PayDay Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 119 |
| First Seen: | December 13, 2016 |
| Last Seen: | October 7, 2019 |
| OS(es) Affected: | Windows |
The PayDay Ransomware was spotted by security analysts while investigating a Trojan associated with an image from the Payday game franchise from Overkill Software. Investigators report that the PayDay Ransomware is an encryption Trojan based on the Hidden Tear project published by Utku Sen on Github.com. The PayDay Ransomware ranks amongst threats such as the Satan666 Ransomware and the HappyLocker Ransomware.
Table of Contents
The PayDay Ransomware Aims to Pry Money Off of Your Hands Just as the Protagonists from the Game
The PayDay Ransomware is aimed at PC users who speak Portuguese and leaves the email catsexy@protonmail.com for contact between victims and operators. Researchers note that the PayDay Ransomware can encrypt data hosted on local drives and removable storage such as USB drives and media players. You can recognize enciphered files by the '.sexy' extension placed after the original file extension. For example, 'Modest Mouse - Float On.mp3' is transcoded to 'Modest Mouse - Float On.mp3.sexy.' The PayDay Ransomware is designed to use an AES-256 cipher and encode the content of data containers with the following extensions:
.RAW, .TIF, .GIF, .PNG, .BMP, .3DM, .MAX, .ACCDB, .DB, .DBF, .MDB, .PDB, .SQL, .SAV, .SPV, .GRLE, .MLX, .SV5, .GAME, .SLOT, .DWG, .DXF, .C, .CPP, .CS, .H, .PHP, .ASP, .RB, .JAVA, .JAR, .CLASS, .AAF, .AEP, .AEPX, .PLB, .PREL, .PRPROJ, .AET, .PPJ, .PSD, .INDD, .INDL, .INDT, .INDB, .INX, .IDML, .PMD, .XQX, .XQX, .AI, .EPS, .PS, .SVG, .SWF, .FLA, .AS3, .AS, .TXT, .DOC, .DOT, .DOCX, .DOCM, .DOTX, .DOTM, .DOCB, .RTF, .WPD, .WPS, .MSG, .PDF, .XLS, .XLT, .XLM, .XLSX, .XLSM, .XLTX, .XLTM, .XLSB, .XLA, .XLAM, .XLL, .XLW, .PPT, .POT, .PPS, .PPTX, .PPTM, .POTX, .POTM, .PPAM, .PPSX, .PPSM, .SLDX, .SLDM, .WAV, .MP3, .AIF, .IFF, .M3U, .M4U, .MID, .MPA, .WMA, .RA, .AVI, .MOV, .MP4, .3GP, .MPEG, .3G2, .ASF, .ASX, .FLV, .MPG, .WMV, .VOB, .M3U8, .CSV, .EFX, .SDF, .VCF, .XML, .SES.
A Decryptor is Offered for $950 on the Catsexy@Protonmail.com Email Address
The encryption procedure employed within the PayDay Ransomware is secure, and decryption is impossible without the proper private key and software. The managers behind the PayDay Ransomware direct users to make a payment to the wallet address 1HGYr8g4Jv9EH6qgvEPFFFN9LYMkivFP7L using Bitcoins. At the time of writing this, $950 would allow you to obtain 1.2174 BTC from services like Localbitcoins.com. If you take into consideration the average wage in Brazil for 2016 that is $600 you will find that paying the ransom is not a viable option for most users. Computer users can counter threats like the PayDay Ransomware and the NMoreira Ransomware by being prepared. Installing a trusted anti-malware shield is a must in 2016, and a good backup manager should allow you to create backup images with ease. Do remember to store your archives and backups on unmapped drives to avoid contamination and protect your files. If you are presented with '!!!!!ATENÇÃO!!!!!.html' (!!!!!ATTENTION!!!!!.html) on your desktop you are likely to face the PayDay Ransomware which shows the following message:
'Seus arquivos foram Sequestrados!
os seus documentos, banco de dados, downloads, fotos e outros arquivos importantes foram criptografados utilizando o algoritmo com uma senha alfa-numérica de 150 caracteres gerada a partir deste computador e enviada para um servidor secreto na Internet onde somente eu tenho acesso.
O que fazer?
Para obter essa senha e descriptografar seus arquivos, você terá que pagar uma quantia de R$950,00 em BTC (BITCOIN). Para efetuar o pagamento e obter a senha, siga este pequeno manual:
1. Crie uma carteira BTC aqui:
2. Compre R$950,00 BTC com dinheiro em: localbitcoins.com
3. Envie os BTCs comprados para o endereço: [34 random characters]
4. Acompanhe a transferência em: blockchain.info/address/[34 random characters]
5. Após o pagamento ser confirmado, envie-me um email requisitando a Senha: CATSEXY@PROTONMAIL.COM
6. Logo após, enviarei um arquivo compactado contento dois arquivos: um Decrypter em .exe e a Senha em um .txt
Importante:
1. Ninguém pode te ajudar, a não ser eu!
2. Você tem apenas 120 Horas (5 dias) para efetuar o pagamento, caso o contrario eu deletarei a senha.
3. É inútil instalar/atualizar o software Anti Vírus, formatar o computador, fazer BO na delegacia, etc.
4. Seus arquivos só poderão ser descriptografados depois do pagamento.
5. A,pos você descriptografar seus arquivos, formate seu comutador, instale um bom Anti Vírus e tome mais cuidado onde clica'
Translated into English:
'Your files were encrypted!
Your documents, database, downloads, photos, and other important files were encrypted using the algorithm with a 150 characters alpha-numeric password generated for this computer and sent to a secret server on the Internet where only I have access.
What to do?
To get this password and decrypt your files, you will have to pay an amount of $950.00 in BTC (BITCOIN). To make the payment and obtain the password, follow this small manual:
1. Create a BTC portfolio here: blockchain.info
2. Buy $950,00 BTC with cash at: localbitcoins.com
3. Send the purchased BTCs to the address: [34 random characters]
4. Follow the balance at: blockchain.info/address/[34 random characters]
5. After payment is confirmed, send me an email requesting the Password: CATSEXY@PROTONMAIL.COM
6. Soon after, I will send a compressed file containing two files: a Decrypter in .exe and the Password in a .txt
Important:
1. No one can help you but me!
2. You only have 120 Hours (5 days) to make the payment, otherwise I will delete the password.
3. It is useless to install / update the Anti Virus software, format the computer, submit a report to the police station, etc.
4. Your files can only be decrypted after payment.
5. You can decrypt your files, format your drives, install a good Anti Virus and be more careful where you click'
SpyHunter Detects & Remove PayDay Ransomware
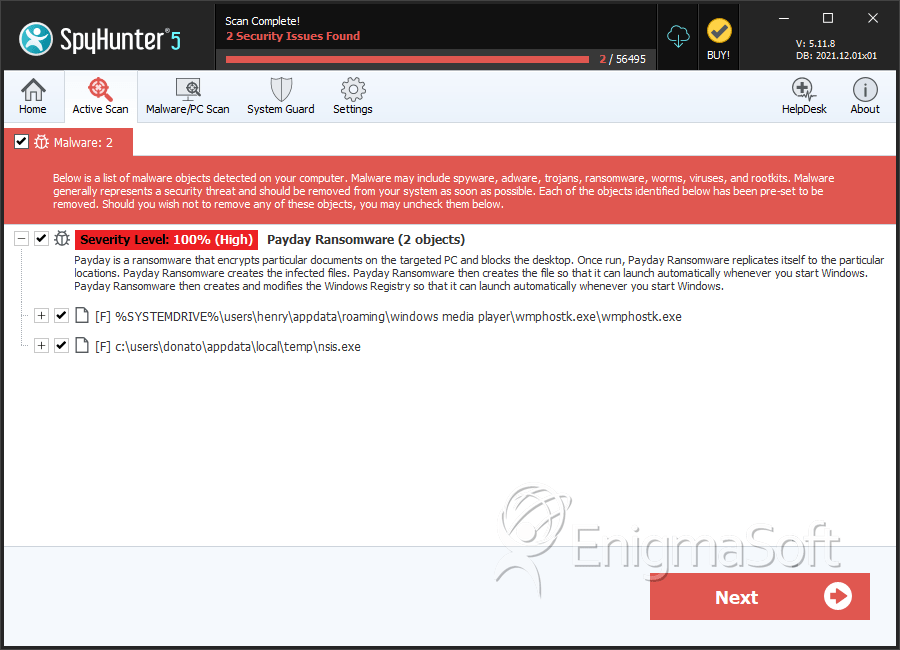
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | wmphostk.exe | 941fe30251abc09b0c9384f319bd635e | 78 |
| 2. | nsis.exe | c8abe202c373acfdf8aef1ed7952e109 | 1 |