A previously unidentified cyber threat actor directs their attention towards the U.S. aerospace industry by deploying a newly discovered PowerShell-based malware called PowerDrop. This advanced malware utilizes various deceptive tactics, encoding techniques, and encryption to avoid detection. The name "PowerDrop" derives from its reliance on the Windows PowerShell tool and the "DROP" (DRP) string incorporated into its code for padding.
PowerDrop is a post-exploitation tool designed to gather sensitive information from compromised networks after gaining unauthorized access through alternative methods. To settle communication with a Command-and-Control (C2) server, the malware employs Internet Control Message Protocol (ICMP) echo request messages as beacons. The C2 server then responds with encrypted commands decoded and executed on the compromised host. Similarly, an ICMP ping message aims to exfiltrate the results of these instructions.
Notably, PowerDrop leverages the Windows Management Instrumentation (WMI) service to execute the PowerShell commands, showcasing the threat actor's use of "living-off-the-land" techniques to evade detection. While the core nature of the malware may not be exceptionally sophisticated, its ability to obfuscate suspicious activities and evade endpoint defenses indicates the involvement of more advanced threat actors.
Table of Contents
Unveiling the Tactics of the Stealthy Malware Attack
The recently discovered malware has been brought to light by security researchers via an advanced machine learning detection system – powerful technology that scrutinizes the content of PowerShell script executions, enabling the identification of this elusive threat. However, despite this breakthrough, the exact infection chain and initial compromise of PowerDrop remain shrouded in mystery.
Analysts speculate on the potential methods employed by the attackers to deploy the PowerDrop script. These include exploiting vulnerabilities, utilizing phishing emails to target victims, or even resorting to the deceptive tactic of spoofed software download sites. The exact avenue through which PowerDrop infiltrated systems is yet to be determined. To enhance its covert nature, the script is encoded using Base64, allowing it to function as a backdoor or Remote Access Trojan (RAT). This sophisticated technique enables PowerDrop to evade detection and maintain persistence within compromised systems.
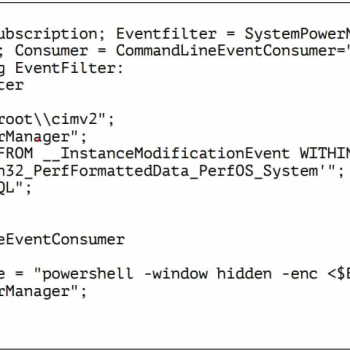
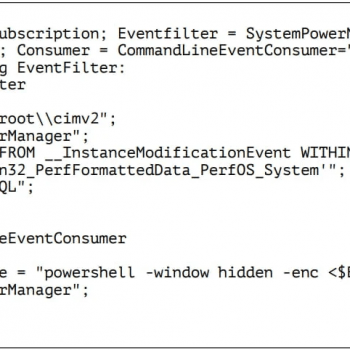
Delving into the system logs unravels crucial insights into PowerDrop's modus operandi. The analysis revealed that the malicious script effectively utilized previously registered WMI event filters and consumers with the distinct moniker 'SystemPowerManager.' The malware itself created this cleverly camouflaged mechanism upon compromising the system using the 'wmic.exe' command-line tool.
The revelation of PowerDrop's unique characteristics sheds light on the sophistication of modern-day cyber threats. With its ability to evade detection and operate covertly within compromised systems, PowerDrop exemplifies malicious actors' constant evolution and ingenuity in the digital landscape.
A previously unidentified cyber threat actor directs their attention towards the U.S. aerospace industry by deploying a newly discovered PowerShell-based malware called PowerDrop. This advanced malware utilizes various deceptive tactics, encoding techniques, and encryption to avoid detection. The name "PowerDrop" derives from its reliance on the Windows PowerShell tool and the "DROP" (DRP) string incorporated into its code for padding.
PowerDrop is a post-exploitation tool designed to gather sensitive information from compromised networks after gaining unauthorized access through alternative methods. To settle communication with a Command-and-Control (C2) server, the malware employs Internet Control Message Protocol (ICMP) echo request messages as beacons. The C2 server then responds with encrypted commands decoded and executed on the compromised host. Similarly, an ICMP ping message aims to exfiltrate the results of these instructions.
Notably, PowerDrop leverages the Windows Management Instrumentation (WMI) service to execute the PowerShell commands, showcasing the threat actor's use of "living-off-the-land" techniques to evade detection. While the core nature of the malware may not be exceptionally sophisticated, its ability to obfuscate suspicious activities and evade endpoint defenses indicates the involvement of more advanced threat actors.
Unveiling the Tactics of the Stealthy Malware Attack
The recently discovered malware has been brought to light by security researchers via an advanced machine learning detection system – powerful technology that scrutinizes the content of PowerShell script executions, enabling the identification of this elusive threat. However, despite this breakthrough, the exact infection chain and initial compromise of PowerDrop remain shrouded in mystery.
Analysts speculate on the potential methods employed by the attackers to deploy the PowerDrop script. These include exploiting vulnerabilities, utilizing phishing emails to target victims, or even resorting to the deceptive tactic of spoofed software download sites. The exact avenue through which PowerDrop infiltrated systems is yet to be determined. To enhance its covert nature, the script is encoded using Base64, allowing it to function as a backdoor or Remote Access Trojan (RAT). This sophisticated technique enables PowerDrop to evade detection and maintain persistence within compromised systems.
Delving into the system logs unravels crucial insights into PowerDrop's modus operandi. The analysis revealed that the malicious script effectively utilized previously registered WMI event filters and consumers with the distinct moniker 'SystemPowerManager.' The malware itself created this cleverly camouflaged mechanism upon compromising the system using the 'wmic.exe' command-line tool.
The revelation of PowerDrop's unique characteristics sheds light on the sophistication of modern-day cyber threats. With its ability to evade detection and operate covertly within compromised systems, PowerDrop exemplifies malicious actors' constant evolution and ingenuity in the digital landscape.