Java Browser Plugin Fails to Check the Status of Stolen Digital Certificates as Unsafe
 Java has recently been the talk of the town when it comes to the latest platform or software to receive a rash of exploited attacks due to a vulnerability. With one vulnerability comes others, just as researchers have now found a weakness within a key security protection introduced in the browser plugin for Java's framework. This particular flaw is one that makes it easy for attackers to slip malware onto an affected computer further emphasizing how Java cannot catch a break in the unadulterated attacks it has encountered this year alone.
Java has recently been the talk of the town when it comes to the latest platform or software to receive a rash of exploited attacks due to a vulnerability. With one vulnerability comes others, just as researchers have now found a weakness within a key security protection introduced in the browser plugin for Java's framework. This particular flaw is one that makes it easy for attackers to slip malware onto an affected computer further emphasizing how Java cannot catch a break in the unadulterated attacks it has encountered this year alone.
It is said by researchers and even Oracle, the masterminds behind Java software framework, which over 3 billion computers use the platform. With such an abundance of systems using Java it only makes sense for hackers to target such a big bullseye, they can't miss it. The widely used Java plugin, with its many new-found vulnerabilities, was confirmed by Ars Technica not to check the status of digital certifications used to sign Java apps hosted on sites. Because of this, Java presents these certificates as trusted even in situations where they may have been reported as stolen or publicly blacklisted in databases. Such an oversight leads to serous repercussions in that the failure to check certificate revocation leaves a gaping hole in the infrastructure.
Vetting the status of certifications is necessary to prevent security issues. Moreover, such an oversight will virtually nullify Oracle's recent added security protections to the Java framework. In a way, you can think of this as what some may call a major 'goofup' by allowing Java to treat apps signed by a compromised certificate as trusted. In this situation, users will never get that pop-up notification alerting them of a possible untrusted certificate being accessed later leading to infiltration and diminished security.
It is no wonder Java has been the brunt of recent attacks, their stolen certificates are a virtual gateway for sneaky malware to slip onto an affected system.
Avast's director of threat intelligence, Jindrich Kubec, said "Java thinks the stolen certificate used is 100% valid and should be trusted," referring to the certificate revocation list. In thinking of an alternative method, he added: "With CRL/OCSP it would make it untrusted and probably present completely different dialogues or even won't allow running the applet at all—unfortunately, the situation is a bit complicated with testing this behavior, so I can't tell for sure which of the above would be true."
In support of Oracle's recent moves to better their Java issues, they made major strides in January when they addressed issues to have browser plugins prompt users before running Java apps. Of course, with any software maker, this is viewed as a patch instead of an actual fix as it does not make the user experience much easier.
Sometimes it is a trade-off of user-friendliness and security. Nowadays, it is very rare to have your cake and eat it too, especially when you are dealing with something as volatile and widely used as the Java infrastructure. Considering the strong presence of Java-based attacks recently, computer users are urged to at least educate themselves on steps they can take to 'control' their Java experience.
Figure 1. Java Control Panel customization settings window
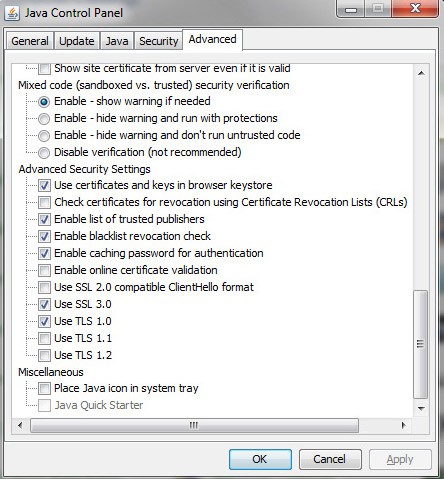
Java has its own set of accessible settings (Figure 1. above) even though it is a general-purpose programming language and software infrastructure that allows many web-based applications to run. There are many real-world threats lurking around the corner. Malicious Java apps are being discovered left and right but the interim actions taken are not enough to put these vulnerabilities to bed. Just the other day, a legitimate German dictionary website was purportedly compromised by those who initially planted the attack through Java. Perhaps a solution for now is to uninstall Java altogether or maybe utilize a stand-alone browser to access a small number of sites that require Java.