CryptoLocker Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 22,569 |
| Threat Level: | 100 % (High) |
| Infected Computers: | 763 |
| First Seen: | September 11, 2013 |
| Last Seen: | October 24, 2025 |
| OS(es) Affected: | Windows |
CryptoLocker Ransomware Image
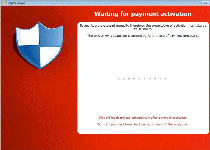
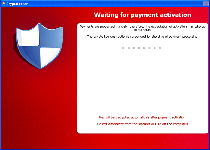
The CryptoLocker Trojan is a ransomware infection that encrypts the victim's files. CryptoLocker may typically be installed by another threat such as a Trojan downloader or a worm. Once CryptoLocker is installed, CryptoLocker will search for sensitive files on the victim's computer and encrypt them. Essentially, CryptoLocker takes the infected computer hostage by preventing access to any of the computer user's files. CryptoLocker then demands payment of a ransom to decrypt the infected files. CryptoLocker is quite harmful, and ESG security analysts strongly advise computer users to use an efficient, proven and updated anti-malware program to protect their computer from these types of infections.
Table of Contents
The Outrageous Fee Asked by CryptoLocker
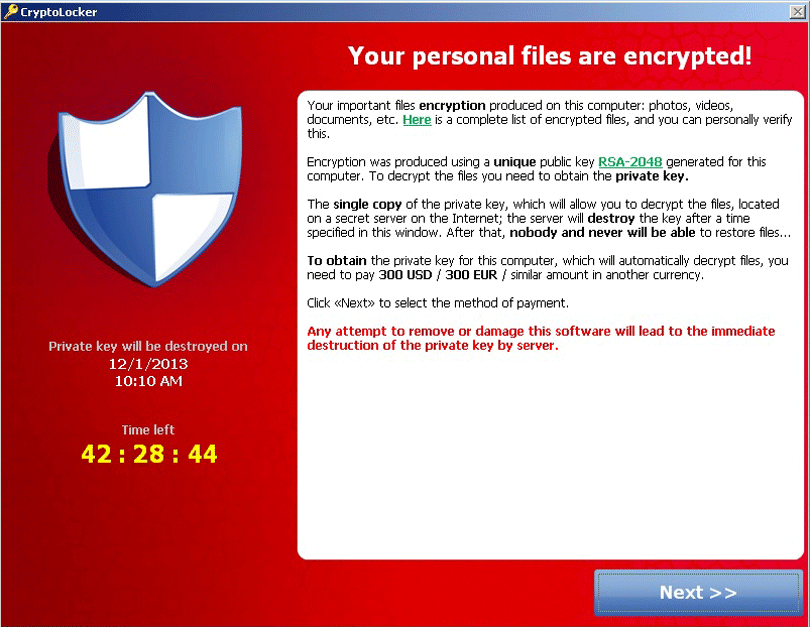
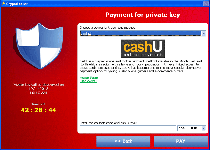
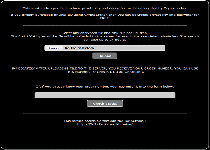
CryptoLocker displays an alarming message when the infected computer starts up. This message demands payment of 100 USD or Euro in order to decrypt the infected files. CryptoLocker also claims that attempting to remove CryptoLocker may result in the victim's files being locked forever. The CryptoLocker ransom message reads as follows:
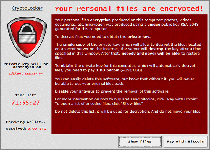
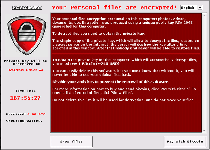
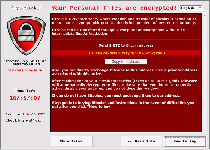
'Your personal files are encrypted!
Your important files encryption produced on this computer: photos, videos, document, etc. Here is a complete list of encrypted files, and you can personally verify this…
To obtain the private key for this computer, which will automatically decrypt files, you need to pay 100 USD / 100EUR / similar amount in another currency.'
To scare inexperienced computer users so that they will not take action to remove CryptoLocker, the ransom message continues by stating the following:
'Any attempt to remove or damage this software will lead to immediate destruction of the private key server.'
Why Paying CryptoLocker’s Ransom is not Going to Help Your PC
There are several reasons why you should not pay CryptoLocker's ransom. You can see below some of them:
- There is no guarantee that paying CryptoLocker's ransom will decrypt your files.
- Paying this 'fee' will support malware developers, allowing them to create additional malicious content and target other computer users.
- Taking steps to remove CryptoLocker with a legitimate security program will not actually endanger your files or prevent you from decrypting them.
In several situations, it may be needed to use an additional decryption utility to restore your files to normal, usually from an external memory device. However, the best way to restore your files is to have a back-up at hand, a good security practice for all computer users.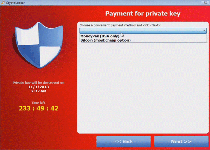




Aliases
12 security vendors flagged this file as malicious.
| Antivirus Vendor | Detection |
|---|---|
| AVG | Inject2.BWZN |
| Fortinet | W32/Bitman.FO!tr |
| Ikarus | Trojan.Win32.Injector |
| McAfee | Artemis!E78654D43FCF |
| Microsoft | Ransom:Win32/Tescrypt.A |
| Antiy-AVL | Trojan[Ransom]/Win32.Bitman |
| Sophos | Troj/Ransom-AST |
| Comodo | TrojWare.Win32.Ransom.Bitman.~NS |
| Kaspersky | Trojan-Ransom.Win32.Bitman.fo |
| Avast | Win32:Malware-gen |
| Symantec | Trojan.Gen |
| K7AntiVirus | Trojan ( 004bc9ff1 ) |
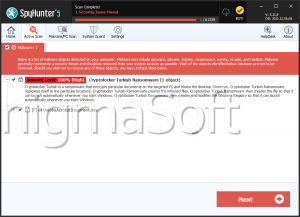
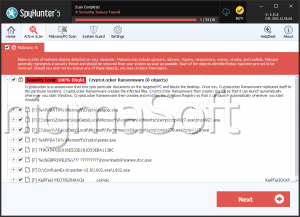
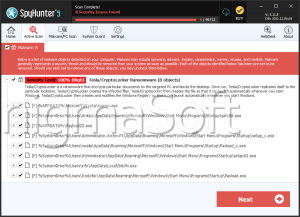
SpyHunter Detects & Remove CryptoLocker Ransomware
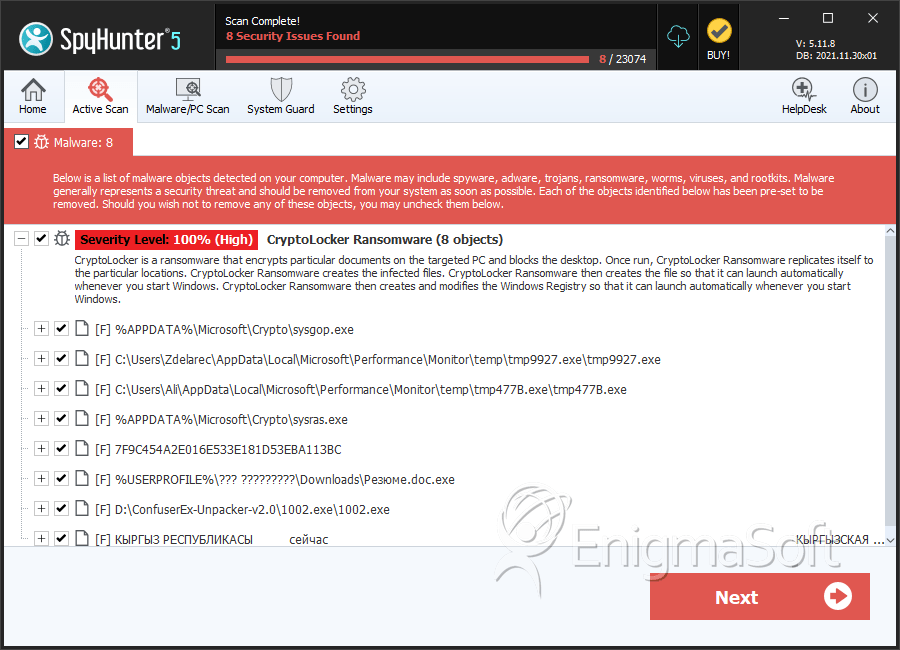
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | sysgop.exe | 3c282af747b4f70340dca3170d55ae29 | 247 |
| 2. | tmp9927.exe | eb2cde846127106689d14afe7911bcec | 153 |
| 3. | tmp477B.exe | 1b21b27589ddc173ba795213e108a096 | 39 |
| 4. | sysras.exe | 881f86bf4bb4b9f0e993b2853a0a27cf | 36 |
| 5. | d765e722e295969c0a5c2d90f549db8b89ab617900bf4698db41c7cdad993bb9 | 04fb36199787f2e3e2135611a38321eb | 20 |
| 6. | 1002.exe | 829dde7015c32d7d77d8128665390dab | 15 |
| 7. | 7F9C454A2E016E533E181D53EBA113BC | 7f9c454a2e016e533e181d53eba113bc | 14 |
| 8. | Резюме.doc.exe | 12303bbfe7194fd4f0070cd4d1005209 | 8 |
| 9. | КЫРГЫЗ РЕСПУБЛИКАСЫ сейчас КЫРГЫЗСКАЯ РЕСПУБЛИКА.docx.exe | acf9873c86e35b9bee0db158befe8163 | 7 |
| 10. | $R803NKR.exe | b8ebbc2a6001ff318e49e0ec679c185f | 6 |
| 11. | план части.docx.exe | bac4daf1ba563a5fdd01691441cedc9b | 6 |
| 12. | сопроводительное в прокуратуру.docx.exe | b51d416995590c6a35a0602cfd2df94d | 2 |
| 13. | Министерство образования и науки Кыргызской Республики.docx.exe | a686e81153a11ea2817ecf58a9b0b25d | 1 |
| 14. | Министерство образования и науки Кыргызской Республики1.docx.exe | 5bcb809524857f26a89ac67ffc80f6f5 | 1 |
| 15. | PROGRAMPEMBELAJARANKELAS4.docx.exe | 7c87cdad5223b0ac9e1a5e2e5cc0d20f | 1 |
| 16. | رزمايش.docx.exe | 64cc41e5aa1d5b34e6c49cbd9ffe9233 | 1 |
| 17. | Testing Draft 2.docx.exe | 9406c8ea0f180383d3a8d5fedb105bb1 | 1 |
| 18. | 3.DAFTAR-LAMPIRAN--wahabkhoter.blogspot.com.docx.exe | 85242fee40a9a0bc3ce6c20f52050643 | 1 |
| 19. | RPPTematikBerkarakterKelas1SDPengalamansms1.docx.exe | 14434f09c026e189161254a3230523e9 | 1 |
| 20. | Списывание.docx.exe | b870f4a3f292452971628fcb54d9067e | 1 |
| 21. | Инструкция как скачать чит и ссылка на него.docx.exe | 860bfffc08296bd13d43bef865b33f76 | 1 |
| 22. | Тесты по модулю Пищеварительная система для студентов 2-курса факультета лечебное дело.docx.exe | 49115ff6fe4016169c24ff3783010321 | 1 |
| 23. | Выписка из Протокола.docx.exe | 06dbb0786866ec652b12ddfcc204a735 | 1 |
| 24. | %UserProfile%\[RANDOM CHARACTERS]\[RANDOM CHARACTERS].exe | ||
| 25. | %UserProfile%\[RANDOM CHARACTERS].exe | ||
| 26. | eb5eb336636e3f6cacf6c8db6bf4ea00 | eb5eb336636e3f6cacf6c8db6bf4ea00 | 0 |