CryptoWall Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Ranking: | 19,458 |
| Threat Level: | 100 % (High) |
| Infected Computers: | 4,837 |
| First Seen: | May 12, 2014 |
| Last Seen: | March 27, 2025 |
| OS(es) Affected: | Windows |
CryptoWall Ransomware Image
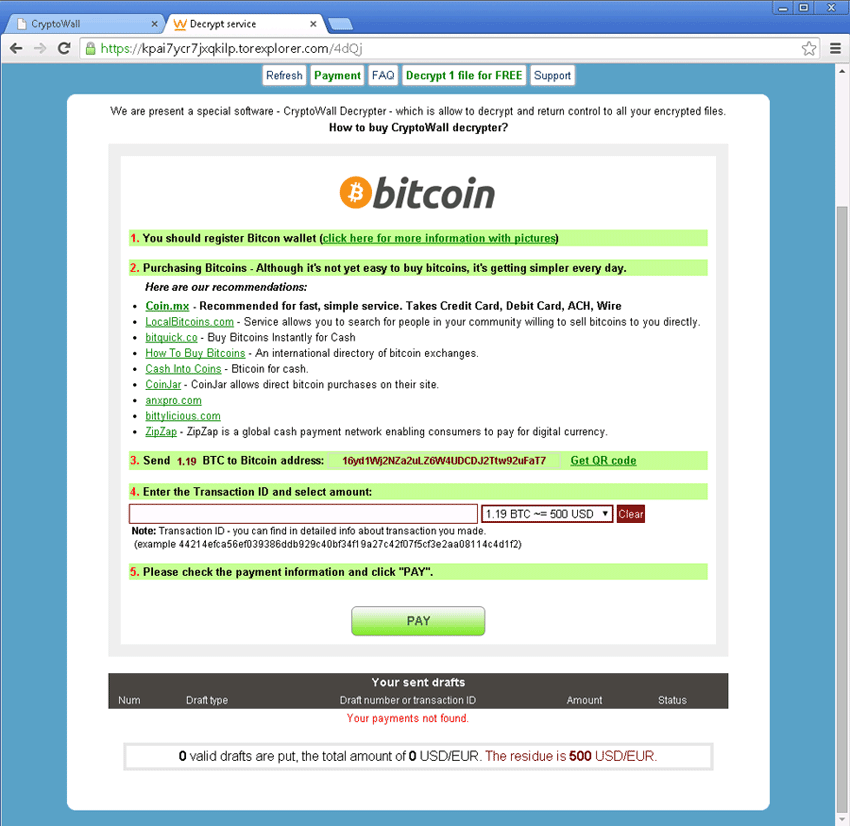
The CryptoWall Ransomware is a ransomware Trojan that carries the same strategy as a number of other encryption ransomware infections such as Cryptorbit Ransomware or CryptoLocker Ransomware. The CryptoWall Ransomware is designed to infect all versions of Windows, including Windows XP, Windows Vista, Windows 7 and Windows 8. As soon as the CryptoWall Ransomware infects a computer, the CryptoWall Ransomware uses the RSA2048 encryption to encrypt crucial files. Effectively, the CryptoWall Ransomware prevents computer users from accessing their data, which will be encrypted and out of reach. The CryptoWall Ransomware claims that it is necessary to pay $500 USD to recover the encrypted data. The payment is demanded using TOR and Bitcoins in order to maintain the recipients' anonymity. Malware researchers strongly advise against paying the CryptoWall Ransomware ransom. This only encourages ill-minded persons to continue carrying these types of attacks and does not guarantee that you will recover your data.
Table of Contents
Fake Updates and Spam Emails may Bring the CryptoWall Ransomware to Your Computer
The CryptoWall Ransomware is distributed as a fake update for applications such as Adobe Reader, Flash Player or the Java Runtime Environment. These types of updates may be offered in pop-up windows when you visit unsafe websites or when a Potentially Unwanted Program is installed on your computer. The CryptoWall Ransomware also may be distributed using spam email attachments and other typical threat delivery methods. Apart from encrypting your software, the CryptoWall Ransomware will also drop the files DECRYPT_INSTRUCTION.txt, DECRYPT_INSTRUCTION.html and DECRYPT_INSTRUCTION.url into directories where the CryptoWall Ransomware has encrypted data. The CryptoWall Ransomware uses the following ransom message to demand payment:
Decrypt service
Your files are encrypted.
To get the key to decrypt files you have to pay 500 USD/EUR. If payments is not made before [date] the cost of decrypting files will increase 2 times and will be 1000 USD/EUR Prior to increasing the amount left: [count down timer]
We are present a special software - CryptoWall Decrypter - which is allow to decrypt and return control to all your encrypted files. How to buy CryptoWall decrypter?
1.You should register Bitcoin waller
2. Purchasing Bitcoins - Although it's not yet easy to buy bit coins, it's getting simpler every day.
3. Send 1.22 BTC to Bitcoin address: 1BhLzCZGY6dwQYgX4B6NR5sjDebBPNapvv
4. Enter the Transaction ID and select amount.
5. Please check the payment information and click 'PAY'.
Avoid paying this ransom. Instead remove the CryptoWall Ransomware using a reliable, fully updated security program and then recover your files from an external back-up.
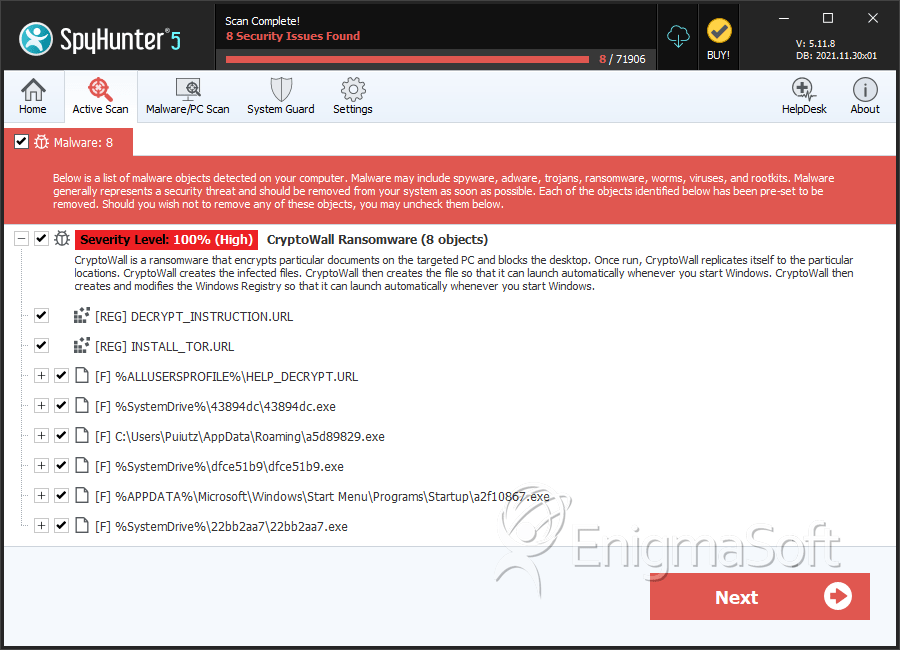
SpyHunter Detects & Remove CryptoWall Ransomware
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | HELP_DECRYPT.URL | 68bab4a48588991342ca900e7b3db1d8 | 54 |
| 2. | a5d89829.exe | edfeb771395e1807109712a2bf158599 | 5 |
| 3. | 43894dc.exe | 517d709b1b99fa87ddfe61950a93cf5c | 4 |
| 4. | dfce51b9.exe | 418fb443bfbc6834de21a4dadbbb4bbb | 3 |
| 5. | a2f10867.exe | 7f919abf4c32b34d576c81564045f98b | 2 |
| 6. | 22bb2aa7.exe | fc70fcc84636f1ac405e85ab375e6323 | 1 |
| 7. | 6ae66a4.exe | 860f2b9c56a56c0f18a7f2e4c1541fed | 1 |
| 8. | a5b2077d.exe | 687d2936249b2ab7387e9336bddf23ef | 1 |
| 9. | deyct-a.exe | ce57a4f528ebb078f9bba3e72dc953f1 | 1 |
| 10. | ivsposkhf2.exe | 3d238f4934dad0b8724acce5800a5e63 | 1 |
| 11. | qnemvp.exe | 467dd942e4f3386bb7e8dd309c21d558 | 1 |
| 12. | DECRYPT_INSTRUCTION.html | ||
| 13. | DECRYPT_INSTRUCTION.url | ||
| 14. | DECRYPT_INSTRUCTION.txt | ||
| 15. | 11a2c84.exe | f97d91f8aebbce4628664231184af5a1 | 0 |
| 16. | onewindow1s.jpg | 845f94f481f32c883692f6c8bb4946cb | 0 |
| 17. | name | 45463800b662da73ea35db76eca79630 | 0 |
| 18. | file.exe | db2758a5be38512e93ab155de25d71e3 | 0 |
