JohnyCryptor Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 153 |
| First Seen: | May 26, 2016 |
| Last Seen: | September 25, 2022 |
| OS(es) Affected: | Windows |
The JohnyCryptor Ransomware is an encryption ransomware Trojan that poses a real threat to computer users. The JohnyCryptor Ransomware encrypts the victim's files, replacing their extensions with an identification number and an AOL email for the JohnyCryptor Ransomware. The files encrypted by the JohnyCryptor Ransomware cannot be decrypted without access to the decryption key. Unfortunately, this is how the JohnyCryptor Ransomware operates, holding the victim hostage by withholding the decryption key until the victim pays a ransom of several hundred dollars. The JohnyCryptor Ransomware ransom is paid through BitCoins.
The best way to recover from a the JohnyCryptor Ransomware attack is to erase the contents of the infected hard drive and restore it from a backup. If this is not possible, some computer users have found limited success by using decryption utilities. However, computer users may not be able to recover their files without the decryption key or a backup copy. Computer users should avoid paying the JohnyCryptor Ransomware's ransom since this allows con artists to continue creating these attacks. A reliable backup solution will cost a fraction of what it would recover from these attacks.
Table of Contents
How the JohnyCryptor Ransomware may Invade Your Computer
The JohnyCryptor Ransomware is distributed using methods commonly seen in threat attacks, mainly corrupted spam email attachments and links. The JohnyCryptor Ransomware can be distributed through attack websites and file sharing networks, included inside popular Torrents. Once the victim is exposed to one of these infection sources, the JohnyCryptor Ransomware infects the victim's computer and begin encrypting the victim's files. The best way to prevent these attacks is to ensure that your computer is protected with a reliable security application that is fully up-to-date. Computer users should avoid file sharing networks and opening unsolicited email messages, attachments, and embedded links to prevent the JohnyCryptor Ransomware from being installed.
Unraveling the JohnyCryptor Ransomware Attack
Once the JohnyCryptor Ransomware has entered a computer, it begins encrypting the victim's files. The JohnyCryptor Ransomware scans the victim's drives for files that have certain file extensions. Common file types that the JohnyCryptor Ransomware and other encryption ransomware Trojans tend to target in their attacks include:
.sql, .mp4, .7z, .rar, .m4a, .wma, .avi, .wmv, .csv, .d3dbsp, .zip, .sie, .sum, .ibank, .t13, .t12, .qdf, .gdb, .tax, .pkpass, .bc6, .bc7, .bkp, .qic, .bkf, .sidn, .sidd, .mddata, .itl, .itdb, .icxs, .hvpl, .hplg, .hkdb, .mdbackup, .syncdb, .gho, .cas, .svg, .map, .wmo, .itm, .sb, .fos, .mov, .vdf, .ztmp, .sis, .sid, .ncf, .menu, .layout, .dmp, .blob, .esm, .vcf, .vtf, .dazip, .fpk, .mlx, .kf, .iwd, .vpk, .tor, .psk, .rim, .w3x, .fsh, .ntl, .arch00, .lvl, .snx, .cfr, .ff, .vpp_pc, .lrf, .m2, .mcmeta, .vfs0, .mpqge, .kdb, .db0, .dba, .rofl, .hkx, .bar, .upk, .das, .iwi, .litemod, .asset, .forge, .ltx, .bsa, .apk, .re4, .sav, .lbf, .slm, .bik, .epk, .rgss3a, .pak, .big, wallet, .wotreplay, .xxx, .desc, .py, .m3u, .flv, .js, .css, .rb, .png, .jpeg, .txt, .p7c, .p7b, .p12, .pfx, .pem, .crt, .cer, .der, .x3f, .srw, .pef, .ptx, .r3d, .rw2, .rwl, .raw, .raf, .orf, .nrw, .mrwref, .mef, .erf, .kdc, .dcr, .cr2, .crw, .bay, .sr2, .srf, .arw, .3fr, .dng, .jpe, .jpg, .cdr, .indd, .ai, .eps, .pdf, .pdd, .psd, .dbf, .mdf, .wb2, .rtf, .wpd, .dxg, .xf, .dwg, .pst, .accdb, .mdb, .pptm, .pptx, .ppt, .xlk, .xlsb, .xlsm, .xlsx, .xls, .wps, .docm, .docx, .doc, .odb, .odc, .odm, .odp, .ods, .odt.
After encrypting the victim's files, the JohnyCryptor Ransomware drops ransom notes to alert the victim of the attack. These files tend to take the form of HTML and TXT files dropped in directories where the JohnyCryptor Ransomware has encrypted files. The JohnyCryptor Ransomware also appends an email address and a numeric identifier to each file that was encrypted, prompting computer users to email this address for further information. The JohnyCryptor Ransomware's ransom notes contain information on how to pay the JohnyCryptor Ransomware's ransom and how to connect the Dark Web and purchase BitCoins to do this.
SpyHunter Detects & Remove JohnyCryptor Ransomware
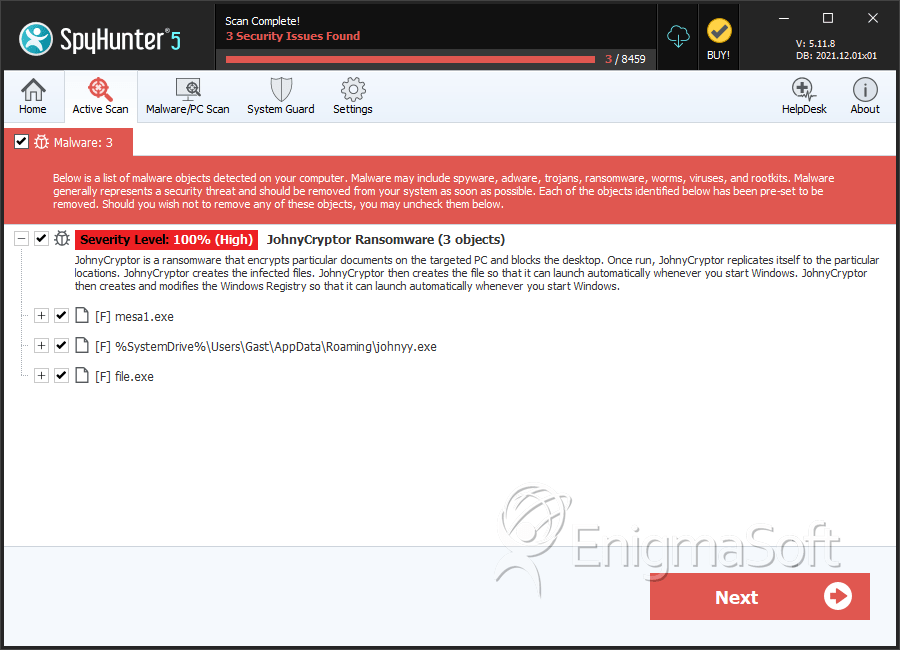
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | johnyy.exe | 493b260b3d1745fa1b1ec06dbd974ea7 | 48 |
| 2. | mesa1.exe | 53186427569d79d1bbf778d77247a215 | 15 |
| 3. | johnyy.exe | 085a912877be08593adfec50b7ba64b6 | 15 |
| 4. | johnyy.exe | 5740a96cf29d42cf951348e5c9fc9cb6 | 12 |
| 5. | johnyy.exe | 7896a94260e61c4612b1aec41c820328 | 8 |
| 6. | johnyy.exe | b70e6b993b77150a5a35d949333ac4cf | 5 |
| 7. | file.exe | 423c414fe65718b47ad191d018a3e0a0 | 0 |

