Netwalker Ransomware Operators Recruit Affiliates with Huge Payouts
 A ransomware operation called Netwalker is working on the recruitment of affiliates with the promise of a big payoff in the millions of dollars. The campaign is paired with an auto-publishing data leak blog to push for more ransom payments.
A ransomware operation called Netwalker is working on the recruitment of affiliates with the promise of a big payoff in the millions of dollars. The campaign is paired with an auto-publishing data leak blog to push for more ransom payments.
The operation started as Mailto, being responsible for a lot of high profile attacks. The threat actors rebranded themselves under the name Netwalker in March 2020, then began work on recruiting affiliates to distribute their ransomware. The affiliates were primed to control the breaching of networks and deployment of ransomware, receiving most of the payments these bring.
Table of Contents
Promises of more money by the Netwalker Cybercriminals
Advanced Intelligence, a cyber intelligence company, found that the public operator of the Netwalker ransomware was interviewing potential affiliates for that program since March 2020. Netwalker outlined the improvements they made to their operation in a post, sharing data about their ransom payments and how they extort their chosen victims.
This Week in Malware Ep 5: NetWalker Ransomware
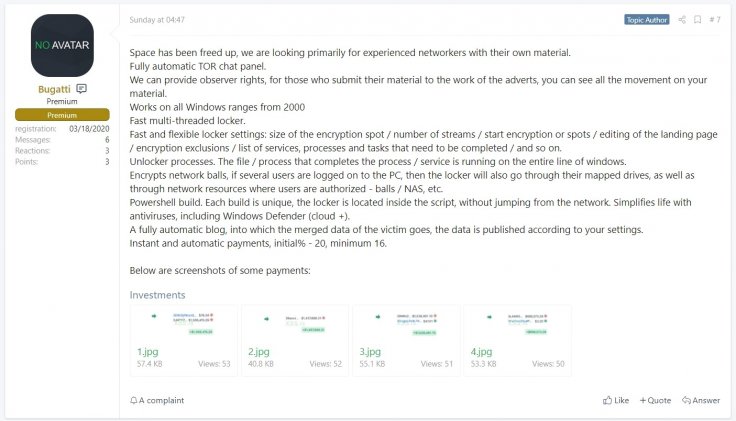
The Netwalker affiliate message Source: Twitter
The Ransom Payments Average a $696,000 to $1.5 Million
Affiliates are offered 70% of the paid ransom amount, allegedly allowing them to earn massive sums up to or over a million US dollars in a single ransom payment. Apart from the impressively large payouts, Netwalker is promoting the automatic publishing website with data leaks, allowing affiliates to upload links to the stolen data. They can also set dates when the information would be publicly released if the payments aren't made.
That type of approach became more common at the beginning of 2020 for ransomware operators, stealing data before encrypting it and holding that extra blackmail material over their victims. The cybercriminals threaten the victims with a public release of the sensitive files on data leak sites if the ransom isn't paid.
The Netwalker operators took things to a new level when they created a leak site that allows their recruited affiliates to create posts. That includes the victim's name, description, a password for data files, links to their data, and the time and date the data may be leaked. The website shows a countdown with a particular victim's data to push the victims into anxiety, forcing them to consider making the payment. When the countdown is done, the leak is automatically published with a link and password for the stolen data. The data is most often hosted on the file-sharing website MEGA.
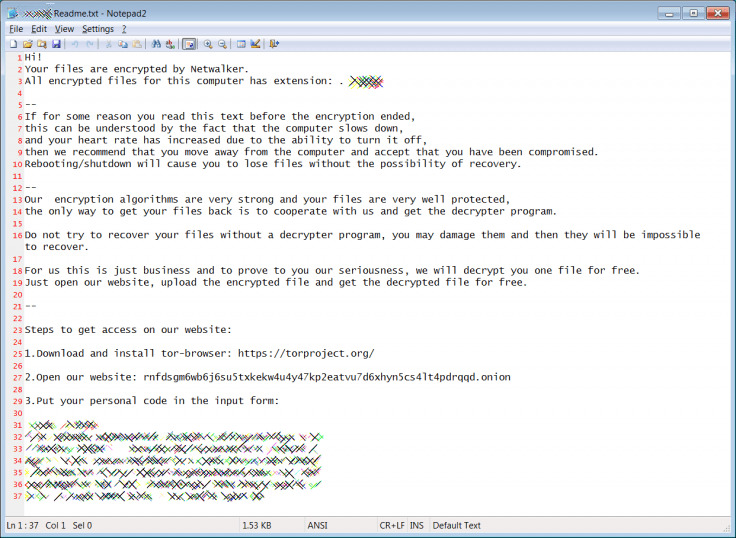
The Netwalker ransom note
How does the Netwalker Ransomware Operate?
The Netwalker ransomware usually spreads through phishing emails, currently bearing the COVID-19 theme, masquerading as health alerts from respected authorities. The emails are paired with malicious attachments written in a VB script, capable of infecting a machine by merely opening the attached document. Once the document is executed, it encrypts files on the device and adds a random extension to the encrypted data, as is the default modus operandi with ransomware.