Ukash Virus
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 1,880 |
| Threat Level: | 90 % (High) |
| Infected Computers: | 57,509 |
| First Seen: | August 8, 2012 |
| Last Seen: | October 24, 2025 |
| OS(es) Affected: | Windows |

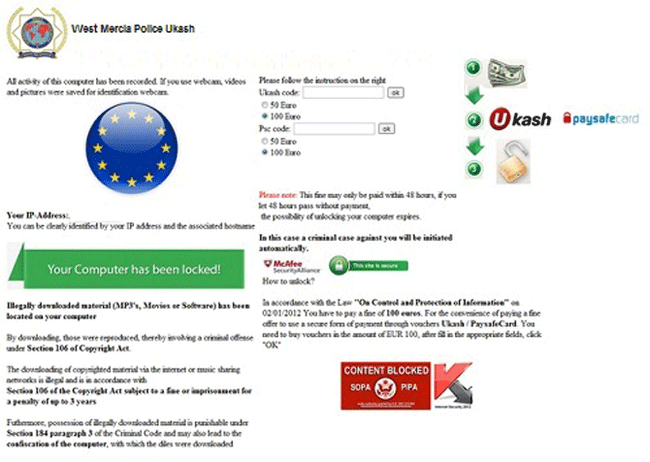
The so-called Ukash Virus is a ransomware Trojan that receives its name because Ukash Virus requires that its victims use Ukash (a legitimate money transfer service) to transfer the ransom funds. This dangerous Trojan infection is composed of a Winlocker component that basically blocks access to the infected computer system, disabling access to the infected computer system's desktop, Task Manager, command line, Registry Editor and other services and applications. There are countless variants of the Ukash Virus, designed to target various different countries in Europe and North America. ESG malware analysts strongly advise against paying the ransom that this malware infection tries to extort from its victims. Instead, variants of the Ukash Virus should be removed with the help of a reliable anti-malware application.
The Ukash Virus is characterized by its use of official police logos and threatening language in order to convince its victims that Ukash Virus is in fact a message displayed by the targeted country's police force. Although the Ukash Virus appears to have originated in the Russian Federation, its main targets are the various European countries. There are dozens of variants of the Ukash Virus, each targeting a specific country. Some examples of country-specific variants of the Ukash Virus include the Scotland Yards Ukash Virus, the Metropolitan Police Ukash Virus and the Strathclyde Police Ukash Virus (all three targeting computer systems in the United Kingdom), or the Fake Federal German Police (BKA) Notice and the 'Die offizielle Mitteilung des Bundeskriminalamtes' fake message infection (both targeting computer systems in Germany). Variants of the Ukash Virus have been spotted for most countries in Europe, including Spain, Italy, France, The Netherlands and Belgium.
Once the Ukash Virus infects the victim's computer, Ukash Virus will block access to the infected computer's files and applications, and instead displaying a large message that fills up the victim's screen. This message will be written in the language of the targeted computer system (whose location is probably detected through its IP address) and contain logos of a law enforcement agency belonging to the targeted computer system's country. For example, variants of the Ukash Virus targeting computer systems in the United States will display fake warning messages from the FBI. This message will claim that the victim's computer system was involved in illegal activities, such as downloading child pornography. In this message, Ukash Virus variants will threaten the victim with deletion of their data and prosecution unless they pay a fine using either the Ukash or the PaySafeCard money transfer service.
Table of Contents
Aliases
15 security vendors flagged this file as malicious.
| Antivirus Vendor | Detection |
|---|---|
| AVG | Pakes2_c.NRL |
| Fortinet | W32/Foreign.AOV!tr |
| Microsoft | Ransom:Win32/Urausy.E |
| Sophos | Troj/Ransom-AOV |
| Kaspersky | Trojan-Ransom.Win32.Foreign.lhds |
| Avast | Win32:Hoblig-B [Heur] |
| K7AntiVirus | Trojan ( 004b24781 ) |
| McAfee | RDN/Suspicious.bfr!bh |
| AVG | Downloader.Generic14.DSF |
| Fortinet | W32/Tracur.AM!tr.dldr |
| Ikarus | Trojan-Downloader.Win32.Tracur |
| Sophos | Mal/Generic-S |
| McAfee-GW-Edition | BehavesLike.Win32.Ramnit.dh |
| BitDefender | Gen:Variant.Jaik.4689 |
| McAfee | Artemis!BC5906995084 |
SpyHunter Detects & Remove Ukash Virus
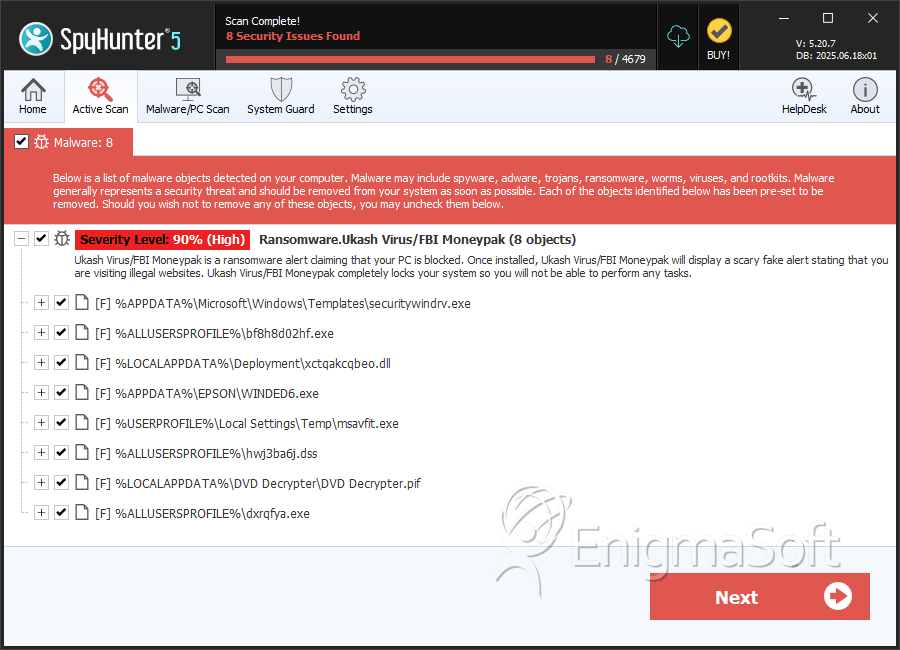
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | securitywindrv.exe | 0da8705f12382804c87d20ee58a4674c | 24 |
| 2. | bf8h8d02hf.exe | 1cbe49c0ebbeefbbe9f1c1fda9eebbe6 | 11 |
| 3. | xctqakcqbeo.dll | bc5906995084024aeab23bdccd0d689f | 7 |
| 4. | msavfit.exe | 9f5e6c75851b2ee4b10e3e3b783d10b7 | 5 |
| 5. | WINDED6.exe | 77c854a9e5b39829d2ffc15767106ad9 | 4 |
| 6. | hwj3ba6j.dss | 54f1a99f7cb18ed47756bb22e1681766 | 3 |
| 7. | DVD Decrypter.pif | feeebe883be3f5fe11a8033fb461ba55 | 2 |
| 8. | dxrqfya.exe | 85f908a5bd0ada2d72d138e038aecc7d | 2 |
| 9. | xaZYOVJW.exe | 4382872727fc8c0996fa315c599ecdf0 | 2 |
| 10. | dqnbdq7.dss | 6514a485b26fcca011121f42f188d3b2 | 2 |
| 11. | bzsbkotiu.exe | 35180a38939fe1b4368d804ae25e5a57 | 2 |
| 12. | wjthvwjb.dss | 9f2da2fd4fe9713d74acf0eb8fad8dc3 | 2 |
| 13. | ctfmon.exe | d6d5126353edcb1f91aa210c3742de01 | 2 |
| 14. | ubvhynpxh.exe | 3679444e7921794b3754ffb8ca80916b | 2 |
| 15. | audipbrd.exe | 6ea827e7f4d182b0cb538cb5048bbdb2 | 2 |
| 16. | vE0f7hC.exe | 9ae84c87978d6009950e02256cacfd4e | 1 |
| 17. | a6j2rftb.dss | 3113b50a73f66c90d9f9b82555ba5ddd | 1 |
| 18. | ilwfjrrfrf.dss | c5792b3e01620c4d64a62617cc9cac29 | 1 |
| 19. | r90lwlww.dss | dbc66a280086ab3c23c2dca7b49fa96c | 1 |
| 20. | lwo8z8rcl.dss | 496fea09b09d07f7b3a9d3834229702f | 1 |
| 21. | qmi6jdowjr.dss | ff6d455877d0eeb73a6c76a45d2b6ac7 | 1 |
| 22. | %AppData%\[RANDOM CHARACTERS].exe | ||
| 23. | %Temp%\[RANDOM CHARACTERS].exe | ||
| 24. | bunk.exe | bb29ba1cad79dcb26c986ecc92d76b4e | 0 |
| 25. | kyuba.exe | 15945e4dca232d306363340b1a53f21b | 0 |
| 26. | MSPAINT.EXE | d3448fb158b500704144fd75ec94c189 | 0 |
| 27. | F5753306.cpp | 12f3c8bc428f4e2c2b547cc20ac6db87 | 0 |