Britney Spears' Instagram Followers Help Turla Malware Find Its Controlling Server
 Britney Spears has about 17 million Instagram followers who view, share, and comment on her pictures every day. Some of them are big fans. One user going by the handle 'asmith2155,' for example, was so beside himself with excitement when he was commenting on one of the pop star's pictures, that he lost the ability to form coherent sentences. At least that's what you'd think has happened. As researchers from ESET found out, however, asmith2155's comment was actually a specially crafted string that helped a backdoor created by the Turla APT group find its Command and Control (C&C) server.
Britney Spears has about 17 million Instagram followers who view, share, and comment on her pictures every day. Some of them are big fans. One user going by the handle 'asmith2155,' for example, was so beside himself with excitement when he was commenting on one of the pop star's pictures, that he lost the ability to form coherent sentences. At least that's what you'd think has happened. As researchers from ESET found out, however, asmith2155's comment was actually a specially crafted string that helped a backdoor created by the Turla APT group find its Command and Control (C&C) server.
APT stands for "Advanced Persistent Threat," and the term is used for describing hacking crews (who, in most cases, are state-sponsored) that attack high-profile targets with sophisticated malware. It must be said that when it comes to certain aspects of their modus operandi, the Turla gang is especially persistent.
For a while now, the initial point of its attacks has been the so-called watering holes. Basically, Turla picks websites that are likely to be visited by their targets and inject some code into them. ESET's experts saw the said code in the websites of a number of embassies, ministries of foreign affairs, and political organizations and noted that the threat actors have designed the strings to look like they belong to the Clicky Web Analytics platform. In reality, the code leads visitors to a fingerprinting JS file hosted on another breached website which determines the IP address of the potential victim. If the script decides that the visitor is "interesting," it pushes another JS file which installs a super cookie that tracks the victim's browsing habits and downloads a library that detects the installed browser plugins.
But where does Britney Spears' Instagram profile come in?
While monitoring the watering holes, ESET's experts noticed an interesting Firefox extension. Firefox extensions, the researchers noted, have been used by other APT groups in the past, so they couldn't help but take a look at it. Sure enough, it turned out to be a JavaScript backdoor that can read, download, upload, and execute files. There is one small detail, though. The backdoor can't work without a C&C.
Further investigation revealed the clever mechanism of locating the threat actors' server. The malware goes to a specific Instagram photo (in this case, it was uploaded by Britney Spears), screens the comments and looks for the one with the hash value of 183. The comment that matched the criteria was written by the aforementioned asmith2155.
Figure 1. Britney Spears Instagram Turla Malware Linking - Source: WeLiveSecurity
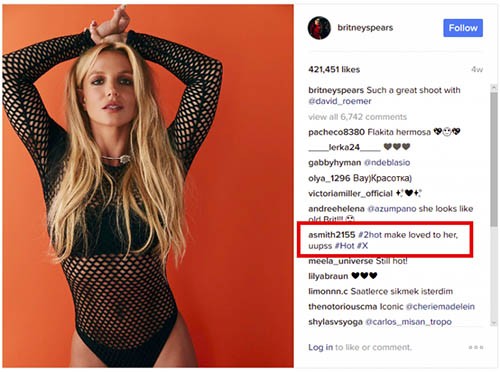
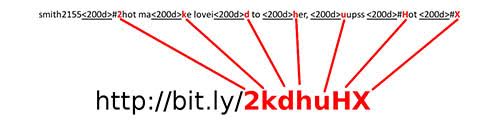
What you see above isn't what the malware sees, though. In the comment, there is a non-printable character, "<200d>" which is put in several places and is normally used to separate emojis. To Turla's backdoor, the comment looks like this:
smith2155<200d>#2hot ma<200d>ke lovei<200d>d to <200d>her, <200d>uupss <200d>#Hot <200d>#X
The malware uses regex to check for the first alphanumerical character after each <200d> and pieces the results together into a bit.ly shortened URL.
A graphic representation of the mechanism
The C&C finding mechanism is quite ingenious indeed, not least because the URL is basically hidden in plain sight. It would appear, however, that the Turla hackers are still testing it.
The bit.ly link resolves to "http://static.travelclothes[dot]org/dolR_1ert.php," and a quick check shows that it was clicked on just seventeen times back in February. In addition to this, due to a few changes that are about to be made to Firefox, the backdoor won't function properly in the browser's future versions.
It is unlikely that the changes will deter the Turla threat actors.