'.ecc File Extension' Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 6 |
| First Seen: | January 20, 2016 |
| Last Seen: | August 30, 2022 |
| OS(es) Affected: | Windows |
The '.ecc File Extension' Ransomware is a variant of the TeslaCrypt infection. This threat, which has been active since early 2015, has recently released its newest version, TeslaCrypt 3.0. This version fixes a loophole that had previously allowed malware researchers to recover decryption keys directly from the threat, preventing con artists from monetizing these attacks effectively. In late 2015, PC security researchers spotted a rise in infections such as the '.ecc File Extension' Ransomware, which were essentially TeslaCrypt variants that change the affected files' extensions to different extensions (in this case, to the ECC extension). This increase in TeslaCrypt variant attacks is surely related to the rise in RaaS (Ransomware as a Service), which was recently being offered along with this infection.
The Similarities Between the '.ecc File Extension' Ransomware and TeslaCrypt
The '.ecc File Extension' Ransomware and other TeslaCrypt variants use AES encryption to encrypt the victim's files. They demand the payment of a ransom by changing the victim's Desktop image and also by dropping numerous text or HTML files with payment instructions on the victim's computer. The '.ecc File Extension' Ransomware and other TeslaCrypt variants are set apart from other ransomware threats in that they also may target video game files, particularly saved files for popular games that may amount to a significant time investment on the part of computer users.
There are numerous other differences between new TeslaCrypt variants such as the '.ecc File Extension' Ransomware and their predecessors. The '.ecc File Extension' Ransomware now allows victims to pay ransoms using PayPal My Cash cards rather than limiting payment to BitCoins. However, instead of demanding the $500 USD ransom associated with BitCoin, they demand a $1000 USD ransom if this payment method is used. It is not possible to recover the decryption key using utilities developed for this by malware researchers, which makes it difficult to recover from a '.ecc File Extension' Ransomware attack.
The following are the file extensions that are targeted by the '.ecc File Extension' Ransomware and the other, newer TeslaCrypt variants:
.7z; .rar; .m4a; .wma; .avi; .wmv; .csv; .d3dbsp; .sc2save; .sie; .sum; .ibank; .t13; .t12; .qdf; .gdb; .tax; .pkpass; .bc6; .bc7; .bkp; .qic; .bkf; .sidn; .sidd; .mddata; .itl; .itdb; .icxs; .hvpl; .hplg; .hkdb; .mdbackup; .syncdb; .gho; .cas; .svg; .map; .wmo; .itm; .sb; .fos; .mcgame; .vdf; .ztmp; .sis; .sid; .ncf; .menu; .layout; .dmp; .blob; .esm; .001; .vtf; .dazip; .fpk; .mlx; .kf; .iwd; .vpk; .tor; .psk; .rim; .w3x; .fsh; .ntl; .arch00; .lvl; .snx; .cfr; .ff; .vpp_pc; .lrf; .m2; .mcmeta; .vfs0; .mpqge; .kdb; .db0; .DayZProfile; .rofl; .hkx; .bar; .upk; .das; .iwi; .litemod; .asset; .forge; .ltx; .bsa; .apk; .re4; .sav; .lbf; .slm; .bik; .epk; .rgss3a; .pak; .big; .unity3d; .wotreplay; .xxx; .desc; .py; .m3u; .flv; .js; .css; .rb; .png; .jpeg; .txt; .p7c; .p7b; .p12; .pfx; .pem; .crt; .cer; .der; .x3f; .srw; .pef; .ptx; .r3d; .rw2; .rwl; .raw; .raf; .orf; .nrw; .mrwref; .mef; .erf; .kdc; .dcr; .cr2; .crw; .bay; .sr2; .srf; .arw; .3fr; .dng; .jpe; .jpg; .cdr; .indd; .ai; .eps; .pdf; .pdd; .psd; .dbfv; .mdf; .wb2; .rtf; .wpd; .dxg; .xf; .dwg; .pst; .accdb; .mdb; .pptm; .pptx; .ppt; .xlk; .xlsb; .xlsm; .xlsx; .xls; .wps; .docm; .docx; .doc; .odb; .odc; .odm; .odp; .ods; .odt
As can be seen in the above list, the '.ecc File Extension' Ransomware will target files associated with popular games including Minecraft, StarCraft 2, and League of Legend, making the games p[resent malfunctions until the files have been restored. The '.ecc File Extension' Ransomware will delete Shadow Volume copies of the files it encrypts as well as prevent computer users from using System Restore or other methods to recover their files. Because of this, the best method of dealing with the '.ecc File Extension' Ransomware is prevention, making sure that it does not enter a computer and that all files are backed up using an external device or the cloud. That way, the '.ecc File Extension' Ransomware infections can be treated effectively by wiping the infected hard drive and restoring the affected files from the backup.
SpyHunter Detects & Remove '.ecc File Extension' Ransomware
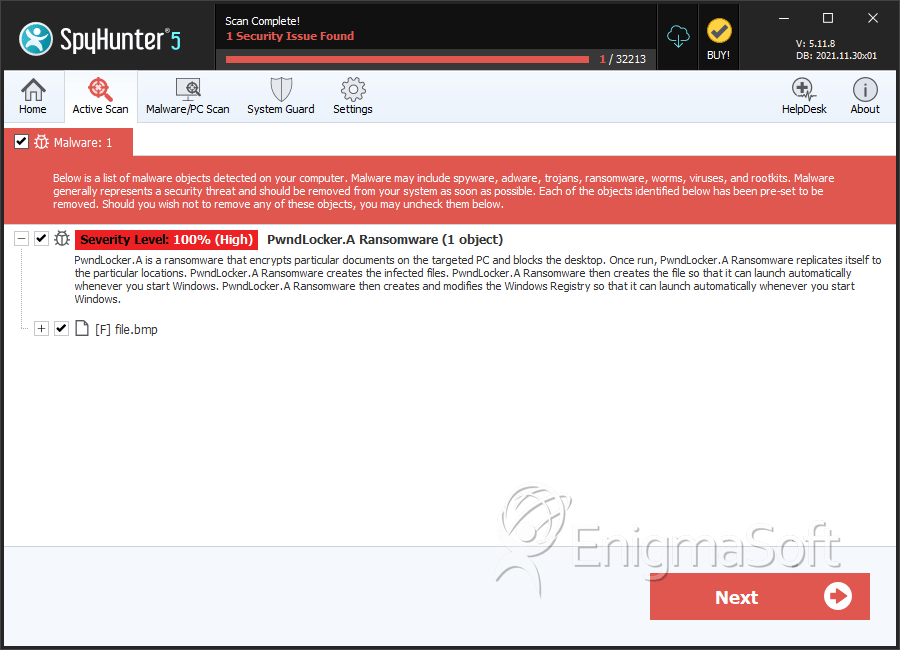
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.bmp | c579341f86f7e962719c7113943bb6e4 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.