Dyre/Dyreza Trojan
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 90 % (High) |
| Infected Computers: | 15 |
| First Seen: | June 17, 2014 |
| Last Seen: | July 3, 2019 |
| OS(es) Affected: | Windows |
The Dyreza Trojan is a banker Trojan that is used to take money and login credentials from the victims' bank accounts. One of the reasons why the Dyreza Trojan became interesting to PC security analysts is because the Dyreza Trojan can bypass the SSL mechanism, undermining this basic online security protection measure. The Dyreza Trojan may collect the financial credentials and then send them to the attacker in a remote location in plain text. The Dyreza Trojan also has RAT (Remote Access Trojan) capabilities, letting outsiders control the affected computer from a remote location. The Dyreza Trojan allows ill-minded persons to intercept encrypted traffic by routing the connection through domains belonging to the attackers.
Table of Contents
The Dyreza Trojan may Cause Serious Damage to a Computer User’s Finances
The Dyreza Trojan, also known as Dyre, uses a method known as browser hooking to interrupt online traffic and route it directly to servers that are controlled by the attackers. Using browser hooking, people may collect information without the victim being aware that the data is being tracked on or intercepted. On the side of the victim, the session seems to continue uninterrupted through HTTPS, despite being routed to a third party automatically. As soon as the Dyreza Trojan infects a computer, the Dyreza Trojan establishes a connection with various IP addresses and requests access to a 'publickey' directory, whose purpose is currently unknown. The Dyreza Trojan uses the established connection to receive commands from the remote server and to relay information about the infected computer's settings and operating system.
Using the Dyreza Trojan, third parties may capture traffic from the affected Web browser. Every time the victim carries out a task on the affected Web browser, the Dyreza Trojan sends the information to the attacker as well, allowing other persons to gain access to data or command the infected PC from an outside location. Through the use of the Dyreza Trojan, other people may see when the victim enters a secure address or password in plain text, with the main target of these attacks being online banking and financial websites. The true danger of the Dyreza Trojan is that the victim is never aware that their information is being intercepted.
Aliases
11 security vendors flagged this file as malicious.
| Anti-Virus Software | Detection |
|---|---|
| AVG | Crypt3.BWFI |
| Fortinet | W32/Upatre.HN!tr |
| Ikarus | Trojan.Inject |
| Panda | Trj/Genetic.gen |
| AhnLab-V3 | Trojan/Win32.Waski |
| Microsoft | PWS:Win32/Dyzap |
| Sophos | Troj/Dyreza-BD |
| McAfee-GW-Edition | BehavesLike.Win32.Backdoor.gc |
| Kaspersky | Trojan.Win32.Staser.gv |
| Symantec | Infostealer.Dyranges |
| McAfee | Upatre-FAAJ!97388A31E2E3 |
SpyHunter Detects & Remove Dyre/Dyreza Trojan
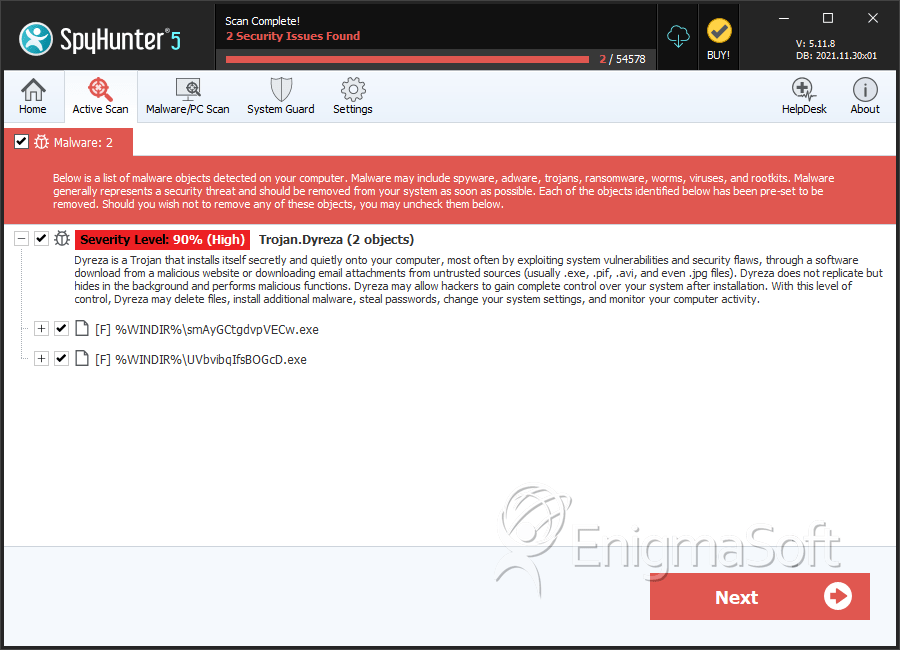
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | smAyGCtgdvpVECw.exe | 97388a31e2e36b2bef2984e40e23f2f1 | 5 |
| 2. | UVbvibqIfsBOGcD.exe | b25cafa85213d906bee856a841dbae02 | 1 |

