button to view a complete list on encrypted files, and you can personally verify this.
Encryption was produced using a unique public key RSA-2048 generated for this computer. To decrypt files you need to obtain the private key.
SpyHunter Detects & Remove '.locky File Extension' Ransomware
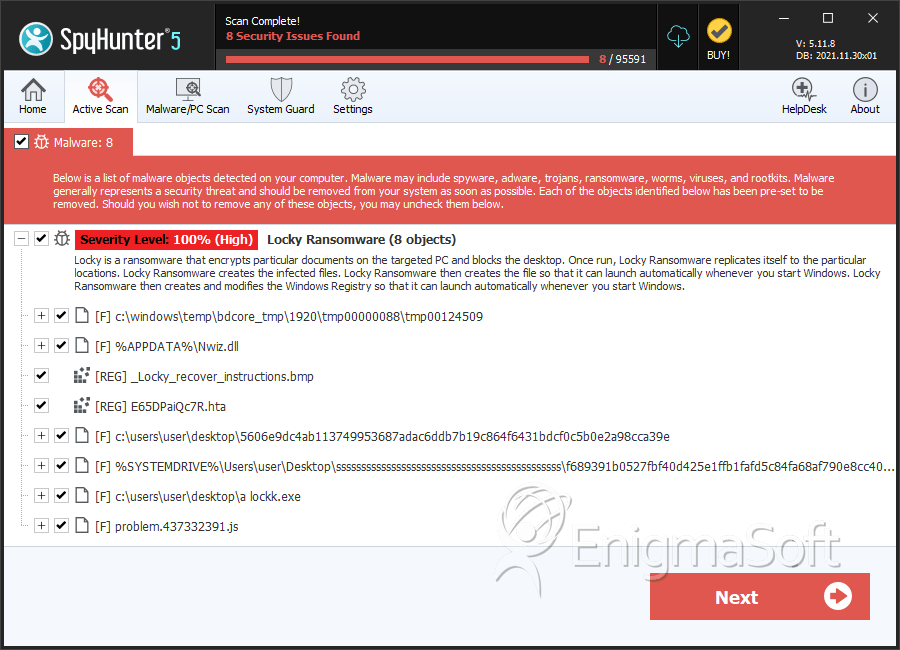
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | Nwiz.dll | 877dcbdf9b0a4a0872aadb13496d60b8 | 102 |
| 2. | tmp00124509 | 2fbffc7434688a221968eabce01cf406 | 29 |
| 3. | file.exe | 0ca0d0acc30a746227bc4b5054569d7f | 3 |
| 4. | 5606e9dc4ab113749953687adac6ddb7b19c864f6431bdcf0c5b0e2a98cca39e | 9dcdfbb3e8e4020e4cf2fc77e86daa76 | 2 |
| 5. | Locky.exe | 0d0823d9a5d000b80e27090754f59ee5 | 1 |
| 6. | f689391b0527fbf40d425e1ffb1fafd5c84fa68af790e8cc4093bcc81708c11b | 544bc1c6ecd95d89d96b5e75c3121fea | 1 |
| 7. | a lockk.exe | bfff16a0cca57b278591052a9059c0a1 | 1 |
| 8. | problem.437332391.js | 34b1de7abb0fca894b13780fc65899eb | 0 |
| 9. | MRI6219316107.js | e66009d3c69f364568d5f0d5dd6ec2d0 | 0 |
| 10. | name | bdff9c8ae6506768df834d19dfa028f9 | 0 |
