Updated Vcrypt Ransomware Locks Files in Password-Protected 7zips
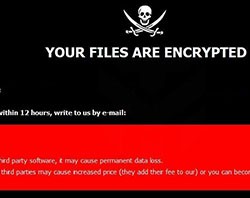 A ransomware threat by the name of Vcrypt is targeting French users in an aggressive method. Vcrypt utilizes 7zip, a legitimate program to create password-protected archives of the affected data folders.
A ransomware threat by the name of Vcrypt is targeting French users in an aggressive method. Vcrypt utilizes 7zip, a legitimate program to create password-protected archives of the affected data folders.
The ransomware was deleting all of the victim's files found in the Windows data folders, and then it recreates new allegedly encrypted files that use the original folder's name. The encrypted files bear names similar to username_foldername.vxcrypt.
Examples of this were seen with files in the Documents folder being deleted, with a new file called User_documents.vcrypt being created. The ransomware launches Internet Explorer and shows a ransom note called help.html. The language used in the note is French, explaining how users may visit a website to get their files back.
The Vcrypt Ransomware note text translates to the following:
Q: What happened to my files?
A: All your files have been encrypted and placed in a security zone.
Q: How to recover my documents !!?
A: Follow the instructions available via this web page. If the page does not open, please check your internet connection.
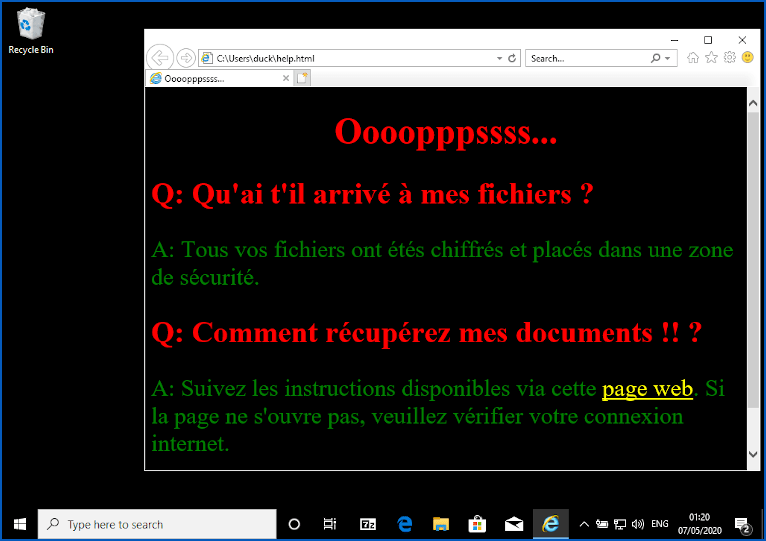
The VCrypt ransom note; Source: Sophos
The website was taken offline, so the amount of the ransom demand is currently unknown.
Vcrypt Creates 7zip Archives Protected by Passwords
Researchers discovered that VCrypt does not encrypt any files at all. When it is executed, the malware configures an automatic start and then extracts 7za.exe to %Temp% under the name mod_01.exe.
Once that step is complete, the ransomware executes commands that archive the affected files in these folders, creating password-protected archives:
%PUBLIC%\Desktop
%PUBLIC%\Downloads
%PUBLIC%\Pictures
%USERPROFILE%\Desktop
%USERPROFILE%\Downloads
%USERPROFILE%\Pictures
%USERPROFILE%\Music
%USERPROFILE%\Videos
%USERPROFILE%\Documents
%PUBLIC%\Music
%PUBLIC%\Videos
%PUBLIC%\Documents
Each archive created by VCrypt uses the same password, hardcoded into it by its creators. It archives the files and deletes any data in the folder after completion. In some cases, with other drives, the ransomware does not archive files before deletion, but it acts as a wiper.
The malware scrambles files on C: and wipes out the files on any other drives, going all the way from A to Z and skipping C: drive, destroying any files and directories it finds.
The attackers used a regular free hosting page to house their ransom demand address, with no Tor or dark web connections, so users are left with no way of paying any ransom demand. The good news is that the creators of VCrypt used a hardcoded crypto key that may be extracted from the malware file.
It is unknown at this time how the ransomware is primarily distributed.