Vista Home Security 2012
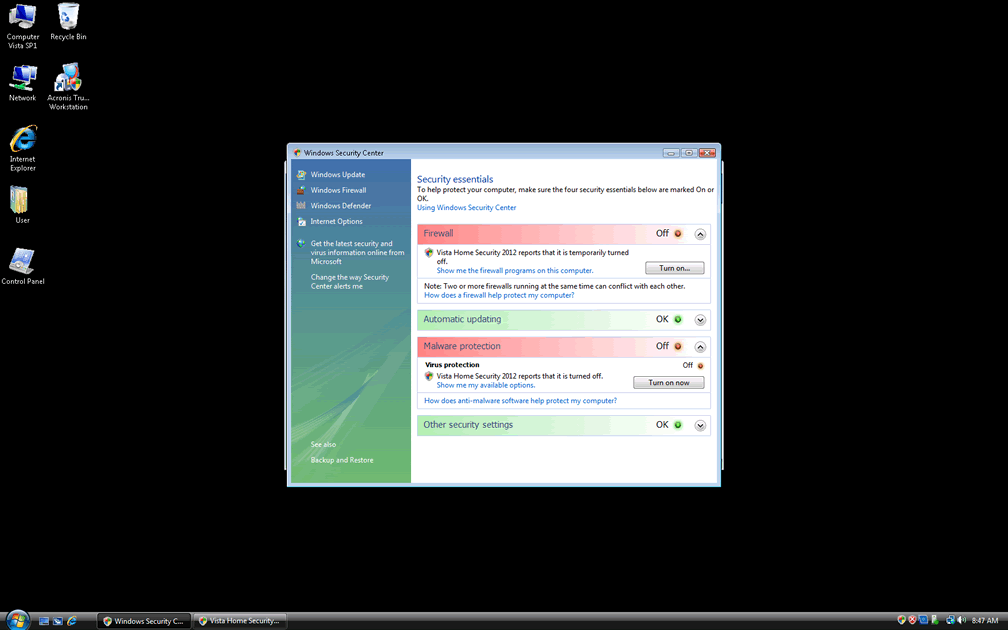
Vista Home Security 2012 Image
Ppn.exe is a harmful file process that can completely wreck a computer system. This process has also been known to show up as Kdn.exe. Vista Home Security is one of dozens of different versions of the Ppn.exe file process, an insidious rogue security application. Programs like Vista Home Security 2012 cause devastating effects on a user's computer and then extort the computer user. The aim of rogue security programs like these is to unnerve the computer user into giving them his credit card information.
Table of Contents
Clones, Copies, and Alternate Versions of Vista Home Security 2012
The Ppn.exe file process only has one known version, the Kdn.exe file. Both are exactly the same program. This file process has also been known to create other processes in the Task Manager, with similar three-letter names. You may ask, if there is only one known clone, then why was it mentioned before that there are dozens of versions of Ppn.exe? That is because Ppn.exe has a unique trait. It changes names and themes depending on the operating system running on the infected machine. Like a chameleon changing the color of its skin, Ppn.exe changes its appearance and name to match the (computer) user's operating system, which makes it extremely hard to detect. Therefore, Vista Home Security 2012 would be named XP Home Security 2012 in a system running Windows XP or Win 7 Home Security 2012 on a system using Windows 7. New names and skins for this program are released every day, making this terrible rogue anti-spyware application harder to track than traditional rogue security applications.
How Ppn.exe Turns into Vista Home Security 2012
Typically, Vista Home Security 2012 enters a computer through a Trojan infection. The Trojan will perform a fake Windows Automatic Update which will trigger the download and installation of the Ppn.exe file into the attacked machine. While Ppn.exe file installs on the infected device, it will detect the operating system that the computer is running and download the appropriate skin and change its name to match it. There are three main sets of possible disguises for the Ppn.exe file process: one for Windows Vista, one for Windows 7, and one for Windows XP. In each set, there is a huge amount of possible names and themes, with new ones being released every day. The skins in each set match its corresponding operating system's style and layout to look as authentic as possible. Vista Home Security 2012 is part of the set of disguises for computer systems running Windows Vista.
How Vista Home Security 2012 Tries to Steal Your Money
Vista Home Security 2012 uses harmful Trojans and scripts to cause harmful effects on your computer system. Some of the usual effects caused by Trojans bundled with Vista Home Security 2012 include:
- Disabled access to the computer user's own files and programs.
- Disabling of legitimate security applications found on the user's computer.
- Disabled connection to the Internet.
- Altered browser settings.
- Slow performance and constant alert messages.
Vista Home Security 2012 attempts to make the computer user believe these problems are caused by problems with the user's computer. Vista Home Home Security 2012 will prompt the (computer) user to enter his credit card information to get rid of the supposed problems. Don't give Vista Home Security 2012 your money; all of these problems are caused by Vista Home Security 2012 itself.
Aliases
4 security vendors flagged this file as malicious.
| Anti-Virus Software | Detection |
|---|---|
| Panda | Suspicious file |
| Sophos | Mal/FakeAV-MQ |
| F-Prot | W32/FakeAlert.PN.gen!Eldorado |
| CAT-QuickHeal | (Suspicious) - DNAScan |
SpyHunter Detects & Remove Vista Home Security 2012
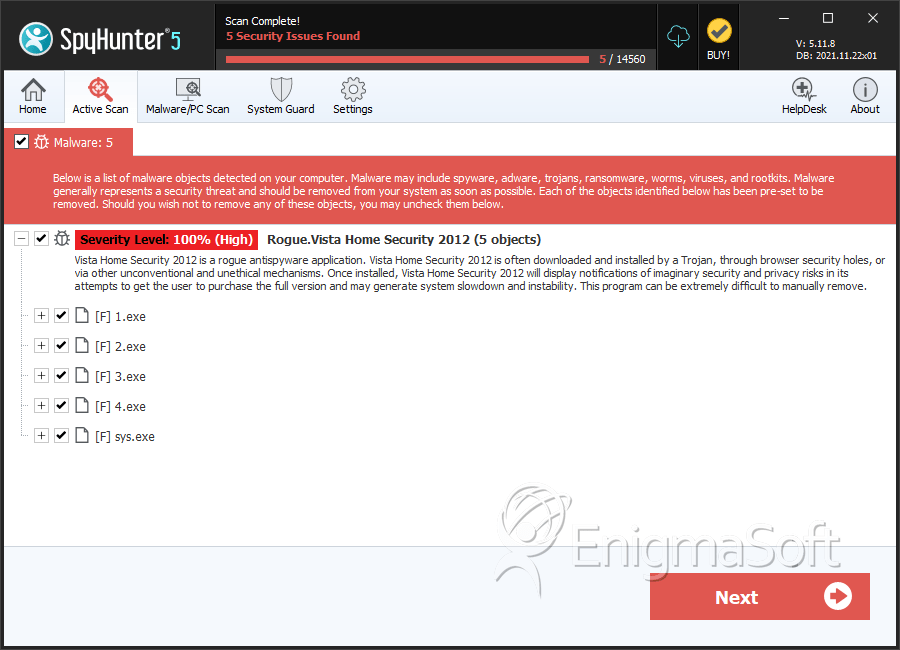
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | %AppData%\Local\[RANDOM CHARACTERS].exe | ||
| 2. | %Temp%\[RANDOM CHARACTERS] | ||
| 3. | %AppData%\Local\[RANDOM CHARACTERS] | ||
| 4. | %AppData%\Roaming\Microsoft\Windows\Templates\[RANDOM CHARACTERS] | ||
| 5. | %AllUsersProfile%\[RANDOM CHARACTERS] | ||
| 6. | 1.exe | 86ddd5aaf8c3d1e5b789adf88fd1bb0f | 0 |
| 7. | 2.exe | 4b03718e290ee47b5b06e0a49ccdf86e | 0 |
| 8. | 3.exe | 02819e7f6bc7484576beba460040ae25 | 0 |
| 9. | 4.exe | 3414baf3798a863f1a7ad5374734c38d | 0 |
| 10. | sys.exe | 3591cad46f9689df8bbc0f655f6b4d68 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.