Trojan.Dropper
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 90 % (High) |
| Infected Computers: | 3,496 |
| First Seen: | July 24, 2009 |
| Last Seen: | May 4, 2024 |
| OS(es) Affected: | Windows |
A Trojan.Dropper is designed to deliver a payload onto the victim's computer system. However, a Trojan.Dropper will usually lead a large-scale attack, usually not the end infection itself. Typically, one of the main goals of computer criminals is to find ways to install malware onto their victim's computer without alerting the victim of the intrusion. A Trojan.Dropper is a typical method that is quite common. Typically, a Trojan.Dropper contains a malware infection within itself which is designed to deliver the infection by copying it onto the victim's computer's file system. A Trojan.Dropper will usually install and execute the malware installed and then will often delete itself or simply remain harmless on the victim's computer system.
A Trojan.Dropper will usually be confusing to the victim, and designed to cause no symptoms. A typical example of a Trojan.Dropper is a fake screen saver which, when opened, will simply display an error message. However, even though the error message may look genuine, it will actually have been part of the Trojan.Dropper's tactics to install its payload without the user being aware of the problem. Many Trojan.Dropper infections will include an encrypting algorithm of some kind of obfuscator or packing algorithm to make their detection and removal much more difficult than normal.
Usually, a Trojan.Dropper is created as a way to distribute malware, since a Trojan.Dropper is relatively cheap and easy to distribute. A Trojan.Dropper is also low risk for the criminals that create it, since it is easy for them to cover their tracks when there are several steps to an infection. However, one of the features of Trojan.Dropper infections that make them attractive to criminals is that they can be easily disguised by simply changing their icon and file name. The payload of a typical Trojan.Dropper will vary from one case to the next. Typically, they will drop executable files, which can then infect the victim's computer system or download malware from a remote location.
There are few symptoms associated with a Trojan.Dropper. Some kinds of Trojan.Dropper infections will display a fake error message while dropping their payload. However, most of the time a Trojan.Dropper will display no signs of infection at all. Usually, the symptoms on an infected computer system will have been caused by the Trojan.Dropper's payload rather than by the dropper. Some examples of Trojan.Dropper infections will be associated with rootkits that hide the Trojan.Dropper's payload and may also make changes to the System's settings and the Windows Registry.
Table of Contents
Aliases
15 security vendors flagged this file as malicious.
| Anti-Virus Software | Detection |
|---|---|
| AVG | RemoteAdmin.ARL |
| Fortinet | Riskware/ESurveiller |
| Ikarus | not-a-virus:Monitor.Win32.007SpySoft.308 |
| Sophos | e-Surveiller |
| AntiVir | SPR/Tool.E.Surveiller.D |
| F-Secure | Application.E.Surveiller |
| Kaspersky | not-a-virus:RemoteAdmin.Win32.eSurveiller.120 |
| eSafe | Virus in password protected archive |
| F-Prot | W32/eSurveiller.A |
| K7AntiVirus | Unwanted-Program |
| McAfee | Generic PUP.d |
| Panda | Trj/OCJ.A |
| AVG | Generic29.CEHH |
| Fortinet | W32/Injector.JLH!tr |
| Ikarus | MSIL |
SpyHunter Detects & Remove Trojan.Dropper
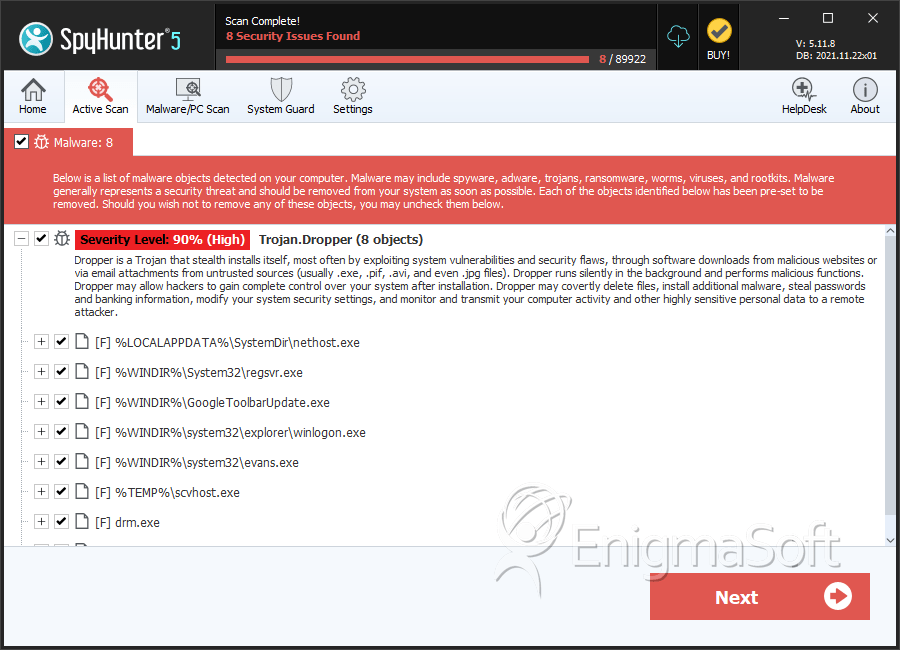
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | hodhTBky6vN1.exe | e090572a3eb5ac6f1453926eae14ecec | 3,349 |
| 2. | regsvr.exe | e9f7627d4710e414b579003332287f05 | 32 |
| 3. | GoogleToolbarUpdate.exe | ce7679af9d8ad929a58e4398a8d382f8 | 7 |
| 4. | winlogon.exe | 155cca87bd1630c1550c15eff43c2b7a | 5 |
| 5. | evans.exe | fc1c976f0884c1b8e70b76a17d4ab6a3 | 4 |
| 6. | scvhost.exe | b751e973a0fa7cffcf60a548552ce45e | 2 |
| 7. | drm.exe | ccd63de22be14961e4357cca58eb8c5c | 1 |
| 8. | vscrtapp.exe | 1aca09c5eefb37539e86ec86dd3be72f | 1 |
| 9. | CLADD | 66e10615b5a98f6233650e7c01c8583d | 0 |
| 10. | CLADD | 3fd6fa1030e552338d2e5f5d4225342b | 0 |
| 11. | CLADD | bafbe70a02269df4b56ef48d9e250639 | 0 |
| 12. | CLADD | 007462b240ed46276d04935dfb59beb1 | 0 |
| 13. | CLADD | 2415eddcabb08b23deaf9d9e18e4b22d | 0 |
| 14. | CLADD | e2c82136ef5c002de2822a8ee7b36d4e | 0 |
| 15. | CLADD | 51de224c0942f0be15bb6f3eea8f27d4 | 0 |
| 16. | CLADD | 827c1269a52208f5094c36402015ef17 | 0 |
| 17. | CLADD | 50ae8903665b931c4553e7802003aafd | 0 |
| 18. | mediacodec.exe | a75d2ed1598b587cd5d5cd0b15163c9d | 0 |
| 19. | init.exe | fe9b99190fbbfcb4de1dbe77539a69c6 | 0 |
| 20. | ddexpshare.exe | d1b6f11c70a01983cd9d4822f5b06174 | 0 |
| 21. | svhost.exe | 979235c02243347568330cacbd00d739 | 0 |
| 22. | Svchost.exe | efbbda1cba44bc9d853269ed1f4efa41 | 0 |
| 23. | explorers.exe | 8135ad5d2966e8791cae5e80a79d8e87 | 0 |
| 24. | lsass.exe | 0d71c6ab6cbb7e701dcef8b1accf547d | 0 |
| 25. | winsys.exe | 166b5b6018e3475bedb35ae0d0eb64b2 | 0 |
| 26. | winsys.exe | ef019c4bdaffab7396649b6b072860a1 | 0 |
| 27. | win32.exe | bc588ff0a21c11d80af7d62584d4ab15 | 0 |
| 28. | new order.exe | f9da7ecfd5d1ac2510ca9113995f3b94 | 0 |
