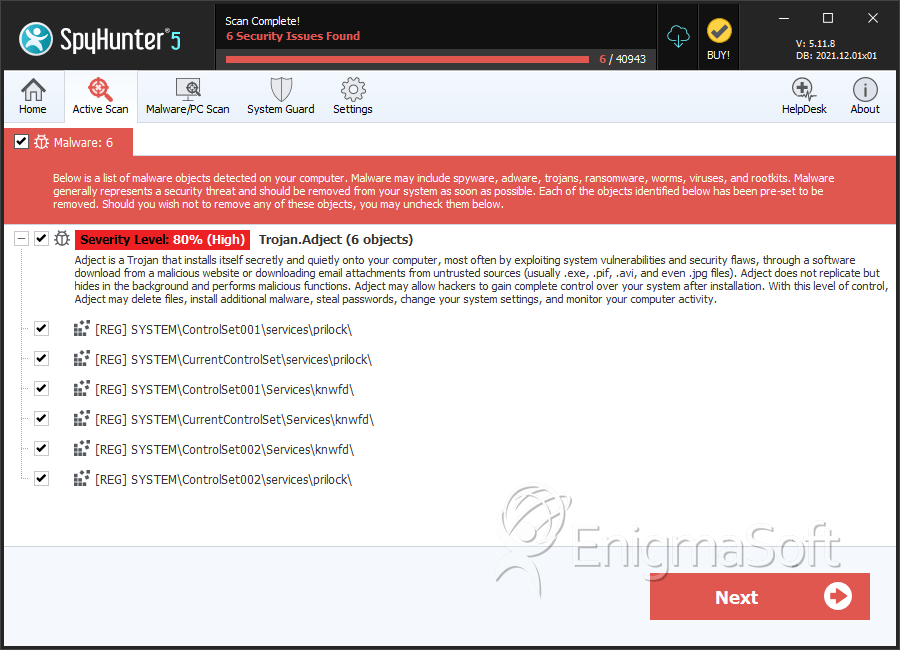
Trojan.Adject
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Ranking: | 13,306 |
| Threat Level: | 80 % (High) |
| Infected Computers: | 3,642 |
| First Seen: | March 8, 2018 |
| Last Seen: | September 14, 2023 |
| OS(es) Affected: | Windows |
Trojan.Adject is a detection name, which not all AV vendors utilize in their databases. The Trojan.Adject detection name points to a a generic Trojan, which is often found on fake software update packages and cracked copies of shareware. Threat actors may use Trojan.Adject to inject HTML and JavaScript code on Web pages loaded by compromised users. Trojan.Adject can be used to divert Web traffic to phishing pages, direct users to download other threats and show advertisements that are not native to pages. The Trojan.Adject threat may be flagged by AV engines as:
- Trojan-Clicker.Win32.VB.dn
- Win32/TrojanClicker.VB.DN
- SecurityRisk.Downldr
- MEM:Trojan-Spy.Win32.Agent.gen
- Malware.UDM!0.BEBCD1E
- UDS:DangerousObject.Multi.Generic
Trojan.Adject is reported to write files to the Windows directory and add tasks to the task scheduler. The Trojan.Adject program might be found in the startup list on Windows and drop files to the AppData directory. We have seen Trojan.Adject write 'cryptfd.sys' and 'wfcre.sys' to 'C:\Windows\System32\drivers' and 'C:\Users\username\AppData\Roaming\curl.' Also, Trojan.Adject might add 'HKLM\System\ControlSet001\Services\wfcre\wfcre' and 'HKLM\System\ControlSet001\Services\cryptfd\cryptfd' to the Windows registry. That way the Trojan can boot with Windows and potentially circumvent some detection mechanisms. Trojan.Adject might change the Internet settings and register a background service to avoid detection. PC users who notice strange hyperlinked words and experience many browser redirects should run a complete computer scan with a reputable cybersecurity utility and remove the files related to Trojan.Adject safely.
SpyHunter Detects & Remove Trojan.Adject