Green_Ray Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 77 |
| First Seen: | May 31, 2016 |
| OS(es) Affected: | Windows |
The Green_Ray Ransomware is a clone of the Mahasaraswati and the JohnyCryptor Ransomware. PC security analysts have determined that the Green_Ray Ransomware is designed to force inexperienced computer users into paying a ransom to recover their files. The Green_Ray Ransomware takes the victim's files hostage by encrypting them using an advanced encryption method. The Green_Ray Ransomware seems to target computer users in India and has an india.com email address, like the other ransomware Trojans that have been associated with this particular group. The Green_Ray Ransomware's ransom note is particularly short, just as with its clones. A simple message instructs the victim to contact the con artists operating the Green_Ray Ransomware at a particular email address. PC security analysts strongly advise computer users to avoid paying the Green_Ray Ransomware's ransom, since there is no guarantee that these people will restore the victim's files. Instead, they should restore files encrypted by the Green_Ray Ransomware from a backup location.
Table of Contents
How the Green_Ray Ransomware and Similar Threats may Attack Your Computer
The Green_Ray Ransomware's harmful executable file may be spread via spam email attachments, although these threats can be delivered through any number of typical delivery methods. When the Green_Ray Ransomware enters a computer, it changes the computer's settings to ensure that the Green_Ray Ransomware runs automatically when the affected computer starts up. The Green_Ray Ransomware encrypts the victim's files, deletes the Shadow Volume Copies of any encrypted file, and drops ransom notes in the form of text files on directories where the files were encrypted. The Green_Ray Ransomware also changes the affected computer's Desktop wallpaper image to display its ransom note. The text files the Green_Ray Ransomware drops are named 'How to decrypt your files.txt,' containing the following text over a colorful landscape:
To decrypt your data write me to the Green_Ray@india.com
After contacting the email address in the ransom note, PC security analysts observed the following response:
Good morning, dear friend!
We are writing to inform you that our team of network security specialists has analyzed your system and has identified vulnerabilities in the protection.
We kindly draw your attention that defensive operation on your computer is not running properly and now the whole database is at risk.
All your files are encrypted and can not be accepted back without our professional help.
Obviously vulnerability analysis, troubleshooting, decoding the information and then ensuring safety are not a simple matter.
And so our high-grade and quick service is not free.
Please note that today the price of your files recovery is 3 Bitcoins, but next day it will cost 5 Bitcoins.
You should buy bitcoins here https://localbitcoins.com/faq
Read the paragraphs:
1. How to buy Bitcoins?
2. How do I send Bitcoins and how can I pay with Bitcoins after buying them?
The Bitcoin wallet for payment is 1DGMeKSALSkYGkedYDUgcvV8mP77WEGusQ
After the transfer of bitcoins please send email with screenshot of the payment page.
We does not advise you to lose time, because the price will encrese with each passing day.
As proof of our desire and readiness to help you, we can decipher a few of your files for test.
To check this you can upload any encrypted file on web site dropmefiles.com, size no more than 10 MB (only text file or a photo) and send us a download link.
Certainly after payment we guarantee prompt solution of the problem, decrypt the database to return to its former condition and consultation how to secure the rules of the system safety.
Kind regards, Green Ray
Note that the message claims that the people behind the Green_Ray Ransomware attack pretend to be helping you protect your computer. The Green_Ray Ransomware attacks force computer users to pay a ransom that is high when compared to other, similar threats.
Dealing with the Green_Ray Ransomware and Similar Threats
It may not be possible currently to decrypt files encrypted by the Green_Ray Ransomware without access to the decryption key. Because of this, it will be necessary for computer users to restore these files from a backup location. Malware analysts advise computer users to disconnect a computer infected with the Green_Ray Ransomware from the Internet or network immediately to prevent the Green_Ray Ransomware infection from spreading within a network. The use of a reliable security program that is fully up-to-date and standard backup procedures can help make computer users impervious to the Green_Ray Ransomware and similar attacks.
SpyHunter Detects & Remove Green_Ray Ransomware
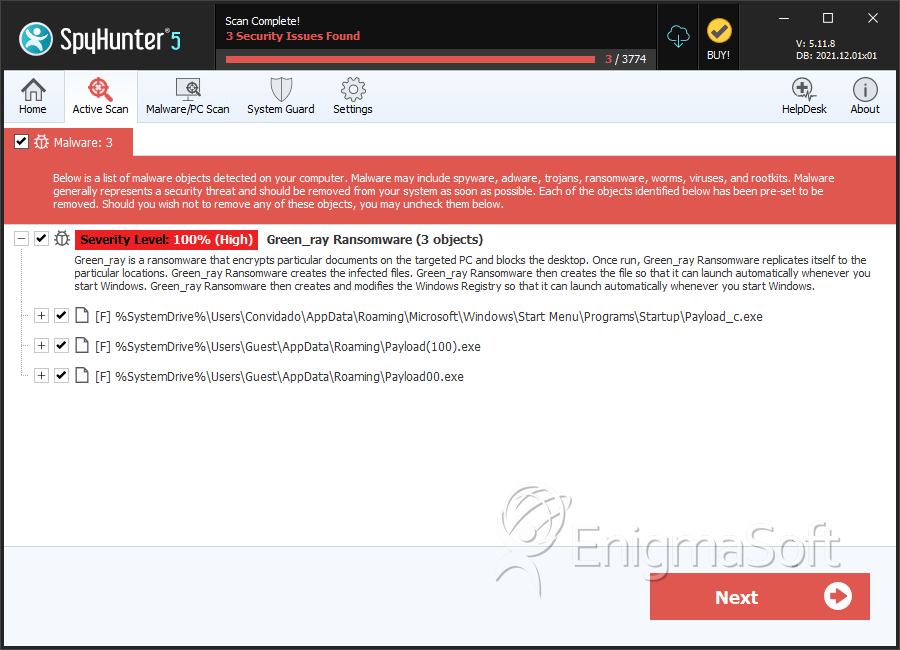
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | Payload_c.exe | 2245551ce293e2c6967786b91710a52b | 45 |
| 2. | Payload(100).exe | df7a135cf879b755eafff7cb12cf5f36 | 16 |
| 3. | Payload00.exe | c4f355599f71d98f49a377c5fec2d909 | 16 |

