NanoLocker Ransomware
The NanoLocker Ransomware is a relatively new player on the cryptomalware scene that surprised researchers with advanced spread techniques. The NanoLocker Ransomware is a Trojan that is deployed via traditional spam emails and the Nuclear Exploit Kit. Additionally, the NanoLocker malware is involved in many MiTM (Man-in-The-Middle) attacks across the globe. As you may already know, Ransomware Trojans are used by con artists to encrypt their victim's files of and demand payment in exchange for the decryption of their files. Cryptomalware such as the NanoLocker, CryptoJoker and the CryptoWall are increasingly popular due to their flexibility and irreversible effect on computer systems.
The developers of the NanoLocker Ransomware seems to employ the same tried-and-true practices that we have seen with the RSA 4096 Ransomware and the Shade Ransomware. The NanoLocker Ransomware might use the AES-256 encryption algorithm that is favored by many to encrypt your data. The NanoLocker Ransomware may scan your local and network hard drives for images, videos, and documents that are not bigger than 50MB and encrypt them. Also, the creators of the NanoLocker malware appear to keep their 'Command and Control' servers in the TOR network to avoid being traced by law enforcement authorities. Additionally, there are samples of the NanoLocker Ransomware that feature stolen SSL certificates that were seen in campings involving Zbot and EyeStye and may evade security scans preliminary. Another interesting trait of the NanoLocker Ransomware is that it might employ ICMP (Internet Control Message Protocol) channels to relay data to its remote host located on an ONION domain. The ransom note that the NanoLocker Ransomware might leave may be an HTML, JPEG and TXT file that might direct users to write an email to a disposal email box from NeoEmailBox.com and Notsharingmy.info. Most cryptomalware is crafted to demand payment in Bitcoins that can not be traced and, in many cases, victims are required to pay more than $800 for their data. A few might consider themselves 'lucky' when infected with a strand of the Ransom32 cryptomalware that does not require more than $100 for the decryption key.
However, you should not trust the con artists behind the NanoLocker Ransomware to fulfill their end of the bargain and need to act preemptively. Malware researchers recommend users to install a backup system that can upload their files on cloud services like the Google Drive and store another backup on a removable drive at your disposal. Installing a renowned anti-malware suite to counter the NanoLocker Ransomware is a must.
SpyHunter Detects & Remove NanoLocker Ransomware
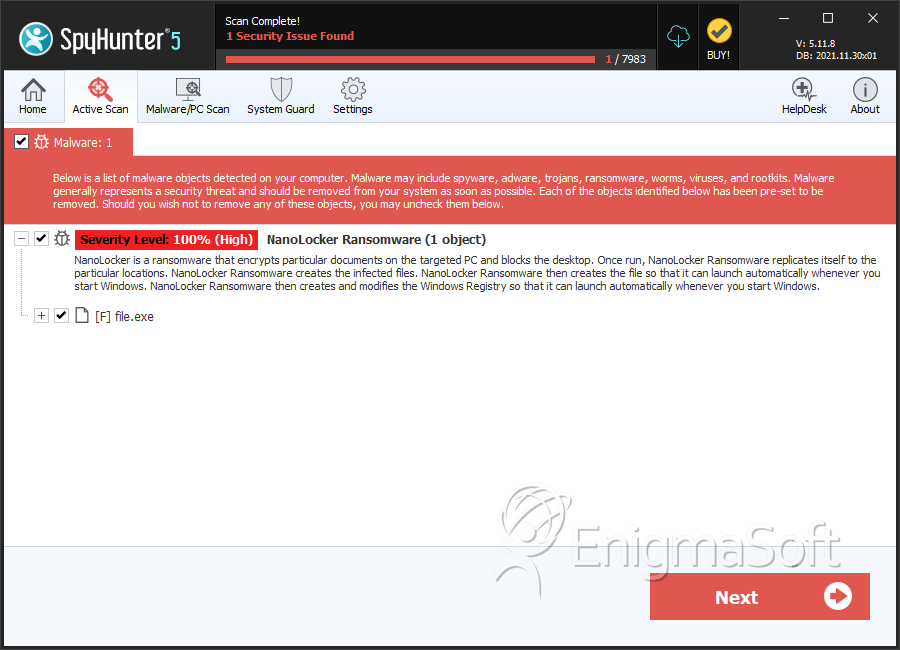
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | f2a344f465b7d7db3c8db0af922ef9eb | 0 |
| 2. | file.exe | 24273ce5ca8e84c52b270b52659304a8 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.