Karmen Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 71 |
| First Seen: | March 16, 2017 |
| Last Seen: | May 2, 2022 |
| OS(es) Affected: | Windows |
The Karmen Ransomware is a ransomware Trojan that is part of a RaaS (Ransomware as a Service) campaign. The Karmen Ransomware administrates its Command and Control servers, payment, and various other aspects of the attack. However, con artists may take charge of distributing the Karmen Ransomware through their networks by hiring the ransomware creators instead of creating the ransomware Trojans themselves. Typically, ransomware Trojans like the Karmen Ransomware are distributed through corrupted spam email attachments and various known tactics, such as bogus software distributed on Torrent networks or hacking into poorly protected computers directly.
Table of Contents
Hidden Tear and Its Offsprings
The Karmen Ransomware was first observed on March 2017 being used in attacks against computer users in English and German speaking regions. This, however, does not mean that computer users in other parts of the world are immune to the Karmen Ransomware or this threat may not manage to find its way into computers in other parts of the world. The Karmen Ransomware and its associated RaaS is based on the HiddenTear project. This was an open source ransomware engine published for 'educational purposes' and which has spawned countless ransomware attacks around the world. Even though HiddenTear was removed from the open Web shortly after the first attacks involving its code started to appear, HiddenTear still forms a large percentage of ransomware Trojan attacks and is freely available on the Dark Web. The Karmen Ransomware RaaS providers take a cut of 20% from all attacks, while distributors receive the other 80% of the profits. Con artists hiring the Karmen Ransomware RaaS are provided with a Web panel to monitor the attacks and receive support from the Karmen Ransomware's developers.
How the Karmen Ransomware may Force Computer Users Pay a Ransom
The Karmen Ransomware runs in an executable file named 'joise.exe' that is disguised as a program named 'Helper' with the description 'Microsoft Helper' (of course, the Karmen Ransomware does not help in any way, nor is it related to Microsoft!). When the Karmen Ransomware infection is installed, it scans all drives on the infected computer and creates a list of the files to be encrypted during the attack. The Karmen Ransomware encrypts numerous file types, including images, videos, and documents of various types. The files that have been encrypted in the Karmen Ransomware attack are easy to recognize because the Karmen Ransomware will change their names. The Karmen Ransomware adds the extension '.grt' to each affected file's name. Once the Karmen Ransomware has encrypted a file, it will no longer be accessible, and no application on the victim's computer should be able to open the affected file correctly. The Karmen Ransomware displays an application window with the name 'Karmen Decrypter,' which includes a ransom note written both in English and German. The contents of the Karmen Ransomware ransom note read as follow:
'Files encrypted
All files are encrypted! Please follow the mind. In order to get the key to decrypt send this amount to our wallet Bitcoin.
Decrypt files automatically.
Interference with the program - can leave you without files.'
Updates and Improvements of the Karmen Ransomware
The version of the Karmen Ransomware analyzed in this report is version 2.4, which demands the payment of a ransom of 0.20150565 Bitcoin, or $246 USD at the current exchange rate. PC security researchers strongly advise computer users to avoid paying the Karmen Ransomware ransom. It is entirely possible that new versions of the Karmen Ransomware will continue to appear. This is especially true regarding RaaS ransomware since each new user of the Karmen Ransomware infection may modify it to suit their needs. It is necessary to take preventive measures to ensure that your data is protected from the Karmen Ransomware. This includes creating backup copies of all files and installing a reliable security program that is fully up-to-date to intercept threats like the Karmen Ransomware before it carries out its attack.
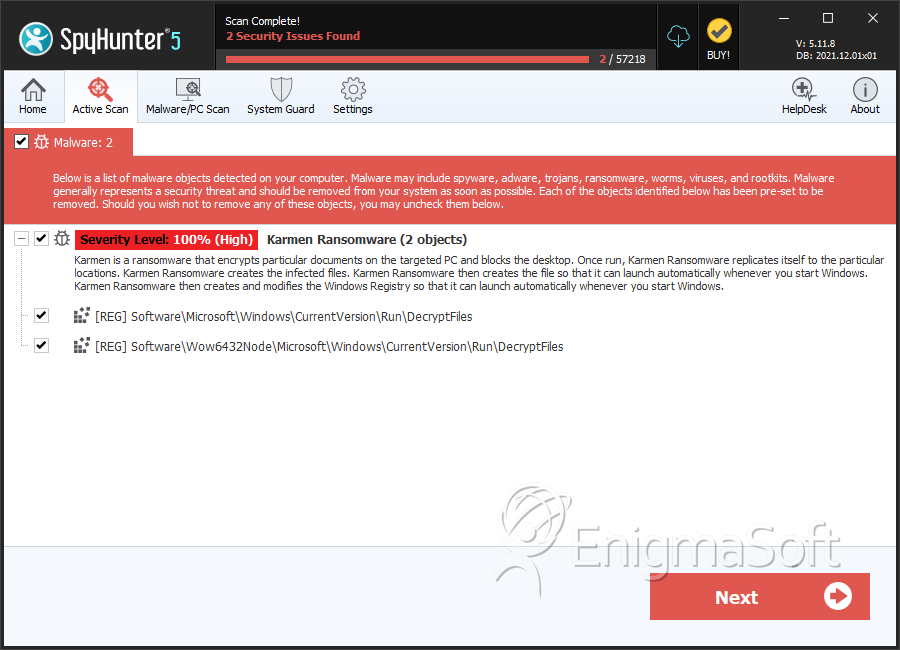
SpyHunter Detects & Remove Karmen Ransomware


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.