Flight Simulator Developer Fights Piracy by Installing a Password-Dumping Tool
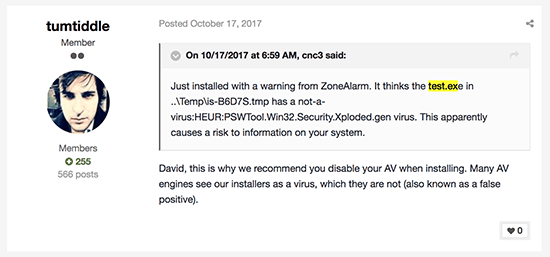
In October, a user complained that his anti-virus program was flagging one of the files dropped by the installer of an add-on for Microsoft's Flight Simulator.
Complaint about Flight Sim Security - Source: Fidus Information Security
Flight Simulator Developer Fights Piracy by Installing a Password-Dumping Tool Image
The add-on in question apparently gives users the chance to fly an Airbus A320 in the popular simulator, and it was developed by a company called FlightSimLabs (a.k.a. FSLabs). Another member of FSLabs' forum told the concerned user: "this is why we recommend you disable your AV when installing" and assured him that his security product was just giving him a false positive. Yesterday, it turned out that this wasn't the case.
After several other users complained about the problem over the last few days, researchers from Fidus Information Security decided to take a closer look. It turned out that in addition to setting up the Flight Simulator add-on, FSLabs' installer also dropped Chrome Password Dump on users' machines.
Chrome Password Dump is a free tool that can recover passwords saved in Google Chrome. It was developed by SecurityXploded, and it's supposedly useful for penetration testers and forensic investigators. While it may be used for legitimate purposes, its password harvesting functionality means that it's flagged by quite a few AV engines as malicious.
Let's just say that whether or not FSLabs used Chrome Password Dump for legitimate purposes is arguable. Fidus explained how they implemented it.
Upon installation of the add-on, the tool is extracted as test.exe and is saved in the %temp% folder. If executed, test.exe scrapes the usernames and passwords stored by Google Chrome and drops them in a text file called log.txt. Then, the login credentials are Base64 encoded, and they're sent over an insecure HTTP connection back to FSLabs.
The story picked up speed quite quickly, and the flight simulator developers realized that they had some explaining to do. In a statement posted on the company's forums, Lefteris Kalamaras, FSLabs' Founder, explained that Chrome Password Dump was put in the installer to track people who were pirating his company's add-ons. Apparently, he and his colleagues found a cracked version of FSLabs' software on torrent websites, and they wanted to learn who was responsible for it. The idea was that the tool would only be launched if the user was registering the product with a serial number and email address provided by the crackers. Those who had bought the product weren't affected, and the installer was designed to delete the test.exe file in case a legitimate serial number was used. Fidus' researchers confirmed that this is indeed true.
So, it wasn't a random password harvesting campaign. Even so, what were FSLabs thinking?
Quite apart from the fact that the password stealing software was never going to slip by unnoticed, this type of tools should never be used in such a way, regardless of whether the target is an Internet pirate or not. And let's not even mention the problem of relaying sensitive information over HTTP. FSLabs admitted that it was a mistake, removed Chrome Password Dump from an updated version of the installer, and promised that everyone requesting a refund would get their money back.
Sadly, saying "sorry" might not cut it. Some users are understandably outraged, and legal actions against the add-on developer are likely to follow. Software piracy is a big problem, make no mistake, but the developers must try and solve it using ethical, not to mention legal, methods only. Silently dropping password slurping tools on the machines of unsuspecting users isn't one of them.