F0xy
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 10 % (Normal) |
| Infected Computers: | 1 |
| First Seen: | February 12, 2015 |
| Last Seen: | August 21, 2020 |
| OS(es) Affected: | Windows |
F0xy is a threat infection that has caught the attention of PC security researchers because of the cleverness of the attack, and the stealthiness F0xy uses to hide from detection. F0xy can change its Command and Control dynamically in order to download and execute files on the victim's computer. Many threat infections have a Command and Control server to which they connect in order to download and upload data, receive orders and other important functions. A vital step in fighting against threats is intercepting these communications and shutting down these types of command and control servers and domains. F0xy's tactic of changing its Command and Control is especially important because F0xy may be used by other threats developers to carry out their attacks while evading detection.
Table of Contents
F0xy Installs a Crypto-Currency Miner on Attacked Pcs
Two of the main tactics associated with F0xy include using the Microsoft's Background Intelligent Transfer service in order to transfer its own threatening data and take advantage of Vkontakte, a popular social network in Russia, to carry out its attacks. The main payload associated with F0xy at this time is to download and install CPUMiner, a crypto-currency miner that uses the victim's computer to mine Bitcoin and other crypto-currency. This allows third parties to profit from installing F0xy on the victims' computers, allowing them to reap the benefits of mining crypto-currencies on a wide variety of infected computers rather than investing in expensive mining infrastructure.
How Third Parties may Generate Revenue Using F0xy
F0xy downloads the 64-bit version of CPUMiner, which is then installed and executed without the victim's knowledge. Numerous computers can be assigned as 'workers' in order to 'mine' crypto-currencies on behalf of a single currency wallet. The revenue goes up according to the number of infected computers. These types of attacks have become increasingly sophisticated, with cybercrooks using advanced tactics to make money directly at the expense of computer users.
F0xy may Hide Its Traffic in a Legitimate Network Traffic
The main purpose of F0xy is to act as a downloader. Potentially, any threat could be downloaded and installed using F0xy. At this time, F0xy is being used to download and execute CPUMiner. However, F0xy could just as easily be used to download and install a banking Trojan or adware. F0xy hides in legitimate network traffic and may use compromised legitimate websites or an advertising network fraud to gain access to the victims' computers. Malware analysts suspect that F0xy is still at an early stage, which could in the future become a more serious threat. F0xy is still being tested, not being used in widespread attacks but, rather, being used to test potential defenses and vulnerabilities. F0xy could very easily be modified to deliver a more serious and destructive payload as part of a wider threat campaign.
Protecting Your Computer from F0xy and Other Threats
If you are concerned about threats like F0xy finding its way into your computer, PC security researchers recommend the use of a skilled security program to protect your PC. Not only security programs should be kept fully updated and patched, but all software. Real-time protection and a firewall are also important. However, the best thing computer users can do to protect their computers from potentially harmful components or threats is to use common sense when browsing the Web. Threats are still mainly distributed using spam email messages, corrupted advertisements and social engineering techniques. Knowing not to open suspicious links, unknown email attachments or staying away from certain websites is one of the best ways of avoiding threat problems such as F0xy.
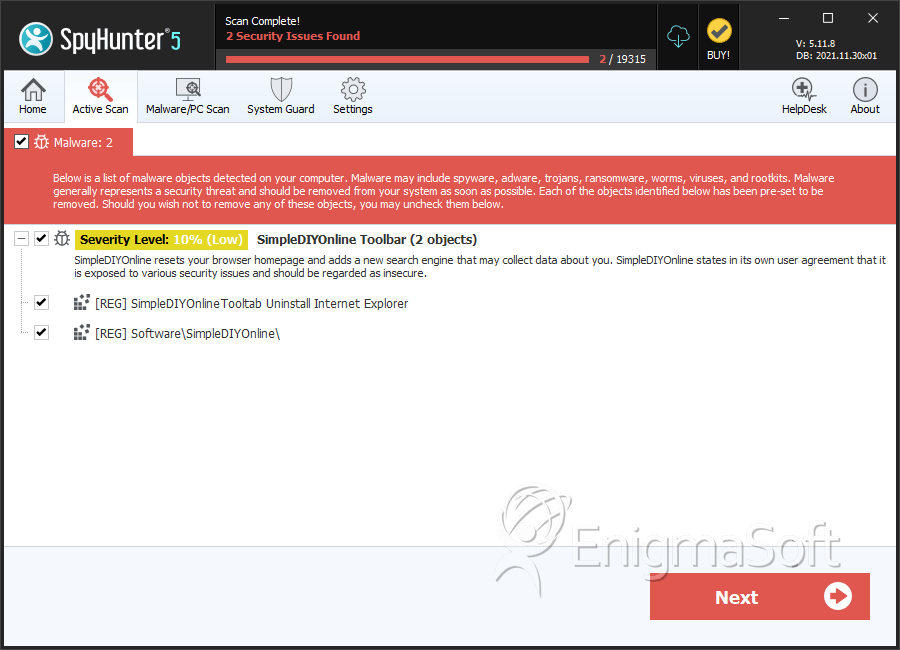
SpyHunter Detects & Remove F0xy


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.