Spora Ransomware Gains Sophistication to Evade AV Detection
 When it first arrived back in January, the Spora ransomware amazed security researchers both with its incredibly complicated and strong encryption routine and with the professionally designed payment and support page. At one point, Spora was among the top ransomware families, and the chat transcripts between the victims and the crooks showed just how many people were left locked out of their computers. In March, however, its popularity suddenly started to dwindle. Although it didn't disappear completely, infections slowed to a crawl, and some of the domains that linked to the crooks' support page stopped working.
When it first arrived back in January, the Spora ransomware amazed security researchers both with its incredibly complicated and strong encryption routine and with the professionally designed payment and support page. At one point, Spora was among the top ransomware families, and the chat transcripts between the victims and the crooks showed just how many people were left locked out of their computers. In March, however, its popularity suddenly started to dwindle. Although it didn't disappear completely, infections slowed to a crawl, and some of the domains that linked to the crooks' support page stopped working.
Nevertheless, the experts thought it unlikely that the Spora gang would abandon their project after the considerable time spent creating what has to be one of the most sophisticated ransomware families of the year. Indeed, they were right.
Researchers from Sophos say that Spora is now well and truly back, and a tweet from Microsoft's Malware Protection Center suggests that this new version has been making the rounds since last week. For the time being, it's aimed at Russian users only, but there's a good chance that we'll see it in other countries as well because the crooks have updated Spora and are clearly hoping to make it even more effective.
Some of you may remember that during its less active period, Spora was distributed with the help of the EI Test campaign which redirected unsuspecting users to either a fake font pack for Google Chrome or a landing page used by the RIG exploit kit. The ransomware has now dropped this infection method and is back to the original vector – an HTA file (HTML application) put inside a ZIP archive and attached to an email. Sophos say that the new HTA files pretend to be payment documents and that their names contain a "_pdf" string, which, especially if the known file extensions are hidden (the default Windows behavior), could fool the victims into clicking on them. Here's the worrying bit – the security solutions might be fooled as well.
It all comes from the differences between how the said security solutions and Windows process files once a user clicks on them. Windows just sees the .hta extension (even though it might not be visible to you) and treats the file as a normal HTML application (i.e. it opens the HTML code without putting it in a sandbox). By contrast, most of the AV products and scanners know that file extensions can be spoofed which is why they go through the first bytes of the files to determine what they're dealing with, which is what the Spora crooks abused.
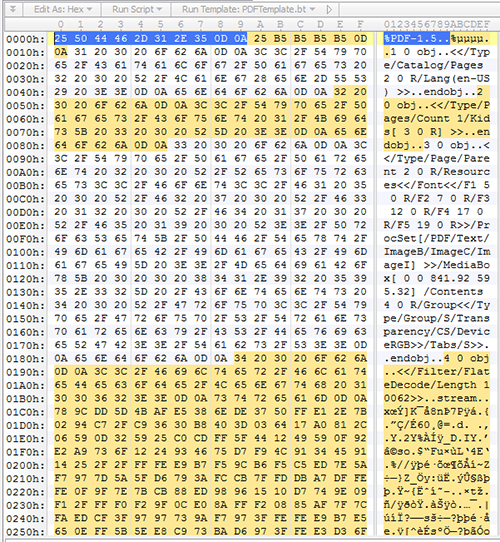
After putting the malicious HTAs into a HEX editor as shown in Figure 1 below, the researchers realized that the ransomware's authors had modified the file headers to look like perfectly normal PDF documents. This means that traditional file scanners raise no alarms, and Windows carries on with launching the application which, in turn, unleashes Spora.
Figure 1. Screenshot of Spora Ransomware malicious HTA in a HEX editor - Source: Sophos News
From then on, it's pretty much same old, same old. Sophos' blog post says nothing about the encryption algorithm of Spora's newest version, but considering the fact that it was quite strong when the ransomware first appeared, it's safe to assume that it's most likely remained unaltered. The worm-like features are still here as well.
When it's done encrypting the files, Spora hides the Program Files folder and replaces it with an LNK file (a Windows shortcut), which, in addition to opening the actual folder, also executes the ransomware. If the shortcut is clicked on by a user from another endpoint on the network, his/her system will also get infected.
Although it comes with a sleek design, a myriad of features, and a professionally-written encryption algorithm, Spora has so far failed to reach the success of Locky, Cerber, and the much cruder WannaCry. This new version shows, however, that the crooks haven't given up just yet and are looking for ways of making their ransomware more difficult to detect and remove, which is something regular users should keep in mind.