VaultCrypt
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 950 |
| First Seen: | March 20, 2015 |
| Last Seen: | May 2, 2022 |
| OS(es) Affected: | Windows |
VaultCrypt is a ransomware infection that may cause computer users to lose access to their files. VaultCrypt uses the RSA 1024 encryption method to encrypt victims' files. Once these have been encrypted, VaultCrypt demands payments of a ransom to restore the encrypted files. VaultCrypt's ransom is one Bitcoin, which is currently worth around $300 USD. This is an anonymous cryptocurrency that allows these third parties to profit at the expense of computer users while remaining unidentified.
One of the reasons why VaultCrypt is particularly threatening is because VaultCrypt is a sophisticated work of threats that has been quite effective at encrypting victims' files. The payment website associated with VaultCrypt is well built and seems quite professional. Similar encryption ransomware infections will drop text files or other similar ransom notes on the victim's computer to explain the situation and demand payment. VaultCrypt uses a slightly different method. It appears that VaultCrypt will change the encrypted files' extension, appending .vault to the end of each file's name. When these files are opened, a pop-up message appears claiming that the file was 'Stored in Vault.' VaultCrypt's message directs computer users to the payment website in order to obtain the decryption key. To make this pop-up message appear, VaultCrypt makes changes to the infected computer's registry. By altering the Windows Registry, VaultCrypt can make Windows display the pop-up error message every time a .vault file is opened. VaultCrypt will encrypt Microsoft Office documents, image files, database files and archives in ZIP format.
Table of Contents
The VaultCrypt Payment Infrastructure and Methods
The VaultCrypt website is well built and, unfortunately, could well pass for the website for any large business. It is evidence of how effectual and lucrative strategies like VaultCrypt are when third parties establish Web pages with fake news, chat and customer support for their victims. VaultCrypt establishes a deadline for payment. In most cases, VaultCrypt threatens computer users, claiming that if the ransom is not paid within a week, the files will be eliminated. In fact, after the week, the amount the victim has to pay is increased. Malware researchers strongly advise against paying VaultCrypt's ransom, although computer users may not have a choice if an irreplaceable file was encrypted.
Backing up Your Files is Your Best Protection against VaultCrypt
The reason threat attacks like VaultCrypt are so effective is that most computer users are not particularly careful when it comes to backing up their files. In fact, if most computer users would backup their files regularly on an external drive or cloud encryption threat attacks like VaultCrypt would virtually disappear. Although earlier forms of encryption threats did not affect the Shadow Volume or System Restore (meaning that encrypted files could be recovered using these types of methods), VaultCrypt and newer attacks have become more sophisticated, also targeting these components to ensure that victims have no recourse but to pay for the encryption key. Because of this, PC security researchers strongly stress the importance of backing up all files regularly. This way, you will also not finance these third parties' operations by allowing them to continue producing threats like VaultCrypt.
VaultCrypt attacks can also be prevented using strong security measures. PC security researchers strongly advise computer users to use a reliable security program that is fully up-to-date to protect your computer at all times. However, security software is useless if it is not active and if it is not up-to-date. Many computer users may disable their security software when downloading files to increase the download speed or when gaming online to improve their latency. Doing this is a bad idea. Malware researchers also advise browsing the Web safely, avoiding shady websites and unknown links or file attachments.
SpyHunter Detects & Remove VaultCrypt
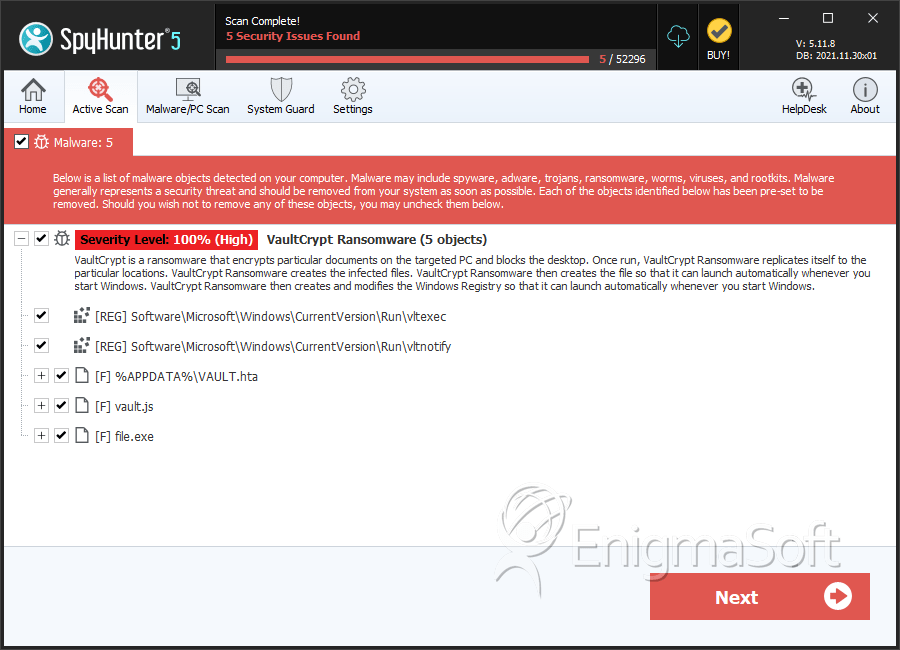
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | VAULT.hta | 207f6a7cf5933e00b575c7243ebef2f1 | 83 |
| 2. | VAULT.hta | 1cf60361078e1c2f1219d27c4b3e760c | 79 |
| 3. | VAULT.hta | c7e7c1a8ebd606638b7e89dc0daef677 | 72 |
| 4. | VAULT.hta | a4e778c80f2fb7a12253070aaedceb1d | 42 |
| 5. | VAULT.hta | 50ce889104fb97f0ce64108e91a14dba | 34 |
| 6. | VAULT.hta | f2ad12c745bb55e0a3600fe1b47eb72d | 32 |
| 7. | VAULT.hta | 99f8ac62c7e84cb5ea0e43004555b800 | 30 |
| 8. | VAULT.hta | 10196fbf29c1dc6916633dc1ee71ed8d | 30 |
| 9. | VAULT.hta | fc397b0266aec242714194bdf4938831 | 25 |
| 10. | VAULT.hta | 520002e0fb095fea87c5c9e1bcaff90f | 22 |
| 11. | VAULT.hta | 9340624438179b75aeafee270259684b | 22 |
| 12. | VAULT.hta | 8d6277f6c65e31272c4af4058d68d986 | 18 |
| 13. | VAULT.hta | e1fb0534c3edd45eed7bf29e61110723 | 12 |
| 14. | VAULT.hta | 7145e1cefed8cea6ded086dc888e95a5 | 12 |
| 15. | VAULT.hta | 220c94d6f9537e00ed18ffa2609da9a9 | 12 |
| 16. | VAULT.hta | 030dce1d07f9de6d8facb42d879a3405 | 10 |
| 17. | VAULT.hta | d4b7e4b65820162201a4eb151ffc1287 | 9 |
| 18. | VAULT.hta | c0b1e17fea1244fa5d996aa7493c4957 | 9 |
| 19. | VAULT.hta | 38bafa10b0151b7121b2f51e9bbedca8 | 9 |
| 20. | VAULT.hta | 0bd2e3e16476704b5f1ebd7dfee21e2e | 7 |
| 21. | VAULT.hta | 0fd543248a2eea14e74f5a9c281fc8ee | 6 |
| 22. | VAULT.hta | 3f0f572625cc70b281491875242ab391 | 6 |
| 23. | VAULT.hta | 86e51c7b49f33386712197164a65dac0 | 5 |
| 24. | VAULT.hta | d300125d32bac2c1db6045e8365d06cf | 3 |
| 25. | VAULT.hta | c478ef858ae078f68520cd5493d52c78 | 1 |
| 26. | VAULT.hta | 29754b1e157b7e2658fee20546f1385e | 1 |
| 27. | VAULT.hta | 1a4912c6623aaf08ae00e19e839c2e6c | 1 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.