CTB-Locker (Critoni) Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 1,565 |
| First Seen: | July 22, 2014 |
| Last Seen: | June 8, 2022 |
| OS(es) Affected: | Windows |
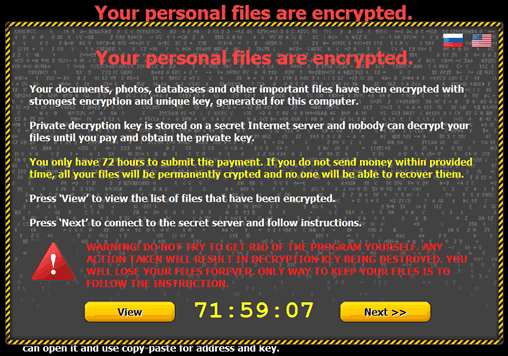
CTB-Locker (Critoni) Ransomware Image
The Critoni Ransomware (also known as CTB-Locker or Curve-Tor-Bitcoin Locker) is a file encryptor Trojan that uses the Tor browser to obfuscate its network activity with its Command & Control servers. While the Critoni Ransomware's technical innovations are noteworthy, for its victims, the Critoni Ransomware endangers their files in much the same ways as other ransomware, with a demanded payment for file restoration. Proper data backup strategies can mitigate the effects of a Critoni Ransomware attack, and anti-malware tools should be used to delete the Critoni Ransomware, and all related threats, as soon as possible.
Table of Contents
What a Trojan’s Anonymity Means for You
The Critoni Ransomware is one of the various file encryption Trojans that may install themselves through software vulnerabilities leveraged in attacks, which tend to be implemented by Web-based threats like the Angler Exploit Kit. Just like the Critoni Ransomware's installation rarely requires any consent from its victims, its attacks also take place automatically, targeting and encrypting specific file types on your PC. Documents, images and audio files all may be made unreadable, with the Critoni Ransomware's warning TXT files claiming the use of a nigh-unbreakable elliptic curve formula in the process.
Along with asking its victims for a Tor-based payment plan to return their files to them, the Critoni Ransomware also initiates communications with a C&C server. This function could let the Critoni Ransomware receive instructions for other attacks or transmit information. The Trojan implements this feature in a semi-innovative fashion, by using Tor to prove anonymity to the C&C servers, as well. Other threats have pioneered that technique, including banking Trojans, but malware experts have yet to see any other file encrypting Trojans using the Critoni Ransomware's anonymity methodology.
In practice, this anonymity could make it more difficult for PC security researchers to disrupt the Critoni Ransomware's server infrastructure, or assist law enforcement with apprehending the Critoni Ransomware's administrators. The Critoni Ransomware's admins are not necessarily the same individuals as its coders; the Critoni Ransomware has been seen being sold to third parties on suspicious forums for sums of three thousand USD.
Getting Your Files Off of Critoni Ransomware’s Curve
While the Critoni Ransomware does boast of an exceptionally strong encryption algorithm that would make decryption difficult, there are other means of preserving your files from a file encryptor Trojan's attacks. For these reasons, malware researchers always recommend that PC users with irreplaceable data use remote file backups in conjunction with removable hard drives, cloud services, and similar storage options.
Deleting the Critoni Ransomware, itself, always should be done by dedicated anti-malware software. The Critoni Ransomware continues to be in active development and may be used by third parties with a variety of infection strategies, which may use variable, third-party threats. Accordingly, your anti-malware tools should be updated for detecting the latest threats while scanning for the Critoni Ransomware. Although the Critoni Ransomware does include a self-deletion function for unpaid ransom scenarios, victims shouldn't hope for this capability to trigger and disinfect their PCs.
Unlike some, more limited file encryptors, the Critoni Ransomware also may attack PCs that lack active Internet connections. While the Critoni Ransomware has been given visibility in news headlines for its novel C&C server communications, these communications don't appear to be mandatory for carrying out its payload.
Infection rates for CTB-Locker are increasing at alarming rates. We have found where the method of CTB-Locker encrypting files will ultimately make those files useless and they cannot be decrypted by any method, even by paying the fine through the offered payment via CTB-Locker's lock screen.
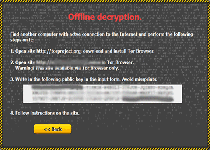
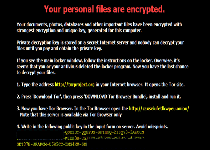
Aliases
15 security vendors flagged this file as malicious.
| Anti-Virus Software | Detection |
|---|---|
| AVG | Inject2.BJOA |
| Fortinet | W32/Filecoder.EB!tr |
| AhnLab-V3 | Trojan/Win32.Necurs |
| Antiy-AVL | Trojan/Win32.Inject |
| Sophos | Mal/Wonton-AF |
| McAfee-GW-Edition | BehavesLike.Win32.PWSZbot.fh |
| DrWeb | Trojan.Encoder.853 |
| Comodo | TrojWare.Win32.Amtar.amu |
| Kaspersky | Trojan.Win32.Inject.ttcq |
| Avast | Win32:Injector-CLC [Trj] |
| K7AntiVirus | Trojan ( 004b31fd1 ) |
| McAfee | RDN/Generic.dx!dhv |
| CAT-QuickHeal | TrojanRansom.Crowti.A4 |
| AVG | Crypt3.BTGZ |
| Ikarus | Trojan-Ransom.CTBLocker |
SpyHunter Detects & Remove CTB-Locker (Critoni) Ransomware
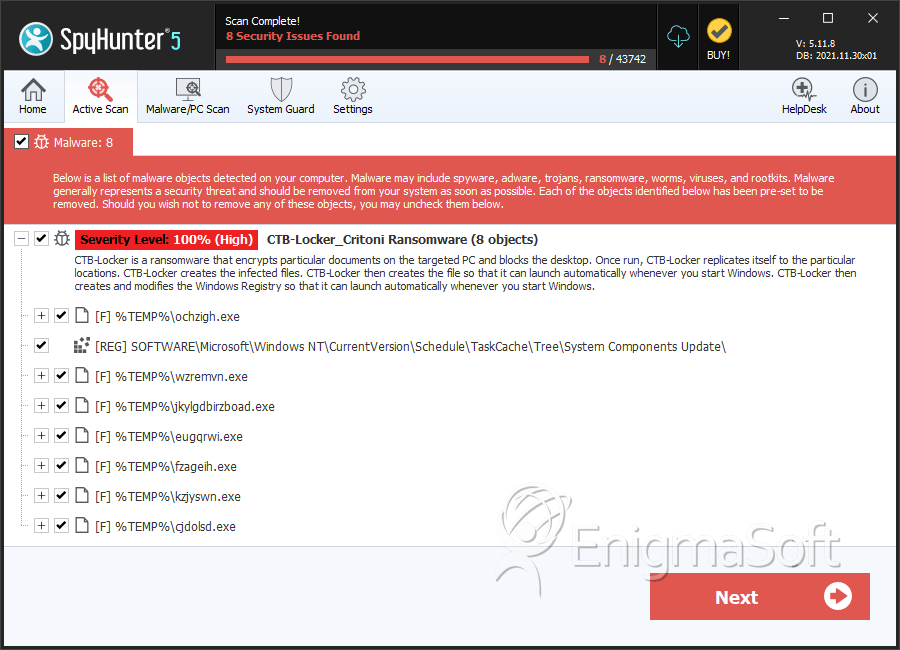
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | jkylgdbirzboad.exe | 015fb9d19a20ba42e5c3b758668d4563 | 3 |
| 2. | ygehnnol.exe | 7027a7ee4fbcb26f1d039035ebd0dca5 | 1 |
| 3. | ljchyff.exe | 7aaa4bd1c2ca44174f17f06deb6221ff | 1 |
| 4. | %MyDocuments%\DecryptAllFiles [USER ID].txt | ||
| 5. | %MyDocuments%\AllFilesAreLocked [USER ID].bmp | ||
| 6. | %MyDocuments%\[RANDOM].html | ||
| 7. | %WinDir%\Tasks\[RANDOM].job | ||
| 8. | %Temp%\[RANDOM].exe | ||
| 9. | C:\[RANDOM]\[RANDOM].exe | ||
| 10. |
C:\Users\ |
||
| 11. |
C:\Documents and Settings\ |
||
| 12. |
C:\Documents and Settings\ |
||
| 13. | file.exe | dbfd1e73c20bf46c5dfa8ff399c7db81 | 0 |
| 14. | file.exe | 4b4544e54740217f4a6248d49d8490d5 | 0 |
| 15. | file.exe | d00ac2f06a3e276e60434a1b27394650 | 0 |
| 16. | file.exe | 5f71e11d485585d217c2249ce951885e | 0 |
| 17. | file.exe | 8fa0c20cbf3b8794cc17bddf96293e25 | 0 |
| 18. | file.exe | c30465dc68a9a0b946b574d14b479825 | 0 |
| 19. | file.exe | 9447d03e39cb44c898223fcd8fb61bce | 0 |
| 20. | file.exe | dfeb332cf1ded1ea0fc0761a3efe57fc | 0 |
| 21. | file.exe | 3f50be0bf26bec263aa64d3d942e8d01 | 0 |
| 22. | file.exe | 23b6aeafd2e7d7657aa6d05afff9c05a | 0 |
| 23. | file.exe | 6661df9d8474b751137202aa99cecdf4 | 0 |
| 24. | file.exe | 050ddfc1ddc6e2e886272f6d254fe402 | 0 |
| 25. | file.exe | b980669fd31acb318843e3f129850195 | 0 |
| 26. | file.exe | 842046f89835d9f194888acf0320cfba | 0 |
| 27. | file.exe | b7d2dbaccf3cd340ec97b03a091fc317 | 0 |
| 28. | file.exe | 9b733b8ff609f3086e4d5dc36454c357 | 0 |
| 29. | file.exe | c25908f6868cd919e27d7728f4e8098f | 0 |
| 30. | file.exe | e6bc67775d6e72f06f555901fb7b47ca | 0 |
| 31. | file.exe | 577a9bb823b4f46cce4e7f1481f77daf | 0 |
| 32. | file.exe | 376565a2294e80daf16776e594bf3f48 | 0 |
| 33. | file.exe | 8d7bfb9738e67f99a90dd9053f43b375 | 0 |
| 34. | file.exe | 34aff4a9ed8761696559e62352af9fea | 0 |
| 35. | file.exe | a65a63148e6f7b11eddb8f54a7fb58a5 | 0 |

